14 - 20 June 2023
(Issue 24)
is sponsored by

Readers who encounter problems with the email version of this newsletter can
view the latest web edition here.
CONTENTS
Section I - CURRENT INTELLIGENCE NEWS HIGHLIGHTS
- Turkey’s new intelligence chief hides past affiliation with Iran’s mullah regime - Nordic Monitor, 15 Jun 23
- Russian embassy: Australia blocks new Canberra site over spying risk - BBC, 15 Jun 23
- Russian intelligence agencies given more resources, importance under Putin - Sky News, 15 Jun 23
- The U.S. Military Could Someday Use Microbes as Tiny Spies - Popular Mechanics, 16 Jun 23
- Why China’s new spying law has foreign firms scratching their heads, scrambling like a ‘scared monkey’ - South China Morning Post, 17 Jun 23
- Announcing the Center for the Study of Intelligence and Nontraditional Warfare - Foreign Policy Research Institute, 16 Jun 23
- University shuts down its CCP-linked Confucius Institute after scrutiny from top Republican - Daily Mail, 16 Jun 23
- ODNI releases commercially available information report - Intelligence Community News, 15 Jun 23
- US intelligence looks to ‘anonymize conversational speech’ recorded by IoT devices in real-time - The Sociable, 13 Jun 23
- Senate Select Committee on Intelligence Passes Intel Act, Including Security Clearance and Classification Reform - Clearance Jobs, 15 Jun 23
- How much do you know about the Intelligence Identities Protection Act? - Clearance Jobs, 13 Jun 23
- Intelligence analysts confront the reality of deepfakes - Space News, 16 Jun 23
- Super spy or paper pusher? How Putin’s KGB years in East Germany helped shape him - Los Angeles Times, 15 Jun 23
- Counterespionage Corner - A collection of recent material on arrests, convictions, expulsions, and more...
- Cyberespionage Collection - Newly identified actors and operations, countermeasures, policy, other...
Section II - REGULARLY FEATURED PODCASTS, BROADCASTS, NEWSLETTERS
- “Spies: The Epic Intelligence War Between East vs. West” – with Calder Walton — Andrew Hammond, PhD. SpyCast
- Putin is prioritizing control over efficiency, and it’s not going to serve him well in the long run. — Former Acting CIA Dep. Dir. for Ops and Arkin Group President Jack Devine, In Other News
- Modi Visit and U.S.-India Partnership, UN Global CT Strategy to be Adopted, Global Terrorist Threat Evolves, Yemen Conflict Settlement Still Elusive, Ukraine Counteroffensive Drives Conflict's Future — Former FBI Special Agent and Soufan Group CEO Ali Soufan, Intel Brief
- Cyber Hacking Campaigns, Russia, Ukraine, Disinformation, The destruction of the Nova Khakovka Dam in Ukraine, 4 children stabbed in France: Terrorism?, and more... — WTOP National Security Correspondent JJ Green - Inside the SCIF, Target USA, The Hunt
- New Biden Nuclear Deal with Iran Threatens Kurds | Flipped: How Dan Ellsberg changed my life | All Quiet on the Miami Front - Jeff Stein and Colleagues in SpyTalk (Substack)
Section III - MEMBER CONTRIBUTIONS
- Article: CISA Order Highlights Persistent Risk at Network Edge - Krebs On Security, 15 Jun 23
- Article: EXCLUSIVE: Chinese Intel Arm Quietly Operates ‘Service Centers’ In 7 US Cities - Daily Caller, 17 Jun 23
- Video: The Most Dangerous Spy of WW2 - The Limping Lady | True Life Spy Stories (41 mins) - Philip Thompson via YouTube, March 2023
- Article: The US Navy, NATO, and NASA are using a shady Chinese company’s encryption chips - Ars Technica, 16 Jun 23
- Article: China's efforts to catch up in global electronic spying race - Reuters, 13 Jun 23
- Article: Snowden Ten Years Later - Schneier on Security, 06 Jun 23
- Article: FBI pleads to keep FISA spy powers despite concerns over growing abuses - Washington Times, 13 Jun 23
- Article: Senators press Biden to release U.S. intel analysis of Chinese spy balloon incident - Washington Times, 16 Jun 23
- Article: U.S. spies purchasing troves of Americans’ data is under review by intelligence community - Washington Times, 16 Jun 23
- Article: Russia Sought to Kill Defector in Florida - New York Times, 19 Jun 23
- Article: AI-Generated Steganography - Schneier on Security, 13 Jun 23
- Article: Vancouver's Chinese community is closely watched by Beijing - Le Monde, 18 Jun 23
Section IV - DEEPER DIVES, FILM, HISTORY, POP CULTURE
- Let’s Stop Pretending Spying Is a Big Deal - Foreign Policy, 14 Jun 23
- Using the Global Online Exchange to Enhance Cultural Intelligence in Future IC Workforces - Journal of Intelligence, Security, and Resilience Education (2023)
- We Need To Talk About the Espionage Act (46 mins) - The Lawfare Podcast, 15 Jun 23
- Aliens Or Not, Secret Crash Retrieval Programs Are A Very Real Thing - The Drive, 15 Jun 2023
- Infographic and Report: Interactive: Comparing Military Spending Around the World - Visual Capitalist, 04 Jun 23
- Intelligence in History - A Collection of Recent Content
- True Intelligence Matters in Film: M. Butterfly - David Cronenberg (1993)
- Walking Tours: The Spies of Embassy Row and Spies of Georgetown - Washington, DC. (Sundays, Dates/Times Vary)
Section V - Books, Research Requests, Academic Opportunities, Jobs, Obituaries
Books — Forthcoming, New Releases, Overlooked
- Spy Ships: One Hundred Years of Intelligence Collection by Ships and Submarines by Norman Polmar, Lee J. Mathers, and Rear Admiral Thomas A Brooks
- The Central Intelligence Agency and Overhead Reconnaissance: The U-2 and OXCART Programs, 1954-1974 by Gregory Pedlow and Donald Welzenbach
- OSINT Tools: A Practical Guide to Collection, Analysis, and Visualization by Paul Michel
Research Requests and Academic Opportunities
- Survey for Members: Skill Sets Needed for Intelligence Analysis Degree Holders to See Success After Graduation
- Call for Information: 430th CIC in Salzburg in 1946
- Call For Sources: Intelligence activities in Grenada and the southern Caribbean between 1979, Operation Urgent Fury, Leonard Barrett
- Call For Sources: Intelligence Officers Who Lived in Spain in the 1970s
- Call For Papers: Intelligence and Post-War Reconstruction - International Journal of Intelligence and Counterintelligence
- Call For Articles: AFIO Journal, The Intelligencer
- Retired Federal Government Employees Wanted - National Security Agency, Fort Meade, MD
- Assistant Professor - Intelligence Studies (Global Security and Intelligence Studies), Embry-Riddle Aeronautical University - Prescott, Arizona
- Teaching Associate - Intelligence and National Security Studies, Coastal Carolina University, Conway, South Carolina
- Thomas Glenn, Former NSA Executive
- Mary Stafford, Former Director of Admin for NGA's Predecessor
- 6 Jul 23 (Thursday), 1900 (Central) - Virtual - LTG Michael Groen, USMC, Ret. on Artificial Intelligence - San Antonio AFIO Chapter
- 27 Jul 23 (Thursday), 1130 (Pacific) - In Person, San Francisco - Col. Robert W. Parr, USAF (ret), on "12 Days with a Soviet Pilot Defector" - AFIO Andre LeGallo Chapter
Events from Advertisers, Corporate Sponsors, Others
- 21 Jun 23, 1200 (ET) Nino and the "Rogue Elephant": The Intelligence Career of Antonin Scalia with James Rosen – International Spy Museum - Virtual
- 27 Jun 23, 1400-1500 (ET) SPY with Me: Memory Loss Program – International Spy Museum - Virtual
- 29 Jun 23, 0900-0945 (ET) Coffee and Conversation with The Hon. Michael Vickers – INSA - Virtual
- 13-14 Jul 23 2023 Intelligence and Security Summit – AFCEA/INSA - In Person - National Harbor, MD
- 20-22 Jul 2023 NASIH Annual Conference 2023 – NASIH - In Person - University of Calgary, Canada
See the AFIO Calendar of Events for scheduling further in the future.
ACKNOWLEDGEMENTS
The WIN editors thank the following contributors of content for this issue:
EB, JK, LR, GR, S
Readers are encouraged to suggest material for any section of the WIN to:
winseditor@afio.com
The WIN editors thank the following contributors of content for this issue:
EB, JK, LR, GR, S
Readers are encouraged to suggest material for any section of the WIN to:
winseditor@afio.com
DISCLAIMER
Our editors include a wide range of articles and commentary in the Weekly Intelligence Notes to
inform and educate our readers. The views expressed in the articles are purely those of the authors and do not reflect support or endorsement from AFIO. WIN notices about non-AFIO events do not constitute endorsement or recommendation by AFIO.
AFIO does not vet or endorse research inquiries, career announcements, or job offers. We publish reasonable-sounding inquiries and career offerings as a service to our members. We encourage readers to exercise caution and good judgment when responding and to independently verify the source before supplying resumes, career data, or personal information.
TECHNICAL DIFFICULTIES
Readers who encounter problems with links or viewing this newsletter as an email can access
the latest web edition here.
the latest web edition here.
LATEST FROM AFIO
Released exclusively to members...13 June 2023
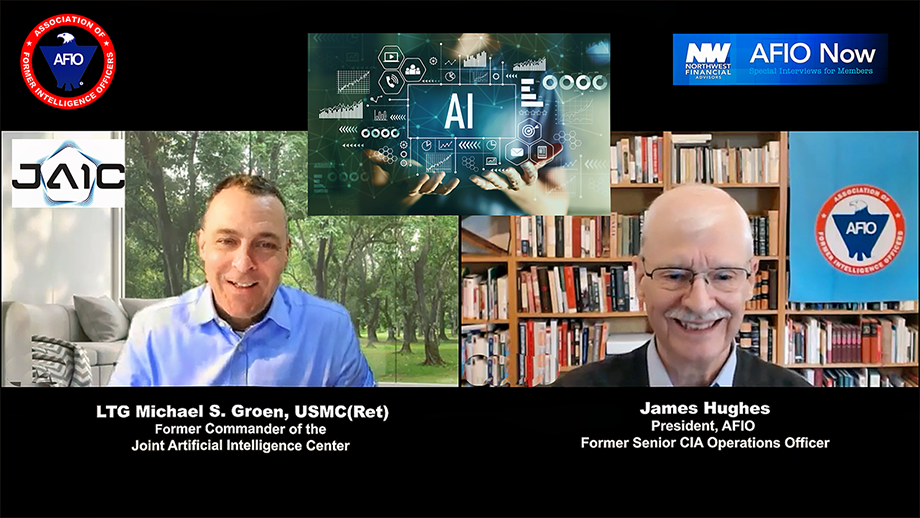
The Meaning, Uses, Adoption Problems, and Ethics of AI in the Military and Beyond
LTG Michael Groen USMC, Ret,
former Commander of the Joint Artificial Intelligence Center, on AI
Interview of Thursday, 4 May 2023 of LTG Michael Groen (USMC, Ret), former Commander of the Joint Artificial Intelligence Center, discussing AI. Host and Interviewer: James Hughes, AFIO President, a former Senior CIA Operations Officer.
TOPIC: General Groen and Jim Hughes discuss the Joint Artificial Intelligence Center, the meaning, uses, adoption problems, and ethics of AI in the military and beyond. Of special interest are what led General Groen to this career path. He provides inspiring comments about careers in the military and intelligence, the types of people and opportunities he found and enjoyed over an unexpectedly long career.
The interview runs 44 minutes and includes several Q&As.
Access the Groen interview here or click above image
This, and upcoming AFIO Now videos in 2023, are sponsored by Northwest Financial Advisors.
WORK AT AFIO
A few of the responsibilities include: • Serve as focal point for a major AFIO project, to include maintaining project database and supporting a large annual formal dinner • Provide back-up support to AFIO Directors of Membership and Operations • Support AFIO's existing partners and stakeholders ... Robust Microsoft Office Skills (Excel, Outlook, Word) required.
Full job description here.

"AFIO Now" Video Interviews and Podcasts in 2023 are sponsored by
Northwest Financial Advisors
Click here to watch interviews in the AFIO Now series released in 2023.
View interviews from 2020 to 2022 here.
Watch public-release interviews on our YouTube channel or listen to them in podcast form at the links below.
Log into the member-only area for member-only features.
The Real Life Impacts of Russian Oligarchs Being Welcomed into London and Then Becoming Problems as Putin Struck Out at Perceived Betrayers
Latest podcast episode: Alma Katsu, former NSA and CIA Officer, discussing her latest novel, "Red London"
Video and Podcast released to public 11 June 2023.
Alma Katsu and Jim Hughes discuss why she chose to write novels, the steps leading to Katsu's second novel in her semi-fiction series - Red London - which followed her highly-praised first in the series: Red Widow. The real life impacts of Russian Oligarchs being welcomed into London and then becoming problems as Putin struck out at perceived betrayers (his poisoning of defector Alexander Litvinenko and others with fatal doses of polonium-210). And then Putin's invasion of Ukraine. Also discussed is the demands upon authors as their books are prepared for films, television series, podcasts, and other formats. Katsu also describes her career experiences at NSA and CIA, and gives pointers to women considering careers in the Intelligence Community.
The interview runs 24 minutes and includes several Q&As.
Are you too busy to watch an entire AFIO Now episode on YouTube? Would you rather listen in your car or while accomplishing other tasks? You can download or stream episodes on any of the 8 podcasting platforms that host AFIO Now. Search for 'AFIO Podcast' for a selection of the interviews above (public released ones) on:
Podbean; iTunes; Google; Spotify; Amazon Music; Amazon TuneIn + Alexa; iHeartRadio; Pandora
FOR YOUR FALL TRAVEL PLANS
10-12 November 2023 - Sante Fe, NM - Spies, Lies & Nukes Conference
Spies, Lies & Nukes - Third Conference - Santa Fe, NM
Plan Your Fall Attendance NOW to capture the lower rates


This third, enhanced running of Spies, Lies & Nukes. Join Valerie Plame and some of her legendary, highly decorated, and experienced CIA colleagues as they pull back the curtain on the real life "wilderness of mirrors" that is international espionage.
Hear from and engage with the best of CIA's spies to better understand today's world: from emergent threats, to never-before-told spy operations, black market nuclear scams, how to recruit a spy, the growth of domestic terrorism, how social media is used in espionage, and keeping your employees and your company safe from foreign spies.
Topics: "Soul Catcher: The Metaphysics of Recruiting a Spy" with Jim Lawler, Former Senior CIA Ops Officer
"Delusion and Illusion in Moscow" with Jonna Mendez in conversation with Valerie Plame, Former Covert CIA Ops Officer
"CIA in the Movies" - Panel;
"China: An Emerging Threat" with Mary Beth Long, Former Assistant Secretary of Defense for International Security Affairs
"Inside Putin's Head" with Rolf Mowatt-Larssen, Former Senior CIA Intelligence Officer
"Clarity in Crisis: Leadership Lessons from the CIA" with Marc Polymeropoulos, Former Senior CIA Ops Officer
"Disinformation Distortions: AI, Deep Fakes, and Everything You Always Wanted to Know About Social Media and Espionage" with Alma Katsu, Former Senior CIA and NSA Analyst
"Morality and Ethics in the CIA" with Doug London, Former Senior Officer in the CIA's Clandestine Service
Michael Morrell in conversation with Valerie Plame, Former Covert CIA Ops Officer
"Eliminating Players on the Intelligence Battlefield: Havana Syndrome" with Marc Polymeropoulos, Former Senior CIA Ops Officer
"The End of the Global Nuclear Order" with Valerie Plame, Former Covert CIA Ops Officer
Program also includes: Former Senior CIA Intelligence Officer; Michael J. Morell, Former CIA Deputy Director
FEE: Early Bird purchase window: Apr 12 - Jun 15, $1200; Regular Sale purchase window: Jun 16 - Nov 2, $1300; Late Sale purchase window: Nov 3 - Nov 10, $1450
Ticket price does not include accommodations. More about accommodations here
Tickets include breakfasts, lunches, VIP reception and all speaker presentations and activities.
Conference location: Conference Location: La Fonda On the Plaza, 100 E. San Francisco Street, Santa Fe, NM 87501
More information or to register here
Access CIA's Inhouse Gift Shop
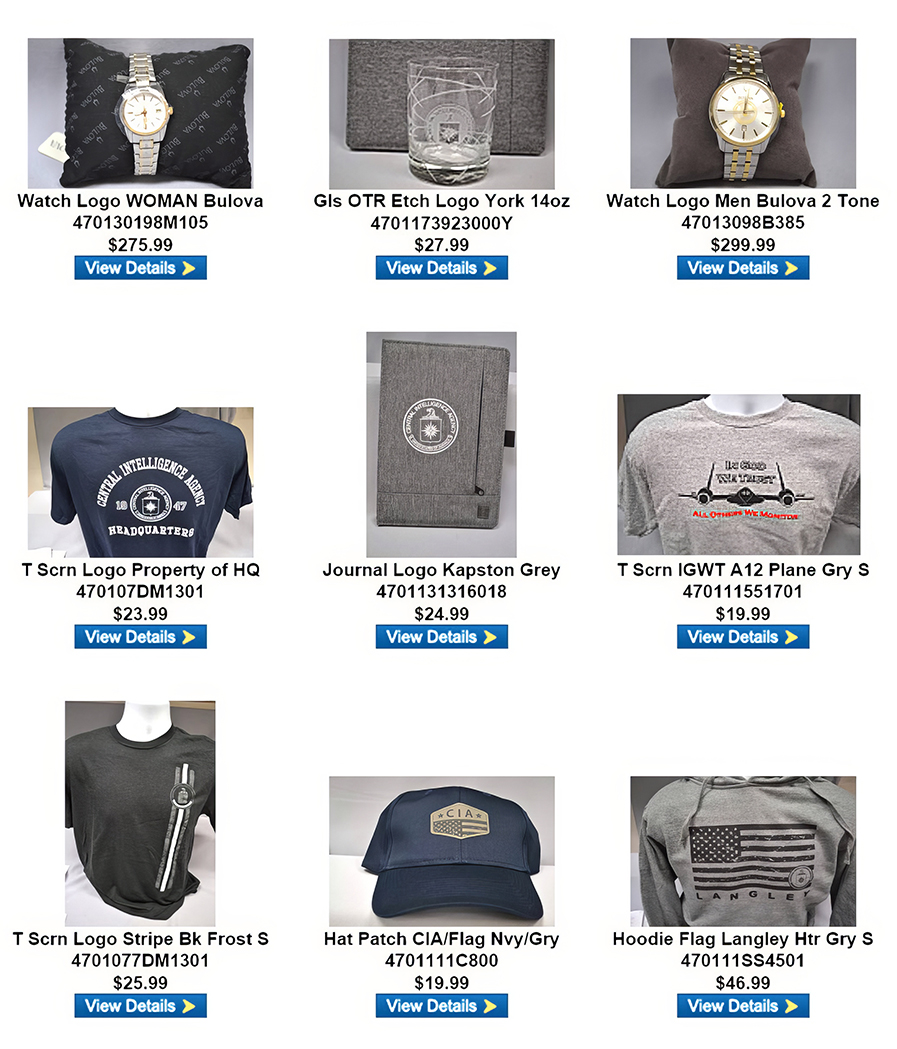
One special benefit of AFIO membership is access to CIA's EAA Store.
After completing the required, quick pre-approval process for all AFIO members, described here, you can purchase directly from the EAA online store their unusual logo'd gift items for self or colleagues. EAA on 12 May 2023 released the photo above, which features some of their newest CIA items and other gift suggestions.
FROM THE AFIO STORE
 Roy Berkeley's "A Spy's London" - Original U.S. Edition - A Few Unsold Copies Available
Roy Berkeley's "A Spy's London" - Original U.S. Edition - A Few Unsold Copies Available
In 'this remarkable book' (as intelligence historian and AFIO member Nigel West describes in his Foreword), the reader will be struck by the vibrancy of history made real. Author/AFIO member Roy Berkeley goes behind the facades of ordinary buildings, in the city that West calls 'the espionage capital of the World,' to remind us that the history of intelligence has often been made in such mundane places. With his evocative photographs and compelling observations, The 136 sites are organized into 21 manageable walks. But also a joy to armchair travelers. Among the sites: the modest hotel suite where an eager Red Army colonel poured out his secrets to a team of British and American intelligence officers; the royal residence where one of the most slippery Soviet moles was at home for years; the London home where an MP plotting to appease Hitler was arrested on his front steps in 1940.
A few copies are available at only $20 a copy (postage to a U.S.-based address included). Telephone the office at 703-790-0320 or email julie@afio.com to obtain one of these last copies.
 Clearance Sale on Long-Sleeved Polo Shirts with AFIO Logo
Clearance Sale on Long-Sleeved Polo Shirts with AFIO Logo
Superior quality and shrink resistant; features a detailed embroidered AFIO seal. The shirt color is royal blue.
The sale price is $25 and includes shipping.
Available in men's sizes only: small, medium, large, extra-large, XXL, and XXXL.
Due to limited quantities, please contact the AFIO National Office for availability of size and to provide payment information.
You may telephone the office at 703-790-0320 or email annettej@afio.com
Section I - CURRENT INTELLIGENCE NEWS HIGHLIGHTS
Turkey’s new intelligence chief hides past affiliation with Iran’s mullah regime - Nordic Monitor, 15 Jun 23
In a resume posted on the official web page of Turkish intelligence agency MIT, İbrahim Kalın, the newly appointed spymaster, did not mention his work for an Iranian-funded, radical Islamist publication that was shut down over its links to terrorism. Kalın’s connection to the Yeryüzü magazine, which promoted an Iranian-style religious revolution in Turkey, and his past work that praised Iran’s Khomeini was deliberately omitted from the long resume published by the agency last week about the new chief of the notorious intelligence service. Yeryüzü is no ordinary magazine. It was named a focal point for the Islamic Revolutionary Guard Corps (IRGC) Quds Force in the Turkish capital in an indictment drafted by the chief prosecutor’s office at the State Security Courthouse in 2000. The cell was run by Ferhan Özmen, who was trained in arms and explosives in Iran and was convicted of a series of murders including that of journalist Uğur Mumcu in the 1990s. (Full article here.)
Russian embassy: Australia blocks new Canberra site over spying risk - BBC, 15 Jun 23
Australia has blocked Russia from building a new embassy near its parliament, citing a spying risk. Prime Minister Anthony Albanese said intelligence agencies had given "very clear security advice" on the move. Laws specifically drafted to halt construction were rapidly passed on Thursday after legal attempts to block the Canberra development failed. The Kremlin said it was "yet another unfriendly action" which Russia would "take into account" in the future. Australia was following the "Russophobic hysteria that is now going on in the countries of the collective West", said spokesman Dmitry Peskov. A Russian diplomat earlier told AFP that the embassy was seeking legal advice. (Full article here.)
Russian intelligence agencies given more resources, importance under Putin - Sky News, 15 Jun 23
Russian intelligence agencies have been given more resources and importance under President Vladimir Putin, according to former diplomat Jon Richardson. Mr Richardson pointed out Mr Putin was a former KGB officer. (View video news story (4 mins) here.)
The U.S. Military Could Someday Use Microbes as Tiny Spies - Popular Mechanics, 16 Jun 23
The Department of Defense’s research and development division, the Defense Advanced Research Projects Agency (DARPA), is exploring the use of microbes to silently track enemy activities and alert U.S. forces if they’re detected. The Tellus program will enable the design of microbial sensors, invisible spies that would lie dormant and flash a covert signal if adversaries performed a certain activity. These could include tanks crossing a border, a nuclear power plant starting up, and more. DARPA, the agency behind such hits as RNA vaccines and the Internet, now wants the capability to rapidly develop microbes to track enemy forces. Project Tellus, named after the Roman goddess of the Earth, “seeks to establish the range of chemical and physical signals that microbial devices can detect, environmental conditions they can tolerate, and types of output signals that can be generated,” according to the agency’s press release. Chemical signals, according to the agency, include toxic or radioactive materials and heavy metal pollutants. Physical signals would include light, electric current, and magnetic fields. An added advantage is that the microbes would be self-powering, requiring no outside power source, or even attention or care. (Full article here.)
Why China’s new spying law has foreign firms scratching their heads, scrambling like a ‘scared monkey’ - South China Morning Post, 17 Jun 23
After three years of missing out on frequent trips to meet clients and colleagues in China, a senior partner in charge of the market for a New York-based consultancy firm was thrilled when the country reopened its borders in January. Thanks to the rising tensions between Beijing and Washington, his agency’s business has been thriving – many companies caught in the geopolitical crossfire have been seeking services and advice from the firm. And with coronavirus travel restrictions lifted, the consultant anticipated that his first post-pandemic trip to China would be in April or May. But a series of national-security-related actions taken by Chinese law-enforcement authorities against consultancy firms gave him pause. (Full article here.)
Announcing the Center for the Study of Intelligence and Nontraditional Warfare - Foreign Policy Research Institute, 16 Jun 23
The Foreign Policy Research Institute (FPRI) is pleased to announce the establishment of the Center for the Study of Intelligence and Nontraditional Warfare, a new National Security Program initiative led by “We are excited to launch this new initiative to study and promote best practices in intelligence and nontraditional warfare, a term that FPRI shall use to describe irregular warfare and political warfare as complementary tools of statecraft. This is an area of great interest to the policy community, practitioners, and the public at large. Under Phil Wasielewski’s capable leadership, I anticipate that this new Center will produce groundbreaking research and analysis,” commented President of FPRI Carol “Rollie” Flynn. The Center for the Study of Intelligence and Nontraditional Warfare’s mission is to facilitate the study of intelligence and counterintelligence, nontraditional warfare, and covert action. The Center aims to promote understanding of these specialties and how they relate to the nation’s security, including caveats in their application and lessons learned from past actions to inform future policy decisions. (Full article here.)
University shuts down its CCP-linked Confucius Institute after scrutiny from top Republican - Daily Mail, 16 Jun 23
Alfred University has agreed to close its Confucius Institute following outrage over national security concerns by House Select Committee on the Chinese Communist Party Chairman Mike Gallagher. Gallagher, R-Wis., wrote to the university last month, demanding more information on the New York school's Confucius Institute and five-year $13.5 million taxpayer-funded research grant in 2022 to by the Pentagon to conduct hypersonic weapons research. In a June 13 letter obtained by DailyMail.com, university attorney Robert Fisher responded to Gallagher saying Alfred University has decided to close the Confucius Institute 'as of June 30, 2023.' (Full article here.)
ODNI releases commercially available information report - Intelligence Community News, 15 Jun 23
On June 14, Director of National Intelligence Avril Haines issued the following statement: “Given the increasing volume of data that is commercially available, I established a Senior Advisory Group Panel on Commercially Available Information and asked them to make recommendations to the Intelligence Community (IC) regarding how and under what circumstances the IC should use commercially available information, and in particular, to reflect on the existing framework for ensuring the protection of privacy and civil liberties. The panel prepared a thorough report, along with key recommendations, which we are now considering and working to implement. I believe the public should have some sense of the policies and procedures that govern our activities in protecting national security and civil liberties and privacy. Consistent with this, when asked by Senator Wyden to review for classification purposes this report and release whatever is unclassified, I readily agreed to do so. Moreover, as I have indicated previously, once we finalize our framework for dealing with such information based on the panel’s recommendations, we will make as much of it publicly available as possible. I remain committed to sharing as much as possible about the IC’s activities with the American people.” (Full article here.)
US intelligence looks to ‘anonymize conversational speech’ recorded by IoT devices in real-time - The Sociable, 13 Jun 23
In today’s episode of the Brains Byte Back podcast, we speak with Madhav Srinath, CEO and CTO of NexusLeap, a technology and management consulting firm focused on helping organizations make sense of their data and use it to make critical business decisions. Srinath shares the story of how NexusLeap started in response to the pandemic, specifically helping food distributors consolidate data and provide insights to solve the problem of food distribution during this difficult time. Srinath also explains the meaning behind the name NexusLeap, which reflects the company's mission to help businesses break free from what they know and take a leap into using data to drive critical decisions. For Srinath, the ”nexus” part of the name refers to the congregation of important decisions and data, while the ”leap” part refers to the need to make a leap into the future to keep up with new challenges, problems, and technologies. (Full article here.)
Senate Select Committee on Intelligence Passes Intel Act, Including Security Clearance and Classification Reform - Clearance Jobs, 15 Jun 23
The Senate Select Committee on Intelligence unanimously approved the Intelligence Authorization Act for Fiscal Year 2024 (IAA), providing necessary funding, legal authorities, and enhanced oversight for the U.S. Intelligence Community (IC). Chairman of the Committee, Senator Mark R. Warner (D-VA), emphasized the bipartisan nature of the IAA, stating that it bolsters the IC’s ability to track threats posed by adversarial nations, particularly in the areas of technological and economic competition with China. The bill also focuses on reforming the nation’s security classification system, strengthening election system security, and improving the security clearance process to attract a diverse and talented workforce. Committee Vice Chairman Senator Marco Rubio (R-FL) emphasized the need for the IC to adapt swiftly in the face of great power conflicts, particularly with China and Russia colluding to undermine the United States and the international rules-based system. Rubio highlighted the importance of intelligence collection, objective analysis, and equipping policymakers with the necessary support to protect national security, promote economic prosperity, and uphold American values. (Full article here.)
How much do you know about the Intelligence Identities Protection Act? - Clearance Jobs, 13 Jun 23
Some of our nation’s most essential roles are held by people whose names we will never know. Only a handful of people can identify these clandestine individuals, and keeping their identities private is vital to preserving their lives and ensuring they can do their jobs – and retire in peace once their days working for the government are over. At least, that’s how it may work in theory. But in 1975, former CIA Officer Philip Agee published “Inside the Company: CIA Diary,” a book exposing hundreds of clandestine individuals and front companies for the United States. He continued exposing other intelligence officers and assets through additional books and articles, publicizing copious amounts of intelligence about people, operations, and more. He also encouraged other former agents to do the same. (Full article here.)
Intelligence analysts confront the reality of deepfakes - Space News, 16 Jun 23
As artificial intelligence takes center stage in the technology landscape, U.S. national security agencies see huge opportunities but also frightening risks. The rise of AI — and what it means for the future of intelligence — was a hot topic at the recent GEOINT 2023 conference held in St. Louis. During a panel discussion, officials from the National Geospatial-Intelligence Agency hailed the value of AI tools and machine learning to analyze thousands of satellite images and quickly unravel critical insights. They also alluded to the dark side of AI and the danger it creates when it’s exploited for misinformation. “The future of geoint is about going faster; it’s about using artificial intelligence,” said James Griffith, NGA’s director of source operations and management. He noted that NGA is responsible for collecting, analyzing and distributing data in support of national security as well as civilian agencies. (Full article here.)
Super spy or paper pusher? How Putin’s KGB years in East Germany helped shape him - Los Angeles Times, 15 Jun 23
Meticulous. Reticent. Clever, but never showy about it. Ever the watcher. It was 1989. The young Vladimir Vladimirovich Putin was a KGB officer in the then-East German city of Dresden, and it was one of history’s pivotal moments. The Berlin Wall had fallen. The repressive government of one of the Soviet Union’s most prized satellite states was collapsing, a prelude to the dissolution of the U.S.S.R. itself. The reunification of East and West Germany was just months away. Putin’s five-year sojourn in Dresden, which abruptly ended in 1990, has come under renewed scrutiny as the 70-year-old Russian president prosecutes an increasingly brutal and bloody war in Ukraine — a neighboring sovereign state that for the last 16 months has fiercely resisted a total Russian takeover. Against that backdrop, analysts point to the lingering legacy of Putin’s Dresden years: His determination never to allow domestic dissent to turn to a tidal surge like the one he witnessed. The realization that even a powerful elite wielding a ruthless police apparatus could suddenly find itself vulnerable. His grievance-laced dreams of a Russian empire greater than the one that slipped away before his eyes. (Full article here.)
Counterespionage Corner - Recent Arrests, Convictions, Expulsions, and more...
- The traitor: Exposing the KGB's mole inside ASIO - ABC Australia, 19 Jun 23
- Somalia: Al-Shabaab Executes Five Men On Espionage Charges - All Africa, 17 Jun 23
- Politician gets suspended sentence for classified documents acquisition, acquitted of espionage - Turkish Minute, 15 Jun 23
- Bondi man battles allegations he sold to Chinese spies - News.com.au, 14 Jun 23
- Austrian man accused of espionage, detained in Afghanistan - The Print, 13 Jun 23
- 14 Americans Currently in Prison for Being Spies - 247 Wall Street, 13 Jun 23
- SBU detains Kharkiv-based top Russian spy monitoring Ukrainian military - Yahoo News, 12 Jun 23
- Russia jails man for allegedly working with German spy agency - A News, 11 Jun 23
- How to Get Free Cybersecurity Assistance from the NSA - Clearance Jobs, 19 Jun 23
- Chinese spies breached hundreds of public, private networks, security firm says - OODA Loop, 16 Jun 23
- Two-step phishing attacks, cyber-espionage increasing - ITBrief, 15 Jun 23
- New hacking unit within Russian military intelligence identified by Microsoft - Cyber News, 15 Jun 23
Section II - REGULARLY FEATURED PODCASTS, BROADCASTS, NEWSLETTERS
The Latest from International Spy Museum Historian Andrew Hammond, PhD.
 Spycast is the official podcast of the International Spy Museum and hosts interviews with intelligence experts on matters of HUMINT, SIGINT, IMINT, OSINT, and GEOINT. Spycast is hosted by historian Andrew Hammond, PhD.
Spycast is the official podcast of the International Spy Museum and hosts interviews with intelligence experts on matters of HUMINT, SIGINT, IMINT, OSINT, and GEOINT. Spycast is hosted by historian Andrew Hammond, PhD.
13 Jun | “Spies: The Epic Intelligence War Between East vs. West” – with Calder Walton Calder Walton joins Andrew to discuss the 100-year intelligence war between the United States and Russia. Calder is the author of the new book, SPIES.
Past episodes:
06 Jun | "Anniversary Special: "The D-Day Deception" with National WWII Museum Corey Graff
30 May | From the Vault: "El Chapo, The War on Drugs, and Intelligence" with Noah Hurowitz
23 May | "70th Anniversary of James Bond Special" with Alexis Albion, Part II
The Latest Insights from Former CIA Acting Deputy Director for Operations Jack Devine.
 In Other News The proprietary analytic newsletter crafted for The Arkin Group's private clients by former CIA Acting Deputy Director for Operations Jack Devine.
In Other News The proprietary analytic newsletter crafted for The Arkin Group's private clients by former CIA Acting Deputy Director for Operations Jack Devine.
16 Jun | Putin is prioritizing control over efficiency, and it’s not going to serve him well in the long run. It’s going to take weeks, or even months, before Ukraine and allies can confidently assess the status of Ukraine’s ongoing counteroffensive. But in the interim, Putin is responding to the increased military pressure by further tightening control over his population- both in terms of the military and civil society. He’s also doubling down on political alliances that might sound promising but are unlikely to offer Russia any long-term economic or political benefit. (Full version available to AFIO members in the coming days here.)
08 Jun | As Ukraine begins its counteroffensive, Russia faces mounting pressure on multiple fronts.
Daily Analysis of Security Issues and Geopolitical Trends
 Intel Brief The Soufan Center's flagship, daily analytical product focused on complex security issues and geopolitical trends that may shape regional or international affairs. The Soufan Center was founded by former FBI Special Agent and Soufan Group CEO Ali Soufan.
Intel Brief The Soufan Center's flagship, daily analytical product focused on complex security issues and geopolitical trends that may shape regional or international affairs. The Soufan Center was founded by former FBI Special Agent and Soufan Group CEO Ali Soufan.
20 Jun | Modi State Visit Symbolizes Expanding U.S.-India Partnership
The U.S. government’s high-profile welcome for India’s Prime Minister Narendra Modi reflects its elevated expectations of enlisting India – which has always prided itself on being a leader of the Non-Aligned Movement (NAM) and an aversion to participating in geopolitical “blocs” – into a web of partnerships seen as containing the growing strategic capabilities and influence of China. Modi’s visit to the United States, scheduled for June 20-23, will include a state dinner, which is usually reserved for close allies. The dinner will mark only the third such event during U.S. President Biden’s term to date. Modi will also address a joint session of the U.S. Congress. U.S. officials perceive India as receptive to aligning against Beijing partly because of its historic rivalry with China, with whom it has had several clashes along their long border, including one as recently as December. India is a member of the Quadrilateral Security Dialogue (“Quad”), a U.S.-led forum that includes Japan, and Australia to promote security in the Indo-Pacific region. To demonstrate the value of a closer partnership with the United States, press reports indicate that U.S. officials have shared intelligence with New Delhi about China’s military buildup along the India-China border. However, New Delhi has always sought to engage and find common ground with Beijing and has thus far steered well clear of appearing to join a binding U.S.-led “alliance” against China. It is unlikely that even the lavish Washington reception for Modi will alter his stance dramatically. (Full brief here.)
19 Jun | UN Global Counterterrorism Strategy to be Adopted During UN “CT Week”
16 Jun | Global Terrorist Threat Evolves as the West Focuses on Great Power Competition
15 Jun | Settlement of the Yemen Conflict Remains Elusive
14 Jun | IntelBrief: Ukraine’s Counteroffensive Will Determine the Future Shape of the Conflict
Analysis of Global Security Events with WTOP National Security Correspondent JJ Green
 Inside the SCIF - 15 June - Cyber Hacking Campaigns, Russia, Ukraine, Disinformation, and more...
Inside the SCIF - 15 June - Cyber Hacking Campaigns, Russia, Ukraine, Disinformation, and more...
 Target USA Podcast - 14 Jun - The destruction of the Nova Khakovka Dam in Ukraine
Target USA Podcast - 14 Jun - The destruction of the Nova Khakovka Dam in Ukraine
The Hunt Broadcast - 14 Jun - 4 children were stabbed in France. Was it terrorism?
The Latest Insights from Jeff Stein and Colleagues in SpyTalk (Substack)
19 Jun | New Biden Nuclear Deal with Iran Threatens Kurds - Jonathan Broder
Pity the poor Kurds. Numbering some 40 million people who have populated the mountainous border convergence of Turkey, Syria, Iraq and Iran for centuries, they remain the world’s largest ethnic group without a state of their own. Over the past 100 years, starting with the new world order that emerged in the aftermath of World War I, both global and regional powers have thwarted the Kurds’ quest for self-determination at every tectonic turn of the Middle East’s historical wheel. Now thousands of Iranian Kurds living in exile in Iraq face yet another existential crisis. Iran, which accuses these Kurds of staging cross-border raids, collaborating with Israel and stirring up anti-government protests, is now threatening to invade their Iraqi base. The Kurds fear Baghdad will acquiesce to Tehran’s demands for their expulsion from their sanctuary. Further complicating their plight is the Biden administration’s renewed drive for a modified nuclear deal with Iran, which has pushed the plight of the Kurds to the back burner. (Full article here.)
17 Jun | Flipped: How Dan Ellsberg changed my life - Jeff Stein
It was one of those life-changing moments that you never forget. In June 1971, I was working as a daytime bartender at the Ritz Hotel off Boston Common, having a cup of coffee before the start of my shift. I unfolded the Boston Globe. And there in big black letters screamed a story about a massive leak at the Pentagon that had exposed decades worth of lies, dirty tricks and mistakes by the U.S. in Vietnam. As a recently discharged former Army intelligence operative in Vietnam, I’d known of some nasty things going on there, like the CIA’s Phoenix assassination program, which by the war’s end in 1975 would total up the number of suspected communists killed at over 20,000. The “Pentagon Papers,” as they were dubbed, had been leaked by a former war hawk and U.S. Marine, Daniel Ellsberg. To me, they merely confirmed the worst of what I had long suspected: No matter that the U.S. might’ve once had noble, if lofty, aspirations for Vietnam, the effort had gone horribly off the rails and evolved into a criminal exercise. (Full article here.)
13 Jun | All Quiet on the Miami Front - Jeff Stein
The day came and went without violence in Miami Tuesday where the Grand Wizard of Mar-a-Lago was arraigned on 37 criminal counts. Much as Trump would’ve enjoyed a spectacle of street fighting in his honor around the federal courthouse, the day was peaceful—as expected. What the feds really worry about is Trump motivating another grievances-soaked loser like Timothy McVeigh into building a truck bomb big enough to take out a federal building with casualties in the thousands. Or a white supremacist murdering a gathering of federal workers instead of Black church goers, or just Black grocery shoppers, like in Buffalo, or Latinos, or gay nightclubbers, or Jews, or merely Olympic Games attendees—you name it. To elements of MAGA world, they’re all worthy targets. (Full article here.)
To support SpyTalk, subscribe here.
Section III - MEMBER CONTRIBUTIONS
Article: CISA Order Highlights Persistent Risk at Network Edge - Krebs On Security, 15 Jun 23
The U.S. government agency in charge of improving the nation’s cybersecurity posture is ordering all federal agencies to take new measures to restrict access to Internet-exposed networking equipment. The directive comes amid a surge in attacks targeting previously unknown vulnerabilities in widely used security and networking appliances. Under a new order from the Cybersecurity and Infrastructure Security Agency (CISA), federal agencies will have 14 days to respond to any reports from CISA about misconfigured or Internet-exposed networking equipment. The directive applies to any networking devices — such as firewalls, routers and load balancers — that allow remote authentication or administration. The order requires federal departments to limit access so that only authorized users on an agency’s local or internal network can reach the management interfaces of these devices. CISA’s mandate follows a slew of recent incidents wherein attackers exploited zero-day flaws in popular networking products to conduct ransomware and cyber espionage attacks on victim organizations. Earlier today, incident response firm Mandiant revealed that since at least October 2022, Chinese cyber spies have been exploiting a zero-day vulnerability in many email security gateway (ESG) appliances sold by California-based Barracuda Networks to hoover up email from organizations using these devices. (Read full report here.)
Article: EXCLUSIVE: Chinese Intel Arm Quietly Operates ‘Service Centers’ In 7 US Cities - Daily Caller, 17 Jun 23
A Chinese intelligence agency quietly operates “service centers” in seven American cities, all of which have had contact with Beijing’s national police authority, according to state media reports and government records reviewed by the Daily Caller News Foundation. The Chinese Communist Party’s (CCP) United Front Work Department (UFWD) — which at least one U.S. government commission has characterized as a “Chinese intelligence service” — operates so-called “Overseas Chinese Service Centers” (OCSCs) that are housed within various U.S.-based nonprofits. OCSCs were ostensibly set up to promote Chinese culture and assist Chinese citizens living abroad, according to Chinese government records. State media reports, Chinese government records and social media posts show that during a 2018 trip to China, U.S.-based OCSC representatives met with Ministry of Public Security (MPS) officials. During the meeting, state security officials demonstrated how they’re leveraging new technology to conduct “cross-border remote justice services” overseas. (Read full report here.)
Video: The Most Dangerous Spy of WW2 - The Limping Lady | True Life Spy Stories (41 mins) - Philip Thompson via YouTube, March 2023
The year is 1942. The shadows of Vichy France, the Nazi puppet state, were crawling with danger. In Lyon, the third largest city in France, wanted posters started appearing on street corners. A rough sketch showed a woman’s face with sharp features and shoulder-length hair. The Abwehr and the Gestapo relentlessly hunted the woman they knew only as “the limping lady”. The woman in the poster was Virginia Hall, an American woman with a wooden leg and the unlikely mastermind behind the French Resistance in the south of France. The Gestapo's orders were clear and uncompromising: she was the most dangerous spy in the Allied forces, and they would stop at nothing to find and destroy her. As the Gestapo closed in, the stakes grew ever higher. Would Virginia succeed in establishing a resistance network able to assist in the toppling of the German war machine, or would she be caught and the resistance crushed beneath the heel of the Third Reich? (Watch here.)
Article: The US Navy, NATO, and NASA are using a shady Chinese company’s encryption chips - Ars Technica, 16 Jun 23
From TikTok to Huawei routers to DJI drones, rising tensions between China and the US have made Americans—and the US government—increasingly wary of Chinese-owned technologies. But thanks to the complexity of the hardware supply chain, encryption chips sold by the subsidiary of a company specifically flagged in warnings from the US Department of Commerce for its ties to the Chinese military have found their way into the storage hardware of military and intelligence networks across the West. In July of 2021, the Commerce Department's Bureau of Industry and Security added the Hangzhou, China-based encryption chip manufacturer Hualan Microelectronics, also known as Sage Microelectronics, to its so-called “Entity List,” a vaguely named trade restrictions list that highlights companies “acting contrary to the foreign policy interests of the United States.” Specifically, the bureau noted that Hualan had been added to the list for “acquiring and ... attempting to acquire US-origin items in support of military modernization for [China's] People's Liberation Army.” (Read full report here.)
Article: China's efforts to catch up in global electronic spying race - Reuters, 13 Jun 23
Amid reports that China is expanding its electronic eavesdropping capabilities in Cuba - which Beijing has denied - China's evolving military surveillance network has some way to go to match the sweep and reach of the U.S. and its allies, defence and intelligence analysts say. Five defence and intelligence analysts and four diplomats say large-scale military operations, even in peacetime, demand extensive attempts to vacuum up communications and electronic emissions, all part of what is known as signals intelligence (SIGINT). The targets could be, for example, conversations between military commanders, a ballistic missile communicating with its command centre or microwave exchanges between a satellite and its ground station. All generate information that can be used against adversaries in a conflict. Even if the communications can't be decoded, tracking the volume and timing of signals can provide vital intelligence, retired military officials say. Radars and jamming equipment also produce electronic signatures that can be captured. (Read full report here.)
Article: Snowden Ten Years Later - Schneier on Security, 06 Jun 23
In 2013 and 2014, I wrote extensively about new revelations regarding NSA surveillance based on the documents provided by Edward Snowden. But I had a more personal involvement as well. I wrote the essay below in September 2013. The New Yorker agreed to publish it, but the Guardian asked me not to. It was scared of UK law enforcement, and worried that this essay would reflect badly on it. And given that the UK police would raid its offices in July 2014, it had legitimate cause to be worried. Now, ten years later, I offer this as a time capsule of what those early months of Snowden were like. (Read full report here.)
Article: FBI pleads to keep FISA spy powers despite concerns over growing abuses - Washington Times, 13 Jun 23
Senior intelligence officials sought to shock Congress on Tuesday into renewing controversial spy powers, saying without the “Section 702” ability to scoop up global communications, the CIA and FBI would struggle to stop Iranian assassination attempts, Chinese hackers, Russian crimes in Ukraine, and drug smugglers pouring fentanyl across America’s southern border. They are fighting an uphill battle after revelations of appalling abuses, including illegally querying communications from Black Lives Matter protesters, crime victims and donors to a U.S. political campaign. Some 278,000 improper queries involving Americans were run on the data from 2016 to 2020. That level of abuse has endangered the existence of Section 702, which will expire at the end of this year unless Congress enacts new legislation. Key lawmakers said no extension will be granted unless it is coupled with major reforms and better transparency on who is getting snooped and why. “You have to, I hope, understand why some of us are skeptical at this point,” Senate Judiciary Committee Chairman Richard J. Durbin, Illinois Democrat, told the intelligence officials at a hearing Tuesday. (Read full report here.)
Article: Senators press Biden to release U.S. intel analysis of Chinese spy balloon incident - Washington Times, 16 Jun 23
Republican senators are pushing for President Biden to explain why a Chinese spy balloon was allowed to float across the U.S. earlier this year before being shot down. In a letter spearheaded by Sens. Marco Rubio and Roger Wicker, the lawmakers expressed frustration with the lack of transparency about the incident. “While four months have passed since a Chinese surveillance balloon was allowed to fly across the United States, your administration has yet to provide the American people a full accounting of how this spy platform was allowed to traverse across sovereign U.S. territory, what the balloon carried, and what it collected during its mission,” the senators wrote. (Read full report here.)
Article: U.S. spies purchasing troves of Americans’ data is under review by intelligence community - Washington Times, 16 Jun 23
The U.S. intelligence community is reviewing how it gathers vast troves of Americans’ personal information from businesses that harvest people’s data from phones, cars, and internet-connected devices. The intimate data available on the open market means the government needs to rethink how it acquires commercially available information (CAI), according to a new report from a panel established by the Director of National Intelligence. “In a way that far fewer Americans seem to understand, and even fewer of them can avoid, CAI includes information on nearly everyone that is of a type and level of sensitivity that historically could have been obtained, if at all, only through targeted (and predicated) collection, and that could be used to cause harm to an individual’s reputation, emotional well-being, or physical safety,” the panel’s report said. “The IC therefore needs to develop more refined approaches to CAI.” (Read full report here.)
Article: Russia Sought to Kill Defector in Florida - New York Times, 19 Jun 23
As President Vladimir V. Putin of Russia has pursued enemies abroad, his intelligence operatives now appear prepared to cross a line that they previously avoided: trying to kill a valuable informant for the U.S. government on American soil. The clandestine operation, seeking to eliminate a C.I.A. informant in Miami who had been a high-ranking Russian intelligence official more than a decade earlier, represented a brazen expansion of Mr. Putin’s campaign of targeted assassinations. It also signaled a dangerous low point even between intelligence services that have long had a strained history. “The red lines are long gone for Putin,” said Marc Polymeropoulos, a former C.I.A. officer who oversaw operations in Europe and Russia. “He wants all these guys dead.” The assassination failed, but the aftermath in part spiraled into tit-for-tat retaliation by the United States and Russia, according to three former senior American officials who spoke on the condition of anonymity to discuss aspects of a plot meant to be secret and its consequences. Sanctions and expulsions, including of top intelligence officials in Moscow and Washington, followed. (Read full report here.) (NOTE: This material may require a one time free subscription or sit behind a paywall.)
Article: AI-Generated Steganography - Schneier on Security, 13 Jun 23
Steganography is the practice of encoding secret information into innocuous content in such a manner that an adversarial third party would not realize that there is hidden meaning. While this problem has classically been studied in security literature, recent advances in generative models have led to a shared interest among security and machine learning researchers in developing scalable steganography techniques. In this work, we show that a steganography procedure is perfectly secure under Cachin (1998)’s information theoretic-model of steganography if and only if it is induced by a coupling. Furthermore, we show that, among perfectly secure procedures, a procedure is maximally efficient if and only if it is induced by a minimum entropy coupling. These insights yield what are, to the best of our knowledge, the first steganography algorithms to achieve perfect security guarantees with non-trivial efficiency; additionally, these algorithms are highly scalable. To provide empirical validation, we compare a minimum entropy coupling-based approach to three modern baselines—arithmetic coding, Meteor, and adaptive dynamic grouping—using GPT-2, WaveRNN, and Image Transformer as communication channels. We find that the minimum entropy coupling-based approach achieves superior encoding efficiency, despite its stronger security constraints. In aggregate, these results suggest that it may be natural to view information-theoretic steganography through the lens of minimum entropy coupling. (Read full report here.)
Article: Vancouver's Chinese community is closely watched by Beijing - Le Monde, 18 Jun 23
A few hours before the commemoration in a Vancouver Bay park of the 34th anniversary of the crushing of the student movement in Tiananmen Square, Kay (her first name has been changed at her request), 28, received an anonymous phone call. "You'd better not go," the caller advised her, "it's going to be hot, and you're never safe from incidents that could erupt." Originally from Shanghai, she has been living in Canada for the past four years. Despite the call, the young administrative assistant still attended the event. As a precaution, she donned a cap and a black mask that covered up half her face but said: "I'm under no illusions. They already have my photo in their database." She said that she's used to this kind of intimidation: "They don't forbid us anything, but they want to make an impression on us. I'm the one fighting in Canada for the respect of freedoms, but it's my loved ones back home who risk retaliation," she said. (Read full report here.)
Section IV - DEEPER DIVES, FILM, HISTORY, POP CULTURE
Let’s Stop Pretending Spying Is a Big Deal - Foreign Policy, 14 Jun 23
When U.S. officials complained at the annual Shangri-La Dialogue in Singapore early this month that a Chinese naval vessel had dangerously cut off a U.S. destroyer in international waters as it passed through the Taiwan Strait, China’s defense minister had a ready-made answer for how such hazards could best be avoided in the future. When U.S. officials complained at the annual Shangri-La Dialogue in Singapore early this month that a Chinese naval vessel had dangerously cut off a U.S. destroyer in international waters as it passed through the Taiwan Strait, China’s defense minister had a ready-made answer for how such hazards could best be avoided in the future. “For China, we always say mind your own business, take good care of your own vessels, your fighter jets, take good care of your own territorial airspace and waters,” said Gen. Li Shangfu. “If that is the case, then I don’t think there will be future problems.” (Full report here.)
Using the Global Online Exchange to Enhance Cultural Intelligence in Future IC Workforces - Journal of Intelligence, Security, and Resilience Education (2023)
Ethnocentrism in intelligence analysis produces challenges in cognition, analysis, and collection that many analysts may not recognize. The most significant challenges are manifestations of mirror-imaging biases and institutional biases that leave gaping cognitive holes. One tool to increase the cultural intelligence of a future U.S. Intelligence Community workforce is incorporating the Global Online Learning Exchange (GOLE) and similar virtual exchange programs within undergraduate intelligence courses. This paper explores the use of GOLE in an undergraduate intelligence course where students in the United States and Australia participated in a joint tabletop exercise using video conferencing. (Full report here.)
The Lawfare Podcast: We Need To Talk About the Espionage Act (46 mins) - The Lawfare Podcast, 15 Jun 23
The first 31 counts of the Trump Mar-a-Lago indictment all are under the Espionage Act, which has led to a lot of confusion because Trump is not accused of spying. Heidi Kitrosser is a professor of law at Northwestern University and an expert on the Espionage Act. She wrote a recent piece in Lawfare about the Espionage Act and its history of prosecutions during the Trump Administration. She joined Lawfare Editor-in-Chief Benjamin Wittes to talk about the law, its history, the problems with it, and how overbroad it is in some areas—and why none of those areas implicate the Trump indictment. It's an interesting conversation that covers media prosecutions, prosecutions of leakers, and prosecutions of spies, and it will give you all the background you need to understand the controversy about the charges against Trump. (Watch here.)
Aliens Or Not, Secret Crash Retrieval Programs Are A Very Real Thing - The Drive, 15 Jun 2023
News first broke just over a week ago that a former career American intelligence officer is alleging the U.S. government is concealing a decades-long top-secret 'crash retrieval' program that has overseen the recovery of otherworldly flying machines and their pilots. There remains no hard evidence available to the public to substantiate these claims. Yet the U.S. military and intelligence community's shadowy crash retrieval programs are a very real thing, although the ones we know about are focused on foreign, not alien technology. These secretive endeavors are part of a larger ecosystem focused on gathering intelligence — through examining, reverse engineering, and testing — non-U.S. weapon systems and other equipment through so-called Foreign Materiel Exploitation, or FME. This extensive espionage ecosystem, honed over nearly a century of operations, lives in the shadows, but remains an indispensable discipline that has paid off massively time and time again. (Full report here.)
Interactive: Comparing Military Spending Around the World - Visual Capitalist, 04 Jun 23
One of the easiest ways to identify a nation’s priorities is by tracking its expenditures, and military spending is no different. Usually spending is measured, and ranked, in absolute amounts. For example, countries around the world collectively spent $2.1 trillion on their militaries in 2021, with the most coming from the U.S. ($800 billion), China ($293 billion), and India ($77 billion). But these eye-popping figures are best understood in the context of each country’s economy. Using data from the Stockholm International Peace Research Institute (SIPRI), Varun Jain has visualized 158 countries’ military expenditures, both as a percentage of their total GDP as well as in average per-capita spend. (Access visual tool and full report here.)
Intelligence in History - A Collection of Recent Content
- 10 Spy Satellites That Soared Through Space In The Cold War - Slash Gear, 17 Jun 23
- A brief history of the Espionage Act in the Pacific Northwest - Cross Cut, 16 Jun 23
- A Historic Cold War Execution on Espionage Charges: Information Delayed is Information Denied - Just Security, 16 Jun 23
- Operation Gold: 9 Interesting Facts About The Berlin Spy Tunnel of the Cold War - SOFREP, 15 Jun 23
- During the Cold War, Canada Designed a World-Class Interceptor — But Was the Program Infested With Soviet Spies? - History Net, 14 Jun 23
- An advisor to former PM Rajiv Gandhi recalls how a 1985 espionage scandal rocked Indian politics - Scroll, 14 Jun 23
- Behind the Bamboo Curtain: Two CIA Officers Imprisoned in China - Spyscape, 12 Jun 23
- British officials dismissed CIA ‘ghost stories’ about Saddam before Gulf War - Metro, 11 Jun 23
- In the Shadow of the KGB: Legacy of Czechoslovak Intelligence (1948–1989) - International Journal of Intelligence and Counterintelligence, 18 May 23
True Intelligence Matters in Film - M. Butterfly - David Cronenberg (1993)
 René Gallimard (Jeremy Irons) is a French diplomatic code clerk assigned to Beijing, China in the 1960s. He becomes infatuated with a Peking opera performer, Song Liling (John Lone), who spies on him for the government of the People's Republic of China. Their affair lasts for 20 years, and they subsequently marry, with Gallimard all the while apparently unaware, or willfully ignorant, of the fact that, in Peking opera, female leading roles were traditionally performed by men.
René Gallimard (Jeremy Irons) is a French diplomatic code clerk assigned to Beijing, China in the 1960s. He becomes infatuated with a Peking opera performer, Song Liling (John Lone), who spies on him for the government of the People's Republic of China. Their affair lasts for 20 years, and they subsequently marry, with Gallimard all the while apparently unaware, or willfully ignorant, of the fact that, in Peking opera, female leading roles were traditionally performed by men.
More information about this based-on-true-events production here.
Walking Tours - Washington, DC - Sundays (Dates/Times Vary)
Former intelligence officers guide visitors on two morning and afternoon espionage-themed walking tours: "Spies of Embassy Row" and "Spies of Georgetown." For more information and booking, click here or contact rosanna@spyher.co
Section V - Books, Research Requests, Jobs, Obituaries
Books — Forthcoming, Newly Released, Overlooked
 Spy Ships: One Hundred Years of Intelligence Collection by Ships and Submarines
Spy Ships: One Hundred Years of Intelligence Collection by Ships and Submarines
by Norman Polmar, Lee J. Mathers, and Rear Admiral Thomas A Brooks
(Potomac Books, 01 Jul 23)
Almost from the first days of seafaring, men have used ships for “spying” and intelligence collection. Since early in the twentieth century, with the technological advancements of radio and radar, the U.S. Navy and other government agencies and many other navies have used increasingly specialized ships and submarines to ferret out the secrets of other nations. The United States and the Soviet Union/Russia have been the leaders in those efforts, especially during the forty-five years of the Cold War. But, as Norman Polmar and Lee J. Mathers reveal, so has China, which has become a major maritime power in the twenty-first century, with special interests in the South China Sea and with increasing hostility toward the United States. Through extensive, meticulous research and through the lens of such notorious spy ship events as the Israeli attack on the USS Liberty, the North Korean capture of the USS Pueblo, and the U.S. Central Intelligence Agency’s success in clandestinely salvaging part of a Soviet submarine with the Hughes Glomar Explorer, Spy Ships is a fascinating and valuable resource for understanding maritime intelligence collection and what we have learned from it.
Order book here.
 The Central Intelligence Agency and Overhead Reconnaissance: The U-2 and OXCART Programs, 1954-1974
The Central Intelligence Agency and Overhead Reconnaissance: The U-2 and OXCART Programs, 1954-1974
by Gregory Pedlow and Donald Welzenbach
(Skyhorse, 15 Mar 16)
The CIA’s 2013 release of its book The Central Intelligence Agency and Overhead Reconnaissance 1954–1974 is a fascinating and important historical document. It contains a significant amount of newly declassified material with respect to the U-2 and Oxcart programs, including names of pilots; codenames and cryptonyms; locations, funding, and cover arrangements; electronic countermeasures equipment; cooperation with foreign governments; and overflights of the Soviet Union, Cuba, China, and other countries. Originally published with a Secret/No Foreign Dissemination classification, this detailed study describes not only the program’s technological and bureaucratic aspects, but also its political and international context, including the difficult choices faced by President Eisenhower in authorizing overflights of the Soviet Union and the controversy surrounding the shoot down there of U-2 pilot Francis Gary Powers in 1960. The authors discuss the origins of the U-2, its top-secret testing, its specially designed high-altitude cameras and complex life-support systems, and even the possible use of poison capsules by its pilots, if captured. They call attention to the crucial importance of the U-2 in the gathering of strategic and tactical intelligence, as well as the controversies that the program unleashed. Finally, they discuss the CIA’s development of a successor to the U-2, the Oxcart, which became the world’s most technologically advanced aircraft. For the first time, the more complete 2013 release of this historical text is available in a professionally typeset format, supplemented with higher quality photographs that will bring alive these incredible aircraft and the story of their development and use by the CIA. This edition also includes a new preface by author Gregory W. Pedlow and a foreword by U-2 expert Chris Pocock. Skyhorse Publishing, as well as our Arcade imprint, are proud to publish a broad range of books for readers interested in history--books about World War II, the Third Reich, Hitler and his henchmen, the JFK assassination, conspiracies, the American Civil War, the American Revolution, gladiators, Vikings, ancient Rome, medieval times, the old West, and much more. While not every title we publish becomes a New York Times bestseller or a national bestseller, we are committed to books on subjects that are sometimes overlooked and to authors whose work might not otherwise find a home.
Order book here.
 OSINT Tools: A Practical Guide to Collection, Analysis, and Visualization
OSINT Tools: A Practical Guide to Collection, Analysis, and Visualization
by Paul Michel
(Amazon, 21 May 23)
OSINT Tools - A Practical Guide to Collection, Analysis, and Visualization, written by Paul Michel, is a comprehensive guidebook that equips readers with the necessary knowledge and skills to effectively leverage open source intelligence (OSINT) tools for information gathering, analysis, and visualization. In today's digital age, where vast amounts of data are available online, OSINT has become an invaluable resource for various fields, including cybersecurity, law enforcement, intelligence, journalism, and corporate investigations. This book serves as an essential resource for professionals and enthusiasts alike who seek to harness the power of OSINT tools in their work. With his extensive experience in OSINT and passion for the subject matter, Paul Michel provides readers with a step-by-step approach to navigate the ever-expanding landscape of OSINT tools. The book begins by laying a solid foundation, covering the evolution and importance of OSINT, key principles and concepts, and its applications in law enforcement, intelligence agencies, corporate investigations, journalism, and open-source investigations. The author also delves into the ethical considerations surrounding OSINT, highlighting the need for responsible and ethical practices in data collection and analysis. Throughout the book, Paul Michel introduces readers to a wide array of tools and techniques that enhance OSINT capabilities. Essential hardware requirements, operating systems, virtualization, and software tools are discussed, ensuring readers have a comprehensive understanding of the technical aspects necessary for effective OSINT investigations. The book also explores secure communication and encryption tools, data organization and management, collaboration platforms, automation through scripting and APIs, and the availability of training and certification programs. The author provides practical insights into web scraping techniques, including HTML parsing, XPath, API integration, and overcoming anti-scraping measures. Readers learn how to extract information from popular social media platforms such as Twitter, Facebook, LinkedIn, Instagram, and YouTube, as well as how to monitor online discussions, detect misinformation, and navigate the dark web. The book also delves into advanced search techniques, geolocation analysis, image and video forensics, and data visualization methods. One of the standout features of this book is its emphasis on ethical considerations. Paul Michel addresses privacy laws, consent, data protection, anonymization techniques, and intellectual property rights, ensuring readers understand the legal and ethical boundaries of OSINT investigations. The book also explores the responsible use of emerging technologies, such as facial recognition, object recognition, and deepfake detection, encouraging readers to approach these tools with a critical and ethical mindset. OSINT Tools - A Practical Guide to Collection, Analysis, and Visualization is written in a clear and accessible manner, making complex concepts and techniques easily understandable for readers at various skill levels. The book is enriched with real-world case studies, practical examples, and screenshots of tools and platforms, providing readers with a hands-on learning experience.
Order book here.
Research Requests and Academic Opportunities
Northeastern University Security and Intelligence Studies professor researching the skill sets required for Intelligence Analysis degree holders to see success after graduation welcomes the participation of AFIO members in a 5-minute survey in support of the research. Access survey here.
Call for Information: 430th CIC in Salzburg in 1946
I am currently writing about 430th CIC in Salzburg in 1946. I have a (large) CIC file and am now trying to track down further details about two officers mentioned in this: (1) Bill Taylor. The sources do not make clear whether the officer was Major Bill G. Taylor, GSC, Head of the Counter-Intelligence Bureau of G-2 (Intelligence Section), US Forces Austria, or “Mil.Reg.” Captain Taylor of Salzburg. Any information on either/both of these officers would be most welcome. (2) Pace B Rose. Rose was a CIC Special Agent in Austria, later a CIA officer who continued to be attached to the Agency after retirement. He died on 3 January 2009. I would like to contact family and friends of Pace Rose. According to the internet, Rose had children, Donna R. Hilverts and Gary W. Rose, and five grandchildren and three great grandchildren. Please contact S.Cody@westminster.ac.uk with any information.
Call for Sources: Intelligence Officers Who Lived in Spain in the 1970s
Spanish journalist Francisco Jiménez is preparing a documentary about the intelligence services in Spain in the 70s. He is looking for intelligence officers who worked in Spain in those years. If you are willing to assist Francisco, he can be reached at fjimenez@globomedia.es.
The Washington Post is developing a multi-part audio documentary series (i.e. podcast) chronicling the Grenadian revolution and the US intervention in 1983. They've interviewed nearly 100 people so far, ranging from the heads of state, former Grenadian officials, current and former US officials, veterans, and intelligence officers. They're looking for people who served at the time and may be knowledgeable about intelligence activities in Grenada and the southern Caribbean between 1979 and Operation Urgent Fury. They would also be interested in speaking with anyone who knew Leonard Barrett during the same period. If anyone is interested in participating, please reach out to Washington Post reporter Ted Muldoon via email at ted.muldoon@washpost.com or on Signal at 651-497-5449.
Call for papers: Intelligence and Post-War Reconstruction - International Journal of Intelligence and Counterintelligence
History shows that without planning for post-war reconstruction, apparent victory in war can lead to long-term defeat. On the other hand, wise post-war planning can lead to friendly, peaceful, and profitable relations between victor and vanquished. For political, socio-economic and security-related planning, intelligence plays a crucial role in estimating capabilities, securing infrastructure, locating persons of interest, and rebuilding. In honor of the 75th anniversary of the European Recovery Program (Marshall Plan) after the Second World War, the editors are particularly interested in papers dealing with intelligence concerning post-war reconstruction initiatives and planning connected to historical and recent conflicts. Both case studies and theoretical and methodological approaches are welcome. The studies may include, but do not have to be focused on, the following questions and issues:
- The role of diplomatic and military intelligence during the conflict as preparation for post-war reconstruction, from the conceptual to the practical.
- What intelligence needs to be collected to secure and boost reconstruction?
- What contacts, networks, and infrastructure are necessary for intelligence to be effective?
- Who has been or should be approached and/or recruited for reconstruction efforts based on intelligence?
- When has intelligent post-war planning (or its opposite) been historically evident?
- How should intelligence interact with formerly warring parties and international organizations to empower practical reconstruction efforts?
- What intelligence collection challenges have services encountered in working for post-war peace?
- How did intelligence factor in the European Recovery Program?
- What was George C. Marshall's position on the role of intelligence in general or concrete examples related to "his" plan?
01 Nov 23 deadline. More information and submission instructions here.
Call For Articles: AFIO Journal, The Intelligencer
For the past four years, AFIO has included in The Intelligencer a series of articles on "when intelligence made a difference." Written by scholars, intelligence practitioners, students, and others, they cover events from ancient times to the modern world and in many countries. AFIO is soliciting articles for future issues. Most articles run between 2,000 and 3,000 words, although some are longer or shorter. If you have an idea for an article that fits the theme, email senior editor Peter Oleson at peter.oleson@afio.com.
Jobs
Retired Federal Government Employees Wanted - National Security Agency - Fort Meade, Maryland
The National Security Agency (NSA) may occasionally need skilled civilian retirees to augment the existing work force on high priority projects or programs. In order to fill these temporary positions quickly, we need to know who may be interested and available to return to work with us on a short notice basis as well as their skills. Retirees provide expertise and corporate knowledge to temporarily support mission requirements, manpower shortfalls, and/or mentor the next generation of Agency employees. Salary Range: $86,335 - $170,800.
Additional information and application here.
Assistant/Associate Professor of Intelligence Studies (Global Security and Intelligence Studies) - Embry-Riddle Aeronautical University - Prescott, Arizona
Embry-Riddle Aeronautical University's Prescott, Arizona campus is accepting applications for a tenure-track assistant or associate-level professor of intelligence studies to teach intelligence courses to students in the Global Security and Intelligence program. The successful candidate will teach students about the intelligence community, strategic intelligence, the intelligence cycle and intelligence analysis, writing, and briefing. Prior experience working in the intelligence community is strongly preferred. We are interested in candidates with teaching acumen in intelligence analysis and writing using structured analytical techniques.
Additional information and application here.
Teaching Associate - Intelligence and National Security Studies - Coastal Carolina University, South Carolina
The Department of Intelligence and Security Studies ( ISS ) at Coastal Carolina University is accepting applications for a pool of Teaching Associates (part-time adjunct faculty) to teach introductory and undergraduate elective course offerings for the program beginning in August 2022. While the ad is open to any specialization within the field of study, courses in the areas of homeland security, law enforcement intelligence, counter-narcotics, and cybersecurity are of particular interest. Course offerings can be in a face-to-face or synchronous online modality. To be considered, candidates must have a masters or doctoral degree in a relevant subject area. Prior professional experience in the profession, as well as prior teaching experience are preferred.
Additional information and application here.
Obituaries
![]() Thomas Glenn — Career NSA Officer
Thomas Glenn — Career NSA Officer
Thomas Louis Glenn III, 87, passed away June 4, 2023 from small cell lung cancer. Born in Los Angeles, California, Dr. Tom Glenn worked as an intelligence operative, a musician, a linguist (seven languages), a cryptologist, a government executive, a caregiver for the dying, a leadership coach, and, always, a writer. Many of his prize-winning short stories (17 in print) came from the 13 years he shuttled between the U.S. and Vietnam as an undercover NSA operative supporting Army and Marine units in combat before escaping under fire when Saigon fell as the last man out of Saigon. With a BA in Music, a Master’s in Government, and a Doctorate in Public Administration and trained as a musician, actor, and public speaker, he toured the U.S. lecturing on leadership and management, trained federal executives, and was the Dean of the Management Department at the National Cryptologic School. Maryland Public Television interviewed him and 15 others in its 2016 salute to Vietnam vets. His memoir article on the fall of Saigon has been published by Studies in Intelligence and reprinted in the Atticus Review and the Cryptologic Quarterly. In late 2017, the New York Times published his story on his role in the 1967 battle of Dak To in Vietnam’s central highlands. Dr. Glenn was a reviewer for the Washington Independent Review of Books and the Internet Review of Books where he specialized in books on war and Vietnam. His Vietnam novel-in-stories, "Friendly Casualties" was published both as an e-book and in hardcopy. His novel "Last of the Annamese" which was set during the fall of Saigon has won multiple awards, most recently the 2022 Gold Winner Historical Realistic Fiction award from the Human Relations Indie Books. His latest novel, "Secretocracy", and his new collection of short stories, "Coming to Terms", were published in 2020. Dr. Glenn was a Phoenix Society member who served at the Agency for 32 years, retiring in October 1993.
![]() Mary Stafford — Former Director of Admin for NGA's Predecessor
Mary Stafford — Former Director of Admin for NGA's Predecessor
Mary Jane Stafford passed away in her home on Saturday, June 10, 2023. She was the daughter of the late Rose Marie Yeropoli and James Vadala and a 1949 graduate of McKeesport, PA High School. In 1960 she moved to Arlington, VA and began her career with the Department of the Army, Chief of Information Office, Pentagon and later worked with several other Dept. of Defense organizations. She retired in 1990 as the Director of Administration for the Defense Mapping Agency now known as the National Geospatial-Intelligence Agency and received the agency's Meritorious Civilian Service award for her outstanding accomplishments.
Section VI - Events
6 Jul 23 (Thursday), 1900 (Central) - Virtual - LTG Michael Groen, USMC, Ret. on Artificial Intelligence. Hosted by The San Antonio AFIO Chapter. This San Antonio AFIO Chapter's program will be on Artificial Intelligence. This will be an excellent program that should give you an increased understanding of AI. LTG Michael Groen (USMC, Ret), former Commander of the Joint Artificial Intelligence Center, will speak about AI in this AFIO NOW program. He is interviewed by AFIO President James Hughes. General Groen and Jim Hughes discuss the Joint Artificial Intelligence Center, the meaning, uses, adoption problems, and ethics of AI in the military and beyond. The interview runs 44 minutes and includes several Q&As. On 6 July 2023 at 7 pm Central Time click on this link to join the program. Questions? Email Chapter President John Franklin at satxafio@gmail.com or call him at 210 863-0430.
27 Jul 23 (Thursday), 1130 (Pacific) - In Person - Col. Robert W. Parr, USAF (ret) on "12 Days with a Soviet Pilot Defector" - Basque Cultural Center, San Francisco - The AFIO Andre LeGallo Chapter. No host cocktail at 1130 hours (Pacific). Meeting starts at 1200 hours. Basque Cultural Center, 599 Railroad Avenue, South San Francisco, CA. RSVP and pre-payment required. More information and registration here.
See the AFIO Calendar of Events for scheduling further in the future.
Events from Advertisers, Corporate Sponsors, Others
Before he became a federal judge and a consequential justice on the Supreme Court, Antonin Scalia served in the Nixon and Ford administrations. Amid the turmoil of the post-Watergate era, Scalia helped reform the intelligence community, worked to preserve the executive powers of the presidency, and provided legal authorization for covert operations. James Rosen is exploring Scalia's life in a two-volume biography. The first volume, Scalia: Rise to Greatness, 1936-1986, just debuted. Rosen, a veteran reporter and bestselling historian, will reveal Antonin Scalia's Executive Branch experiences with the US intelligence community. Drawing on unparalleled access to new documentary and personal sources, Rosen traces Scalia's ground-breaking work on the reforms of the post-Watergate era, including new Justice Department guidelines for the use of surveillance at sensitive foreign installations; his testimony before the Pike Committee; and his role in the approval of covert operations, including the evacuation of the US Embassy during the fall of Saigon in April 1975. Rosen knew Justice Scalia personally and he will discuss Scalia's life and legacy with wit and firsthand insight — just how fast a driver was the justice in his BMW, anyway? Rosen will let us know in his conversation with Amanda Ohlke, Director of Adult Education at the Spy Museum. Program is free of charge but requires advanced registration. Visit www.spymuseum.org.
27 Jun 23, 1400-1500 (ET) - SPY with Me: Memory Loss Program – International Spy Museum - Virtual
International Spy Museum's SPY with Me is an interactive virtual program for individuals living with dementia and their care partners. Join SPY as we use music and artifacts to explore some of our favorite spy stories. Programs last one hour and are held virtually through Zoom. Every month the same program is offered on two different dates. To register, please email Shana Oltmans at soltmans@spymuseum.org. Free but space is limited. Visit www.spymuseum.org.
29 Jun 23, 0900-0945 (ET) - Coffee and Conversation with The Hon. Michael Vickers – INSA - Virtual
Join intelligence and national security colleagues online on Thursday, June 29, from 9:00-9:45 am ET, for a special Coffee & Conversation with The Hon. Michael G. Vickers, former Under Secretary of Defense for Intelligence. In a moderated conversation with Letitia A. Long, Chairwoman, INSA Board of Directors, Mr. Vickers will discuss his latest memoir, By All Means Available: Memoirs of a Life in Intelligence, Special Operations, and Strategy, including: Key accomplishments during his time at CIA, specifically his role in the invasion of Grenada, operational response to the Beirut bombings, and the covert effort to drive the Red Army out of Afghanistan; Leading the comprehensive transformation of defense intelligence capabilities, while USD(I); Serving as the first ASD for Special Operations, Low-Intensity Conflict & Interdependent Capabilities...and much more! Plus, there will be ample time for audience Q&A! Register here.
"The Nation's Premier Intel and National Security Event" - Save the date for the 10th Annual AFCEA/INSA Intelligence and National Security Summit! The powerful, two-day program, at the Gaylord National Resort, will feature five blockbuster plenaries, six engaging breakout sessions, and a jam-packed exhibit hall full of the latest IC technology innovations. Top leaders will discuss State of the Community, Military Intelligence Priorities, Strategic Intelligence, and Cybersecurity Challenges. Breakout sessions with senior leaders, technology experts, and thought leaders will examine some of the most pressing issues facing the community. Plus, powerful networking opportunities designed to foster partnerships and relationship building. Check for for full agenda and updates here.
20-22 Jul 2023 - NASIH Annual Conference 2023 – NASIH - In Person - University of Calgary, Canada
North American Society for Intelligence History's annual event. Registration is open and the registration fee will increase on 15 Jun 23. Full details on this two-day program, with extensive speaker line up and panels, here. Registration here.
Gifts for Friends, Colleagues, Self
 Now available: Black short-sleeved polo shirts with Embroidered AFIO logo
Now available: Black short-sleeved polo shirts with Embroidered AFIO logo
Show your support for AFIO with our new Black Short-sleeve Polo Shirts. Shirts are shrink and wrinkle resistant of fine cotton with a soft, "well-worn, comfy" yet substantial feel. They feature a detailed embroidered AFIO seal. Get a shirt for yourself and consider as gifts for colleagues, family, and friends. Only $50 each including shipping.
Sizes for (M) men, only; Small, Medium, Large, XL, XXL, and XXXL. $50 per shirt.
You may pay by check or credit card. Complete your order online here or mail an order along with payment to: AFIO, 7600 Leesburg Pike, Ste 470 East, Falls Church, VA 22043-2004. Phone orders at 703-790-0320. Questions? Contact Annette at: annettej@afio.com.

PopSocket for cellphones or tablets
Show your support to AFIO while enjoying the convenience offered by our AFIO Logo PopSocket. The PopSocket is most commonly used as a stand and as a grip for your mobile phone or tablet; handy for taking selfies, watching videos, and for texting. The PopSocket looks like a small button or sticker which, when closed, sticks flat to your mobile device. However, its accordion-like design enables it to pop open for use. The benefits of using a PopSocket make it a must-have accessory for your mobile phone or tablet. It also aids in keeping your phone from slipping off your hand during use, falling, or breaking.
Price: $15. Order this and other store items online here.

Duffel Bags - Royal Blue and Black with Full Color AFIO Logo This duffel has it all when it comes to value, style and organization.
600 denier polyester canvas with polyester double contrast; D-shaped zippered entry for easy access. Front pocket with hook and loop closure. End mesh pocket Easy-access end pockets. Four durable, protective feet and built-in bottom board for added strength. Web handles with padded grip. Detachable, adjustable shoulder strap.
Dimensions: 11"h x 19.75"w x 9.75"d; Approx. 2,118 cubic inches
Price: $50. Order this and other store items online here.
AFIO Mug with color glazed seal.
Made in the U.S.A., dishwasher-safe.
$35 includes shipping.
Sip your morning joe in style or use it to stash pens, cards, paperclips, or candy.
Order this and other store items online here.

Caps - Dark Navy with Navy AFIO Logo
An authentic silhouette with the comfort of an unstructured, adjustable fit. Fabric: 100% cotton. Unstructured. Fabric strap closure with adjustable D-clip. Price: $30. Order this and other store items online here.
| PUBLISHED
IN 2023 Be informed on career opportunities in the U.S. Intelligence Community |
||
 |
Intelligence as a Career - with updated listings of colleges teaching intelligence courses, and Q&As on needed foreign languages, as well as the courses, grades, extracurricular activities, and behavioral characteristics and life experiences sought by modern U.S. intelligence agencies. AFIO's popular 47-page booklet reaches thousands of high school, college students, university guidance offices, and distributed in classes teaching intelligence, to help those considering careers in the U.S. Intelligence Community. |
 |
| This is the all new fifth edition. The publication is also popular with University Career Guidance Centers, professors and academic departments specializing in national security, and parents assisting children or grandchildren in choosing meaningful, public service careers. This booklet is provided online as a public service from the generosity of AFIO board, volunteer editors/writers, donors, and members. We thank all for their support which makes this educational effort possible. |
||
| Careers Booklet (new 2023 Fifth Edition) can be read or downloaded here |
||
 Guide to the Study of Intelligence...and...When Intelligence Made a Difference
Guide to the Study of Intelligence...and...When Intelligence Made a Difference
"AFIO's Guide to the Study of Intelligence" has sold out in hard-copy.
It is available in digital form in its entirety on the
AFIO website here.
Also available on the website here are the individual articles of AFIO's
history project "When Intelligence Made a Difference" that have been
published to date in The Intelligencer journal.
More articles will be appear in future editions.
Some features of the email version of the WIN do not work for readers who have chosen the Plaintext Edition, some AOL users, and readers who access their email using web mail. You may request to change from Plaintext to HTML format here afio@afio.com. For the best reading experience, the latest web edition can be found here: https://www.afio.com/pages/currentwin.htm
To unsubscribe from the WIN email list, please click the "UNSUBSCRIBE" link at the bottom of the email. If you did not subscribe to the WIN and are not a member, you received this product from a third party in violation of AFIO policy. Please forward to afio@afio.com the entire message that you received and we will remove the sender from our membership and distribution lists.
(c) 1998 thru 2023
AFIO Members Support the AFIO Mission - sponsor new members! CHECK THE AFIO WEBSITE at www.afio.com for back issues of the WINs, information about AFIO, conference agenda and registrations materials, and membership applications and much more! .
AFIO | 7600 Leesburg Pike, Suite 470 East, Falls Church, VA 22043-2004 | (703) 790-0320 (phone) | (703) 991-1278 (fax) | afio@afio.com