15 - 21 March 2023 — (Issue 12)
is sponsored by

Readers who encounter problems with the email version of this newsletter can
view the latest web edition here.
| Visit us on |
CONTENTS
Section I - CURRENT INTELLIGENCE NEWS HIGHLIGHTS
- Russia's Kremlin bans iPhones as Putin's workers fear espionage threat - iMore, 20 Mar 23
- The CIA’s CTO and deputy director explain the future of spying - Fast Company, 20 Mar 23
- Surveillance nation: India spies on world's largest population - Context, 19 Mar 23
- China-backed espionage is getting harder to spot, researchers say - Axios, 17 Mar 23
- DIA's New China Mission Group to Track Threat Posed by AI Development - NextGov, 14 Mar 23
- YoroTrooper Espionage Campaigns Target CIS, EU Countries - OODA Loop, 16 Mar 23
- Canada investigating claims of secret Chinese police stations in Montreal - Intel News, 14 Mar 23
- What's Up There, Where Is It, and What's It Doing? The U.S. Space Surveillance Network - National Security Archive, 13 Mar 23
- Ethnic Uyghurs Forced to Confront Foreign Influence Concerns - Clearance Jobs, 19 Mar 23
- GCHQ spy chiefs warn Microsoft's ChatGPT and other AI chatbots pose a security risk - Daily Mail, 15 Mar 23
- Mexico probes army's use of spyware against human rights activists - NPR, 18 Mar 23
- 'American spy' stabbed near GCHQ in alleged terrorist incident was known to her attacker - The Telegraph, 15 Mar 23
- Readout on Defence Geospatial Intelligence (DGI) 2023 Conference - GeoConnexion, 13 Mar 23
- Russian Cyberspies Abuse EU Information Exchange Systems in Government Attacks - OODA Loop, 17 Mar 23
- Counterespionage Corner - Recent Arrests, Convictions, Expulsions, and more...
Section II - REGULARLY FEATURED PODCASTS, BROADCASTS, NEWSLETTERS
- The U.S. Invasion of Iraq: A Look at Intelligence, 20 Years Later — Former Acting CIA Director Mike Morell, Intelligence Matters
- "Hitler's Trojan Horse" - Nazi Intelligence with Nigel West — Andrew Hammond, PhD. SpyCast
- Emboldened by an unprecedented third term, Chinese President Xi's ambitions are inciting many firsts. — Former Acting CIA Dep. Dir. for Ops and Arkin Group President Jack Devine, In Other News
- South Africa - an ISIS Financial Hub, Is The U.S. a Viable Partner for Central Asia, Iraq 20 Years Later, China Spy Balloon's Revelation About The U.S., Ukraine War Erodes Russian Arms Sales — Former FBI Special Agent and Soufan Group CEO Ali Soufan, Intel Brief
- Vladimir Kara-Murza's trial delayed, Pentagon footage of Russian jet colliding with U.S. drone, FBI Washington Field Office Chief concerns, DNI Haines' comments at hearing, Russian spies in Poland, and more... — WTOP National Security Correspondent JJ Green - Inside the SCIF, Target USA, The Hunt
- Israeli-Saudi intel ties, Ukraine air combat, Air America, and new Saudi-Iran ties - Jeff Stein and Colleagues in SpyTalk (Substack)
Section III - MEMBER CONTRIBUTIONS
- Article: This Is the New Leader of Russia's Infamous Sandworm Hacking Unit - Wired, 15 Mar 23
- Article: Losing Iraq Worse Than We Had To - National Review, 16 Mar 23
- Article: The story behind spies and The Fourth Man - Santa Barbara News Press, 18 Mar 23
- Article: 'The Hunt for Red October' Is Based on This Real Soviet Mutiny - Military.com, 17 Mar 2023
- Article: Entire Russian spy network dismantled in Poland - BBC, 16 Mar 23
- Article: Alleged Russian spy and sabotage cell busted in Poland - Intel News, 16 Mar 23
- Article: How many Russians have been killed in Ukraine? - Economist, 08 Mar 23
- Article: A Spy Wants to Connect With You on LinkedIn - Wired, 15 Mar 23
- Article: US intel - Chinese influence operations are growing more aggressive, more similar to Russia's - Cyberscoop, 08 Mar 23
- Article: In Espionage Thrillers, Emotional Intelligence Matters, Too - former CIA Targeter writes in Publishers Weekly, 17 Mar 23
Section IV - DEEPER DIVES, FILM, HISTORY, POP CULTURE
- Analysis: Russian Psyops in Northern Europe - Grey Dynamics, 15 Mar 23
- Audio: Havana syndrome looks very real on brain scans. Why is it still a mystery to the U.S. government? (28 min) - Apple News in Conversation, 16 Mar 23
- Backgrounder: Chinese Military intelligence - How a mammoth war machine plays spy games across the globe - First Post, 16 Mar 23
- Analysis: China's Spy Balloon Masks Espionage Iceberg in U.S. - Newsweek, 16 Mar 2023
- Analysis: Open-Source Intelligence is Indispensable for Countering Threats - National Interest, 04 Mar 2023
- Infographic and Report: Mapped - All the World's Military Personnel - Visual Capitalist, 11 Mar 22
- Intelligence in Pop Culture - Spy Movies and the Oscars with Alyssa Rosenberg - Chatter Podcast by Lawfare, 16 Mar 23
- Intelligence in History - A Collection of Recent Content
- True Intelligence Matters in Film: Turn!: Washington's Spies - Craig Silverstein (2014-2017)
- Walking Tours: The Spies of Embassy Row and Spies of Georgetown - Washington, DC. (Sundays, Dates/Times Vary)
Section V - Books, Research Requests, Academic Opportunities, Jobs, Obituaries
Books — Forthcoming, New Releases, Overlooked
- Guilty of Journalism: The Political Case against Julian Assange by Kevin Gosztola
- 'Action Likely in Pacific': Secret Agent Kilsoo Haan, Pearl Harbor and the Creation of North Korea by John Koster
- Covert Radio Agents, 1939–1945: Signals From Behind Enemy Lines by David Hebditch
Research Requests and Academic Opportunities
- Academic Opportunity: National Intelligence Summer Academy (NISA) for High School Students (17-21 July 2023) - University of North Georgia, Cumming Campus
- Call For Sources: Intelligence activities in Grenada and the southern Caribbean between 1979, Operation Urgent Fury, Leonard Barrett
- Call For Sources: Intelligence Officers Who Lived in Spain in the 1970s
- Academic Opportunity: Critical Thinking for Intelligence Analysis Course (21 Apr 23, 0800-1700 (ET) - The Intelligence and Security Academy - Virtual
- Academic Opportunity: The International Security and Intelligence Programme (9 July - 5 August 2023) - Magdalene College, Cambridge
- Call For Papers: Intelligence and Post-War Reconstruction - International Journal of Intelligence and Counterintelligence
- Search For Stories: of encounters with China's civilian and military intelligence apparatus.
- Search For Information: on CIA gallantry award recipients Bob A. Plan and Arthur J. Porn.
- Search For Information: on CIA operation against Iran in late 1990s and bomb found during President Clinton visit to Philippines in 1996
- Search For Information: on the adverse effects of diversity, equity, and inclusion on intelligence
- Call For Papers: Israel Affairs - "The Struggle in the Israeli Security Zone in South Lebanon, 1985-2000" (30 Mar 23 deadline)
- Call For Articles: AFIO Journal, The Intelligencer
- Faculty Opening - Adjunct Faculty, Intelligence Analysis - Krieger School of Arts and Sciences, Johns Hopkins University, Online
- Retired Federal Government Employees Wanted - National Security Agency, Fort Meade, MD
- Assistant Professor - Intelligence Studies (Global Security and Intelligence Studies), Embry-Riddle Aeronautical University - Prescott, Arizona
- Teaching Associate - Intelligence and National Security Studies, Coastal Carolina University, Conway, South Carolina
- Ted Speaker, Career Military Intelligence Officer
- Benedict Dichoso, Decorated DIA and ODNI Engineer and Leader
- 13 Apr 23 (Thursday), 1130 (PST) - In Person - San Francisco - CAPT Richard E. Hanson on CIA Operations in Viet Nam - Andre LeGallo Chapter
- 21 Apr 23 (Friday), 1030 (ET) - In Person - Tysons, VA - Registration Now Open for AFIO Spring Luncheon on Artificial Intelligence, Ana Montes - Code Name Blue Wren - AFIO National Event
Events from Advertisers, Corporate Sponsors, Others
- 24 Mar 23, 1200 (ET) – Sidney Reilly: Master Spy with Benny Morris – International Spy Museum Program - Virtual
- 27 Mar 23, 1630 (ET) – Discussion on The Fourth Man with Prof. John J. Quattrocki, Institute of World Politics - In-Person - Washington, DC
- 27 Mar 23, 1830 (ET) – Red London with Alma Katsu – International Spy Museum Program - Virtual
- 28 Mar 23, 1400-1500 (ET) – SPY with Me: Memory Loss Program – International Spy Museum Program - Virtual
- 29 Mar 23, 0900-1700 (ET) – How Wars End: A Conference Presented by the Pardee Center for the Study of the Longer-Range Future – Boston University - In Person
- 30 Mar 23, 1400-1500 (ET) – SPY with Me: Memory Loss Program – International Spy Museum Program - Virtual
- 13-14 Jul 23 2023 Intelligence and Security Summit – AFCEA/INSA - In Person - National Harbor, MD
See the AFIO Calendar of Events for scheduling further in the future.
ACKNOWLEDGEMENTS
The WIN editors thank the following contributors of content for this issue:
CP, FR, EB, WG, PO
Readers are encouraged to suggest material for any section of the WIN to:
winseditor@afio.com
CP, FR, EB, WG, PO
Readers are encouraged to suggest material for any section of the WIN to:
winseditor@afio.com
DISCLAIMER
Our editors include a wide range of articles and commentary in the Weekly Intelligence Notes to
inform and educate our readers. The views expressed in the articles are purely those of the authors and do not reflect support or endorsement from AFIO. WIN notices about non-AFIO events do not constitute endorsement or recommendation by AFIO.
AFIO does not vet or endorse research inquiries, career announcements, or job offers. We publish reasonable-sounding inquiries and career offerings as a service to our members. We encourage readers to exercise caution and good judgment when responding and to independently verify the source before supplying resumes, career data, or personal information.
TECHNICAL DIFFICULTIES
Readers who encounter problems with links or viewing this newsletter as an email can access
the latest web edition here.
the latest web edition here.
"How Wars End"
Wednesday, 29 March 2023
0900 - 1700 (ET)
In-Person Conference
Boston University Pardee School of Global Studies
AFIO Members are invited to attend this event. Of special interest to members are two panels: PANEL III: How intelligence Supports Diplomats in Ending Wars with Moderator: Joseph Wippl (BU Pardee School), Erik Goldstein (BU Pardee School), Amb. Thomas Simons Jr. (Former U.S. Ambassador to Poland and Pakistan) and PANEL IV: How the Afghanistan War Ended with Moderator: John Woodward (BU Pardee School), Thomas Barfield (BU Department of Anthropology).
More here about conference, other panels, and to register...
LATEST FROM AFIO
Released exclusively to members today, 21 March 2023...
The COVID-19 Intelligence Failure
Erik J. Dahl, Naval Professor/Author on
The COVID-19 Intelligence Failure: Why Warning Was Not Enough
Interview of Thursday, 2 March 2023 of Erik Dahl, Associate Professor and Author. Interviewer - Host: James Hughes, AFIO President, a former CIA Operations Officer.
TOPIC: Erik Dahl and Jim Hughes discuss Dahl's latest book, "The COVID-19 Intelligence Failure: Why Warning Was Not Enough" which explores the roles that both traditional intelligence services and medical intelligence and surveillance systems play in providing advance warning against public health threats ― and how these systems must be improved for the future. Epidemiologists and national security agencies warned for years about the potential for a deadly pandemic, but in the end global surveillance and warning systems were not enough to avert the COVID-19 disaster.
The interview runs 34 minutes and includes several Q&As.
Purchase a copy of "The Covid-19 Intelligence Failure" here.
Access the Erik Dahl interview here or click above image
This, and upcoming AFIO Now videos in 2023, are sponsored by Northwest Financial Advisors.
Registration Open
AFIO National Spring Luncheon,
Friday, 21 April 2023, 10:30 am - 2 pm EST - In-Person Tysons, VA
| Presentations by LTG Michael Groen (USMC, Ret), former Commander of the Joint Artificial Intelligence Center, discussing AI. His presentation begins at 11:00 a.m. |
 |
 |
Journalist Jim Popkin discussing Cuban Spy and DIA mole Ana Montes featured in his book, "Code Name Blue Wren: The True Story of America's Most Dangerous Female Spy―and the Sister She Betrayed." His talk starts at 1:00 p.m. "An entertaining story of cunning espionage."—Kirkus Reviews |
 |
|
Lunch served noon-1:00 p.m. Event ends 2:00 p.m. NO registrations or walk-ins at hotel. Check-in and badge pickup for Registered Attendees starts at 10:30 a.m. |
||
Luncheon prices are $55 for Members; $70 for nonmember guests and all Subscribers. Cancellation Schedule: AFIO must guarantee XX meals to the hotel; therefore, regrets it must charge a cancellation fee. 100% refund until close of registration. No refunds or cancellations after close of registration. You will receive a donation receipt for fees forfeited. A donor statement will be sent showing that you made a "gift to AFIO" in such instances. Gifts to AFIO are tax-deductible. All attendees must be members of AFIO or accompanied by a member of AFIO. To learn more about becoming a member, visit: www.afio.com. If you have any questions regarding membership, contact our office at 703-790-0320 or email us at afio@afio.com Questions regarding event? Email events@afio.com |
||
Some reactions to Popkin's "Code Name Blue Wren"
"Code Name Blue Wren might be the most mesmerizing spy story I've ever read. It shows how a brilliant manipulator secretly working for the Cubans finagled her way deep into the US military—and the anguish of the friends and family she so easily conned. Jim Popkin captures the brutal realities of modern espionage. I couldn't stop reading this." —Mark Leibovich, author of This Town and Thank You for Your Servitude
"For espionage devotees, Jim Popkin's Code Name Blue Wren is a critical read. In great detail, Popkin explores the case of Ana Montes, who became a mole in the Defense Intelligence Agency for Cuban intelligence. A mole who was almost never caught thanks to years of incompetence by the FBI's counterspies. But thanks to the dogged persistence of a dedicated NSA analyst, who bypassed the FBI at great risk to her career, Montes was arrested shortly after the 9/11 attacks. Left in her wake was the likely death of an American Green Beret killed in action in El Salvador and the pro-American troops fighting alongside him." —James Bamford, bestselling author of The Puzzle Palace and Spyfail: Foreign Spies, Moles, Saboteurs, and the Collapse of America's Counterintelligence
"Jim Popkin uncovers riveting details about one of the most damaging spy cases in US history, revealing new insights into the highly sensitive secrets that Ana Montes gave to her Cuban handlers. Through remarkably extensive interviews with her relatives and coworkers, he exposes not only what she did but why. This is the definitive history of how one of America's most highly regarded intelligence analysts betrayed her country, and how she almost got away with it." —Pete Williams, former NBC News justice correspondent
"This spy tale reads like a new season of Homeland – except this Ice Queen's traitorous double-life was entirely real. Jim Popkin takes us deep into a long-ignored story of an intel officer who went rogue, spilling US secrets to Cuba, endangering US operatives, and tricking presidents and her own sister at the FBI in the process." —Carol Leonnig, Pulitzer Prize-winning reporter at the Washington Post and author of Zero Fail: The Rise and Fall of the Secret Service

"AFIO Now" Video Interviews and Podcasts in 2023 are sponsored by
Northwest Financial Advisors
Click here to watch interviews in the AFIO Now series released in 2023.
View interviews from 2020 to 2022 here.
Watch public-release interviews on our YouTube channel or listen to them in podcast form at the links below.
Log into the member-only area for member-only features.
Latest podcast episode: Vince Houghton PhD, Director/Curator, National Cryptologic Museum, NSA, former Historian/Curator International Spy Museum and Interviewer - Host: James Hughes, AFIO President, a former Senior CIA Operations Officer, discuss the All New and Original Exhibits at the Reopened Museum.
Are you too busy to watch an entire AFIO Now episode on YouTube? Would you rather listen in your car or while accomplishing other tasks? You can download or stream episodes on any of the 8 podcasting platforms that host AFIO Now. Search for 'AFIO Podcast' for a selection of the interviews above (public released ones) on:
Podbean; iTunes; Google; Spotify; Amazon Music; Amazon TuneIn + Alexa; iHeartRadio; Pandora
Social media users, and those who wish to explore, can find or be notified about new
announcements and other material on AFIO's Twitter feed, LinkedIn
page, and YouTube channel. Access them here: LinkedIn, Twitter, and YouTube.
![]()
![]()
![]()
FROM THE AFIO STORE
 Clearance Sale on Long-Sleeved Polo Shirts with AFIO Logo
Clearance Sale on Long-Sleeved Polo Shirts with AFIO Logo
Superior quality and shrink resistant; features a detailed embroidered AFIO seal. The shirt color is royal blue.
The sale price is $25 and includes shipping.
Available in men's sizes only: small, medium, large, extra-large, XXL, and XXXL.
Due to limited quantities, please contact the AFIO National Office for availability of size and to provide payment information.
You may telephone the office at 703-790-0320 or email annettej@afio.com
Access CIA's Inhouse Gift Shop
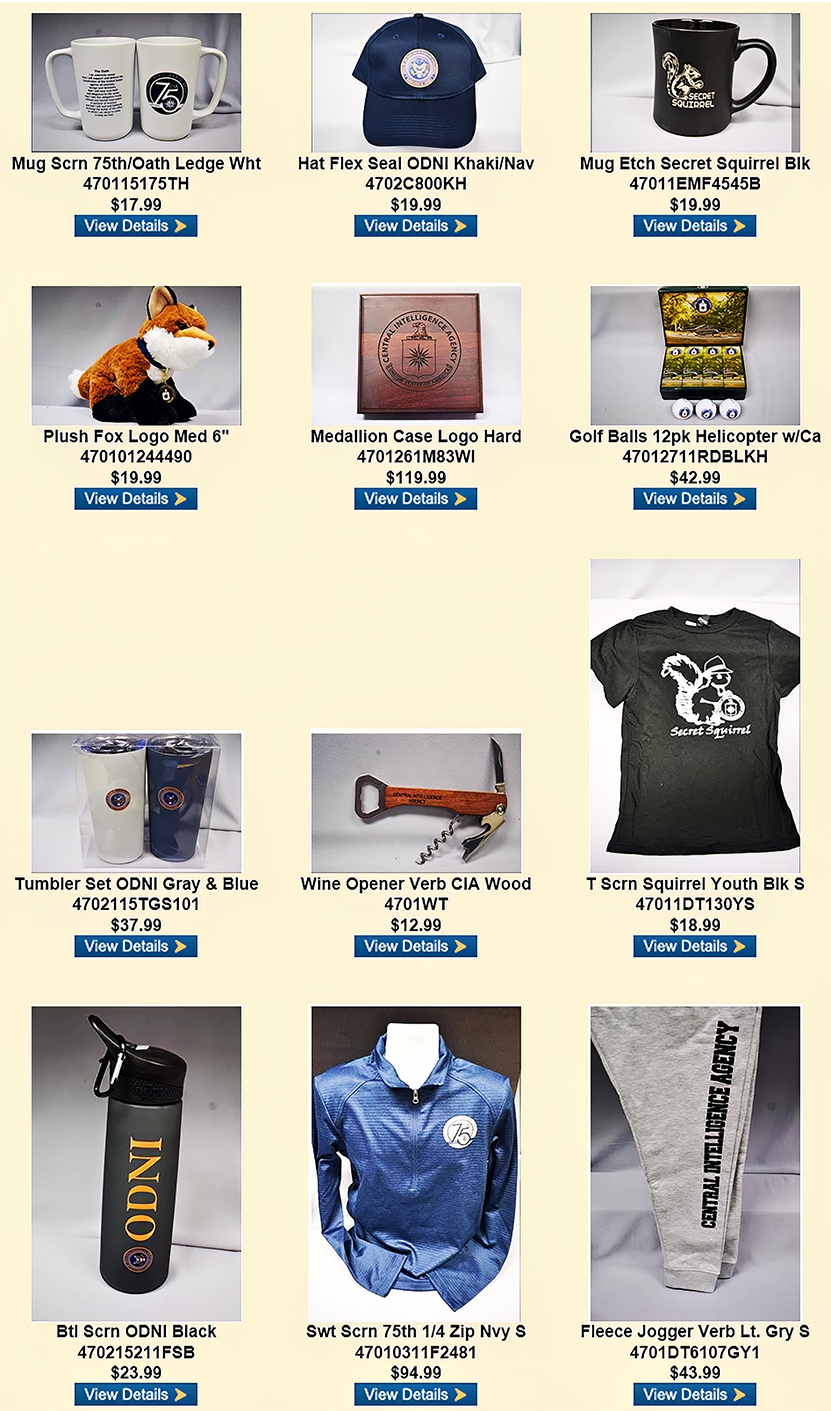
One special benefit of AFIO membership is access to CIA's EAA Store.
After completing the required, quick pre-approval process for all AFIO members, described here, you can purchase directly from the EAA online store their unusual logo'd gift items for self or colleagues. EAA on 10 February 2023 released the photo above, which features some of their newest CIA items and other gift suggestions.
Section I - CURRENT INTELLIGENCE NEWS HIGHLIGHTS
Russia's Kremlin bans iPhones as Putin's workers fear espionage threat - iMore, 20 Mar 23
Russians working on President Putin's 2024 re-election campaign have been told that they cannot use an iPhone over espionage fears. Workers have been told that they have until April 1, 2023, to get rid of their iPhones, with one official quoted as saying that "the iPhone is over." They added that workers should "either throw it away or give it to children." Officials working in the presidential administration's domestic policy, public projects, State Council, and IT departments are among those affected. Instead, they must switch to using Android-based phones. (Full article here.)
The CIA’s CTO and deputy director explain the future of spying - Fast Company, 20 Mar 23
It’s been ten months since the Central Intelligence Agency tapped Nand Mulchandani to become the agency’s first-ever chief technology officer. A veteran of both the public and private sectors, Mulchandani had most recently served as CTO and acting director of the Defense Department’s Joint Artificial Intelligence Center. Before that, he co-founded several startups including Oblix, Determina, and OpenDNS (acquired by Oracle, VMWare, and Cisco, respectively). The CIA hadn’t exactly been sitting on the sidelines of innovation prior to Mulchandani’s arrival. It played a key role advancing a number of advances, from touchscreens to magnetic resonance imaging. But the agency has also come under fire in recent years, with a number of former officers saying it’s been slow to adopt new technologies—and to pivot to combat new technological threats. (Full article here.)
Surveillance nation: India spies on world's largest population - Context, 19 Mar 23
Khadeer Khan was arrested in the south Indian city of Hyderabad in January after police claimed to have identified him from CCTV footage as a suspect in a chain snatching incident. He was released a few days later, and died while being treated for injuries he allegedly sustained while in custody. The police said Khan was arrested because he looked like the man seen in the CCTV footage. "When it was ruled out that Khadeer was not the one who had committed the crime, he was released. Everything was done as per procedure," said K. Saidulu, a deputy superintendent of police. But human rights activists say the 36-year-old was clearly misidentified - a growing risk with the widespread use of CCTV in Telangana state, which has among the highest concentrations of the surveillance technology in the country. (Full article here.)
China-backed espionage is getting harder to spot, researchers say - Axios, 17 Mar 23
Suspected China-linked hacking groups are continuing to build on a new tactic targeting internet-facing security tools as a way of stealthily breaking into some of the most data-rich organizations, researchers at Google-owned Mandiant warn. Driving the news: In a report Thursday, researchers said they've uncovered a new bug targeting software security company Fortinet, which makes firewalls, antivirus programs and similar tools. The Wall Street Journal first reported on the new bugs. (Full article here.)
DIA's New China Mission Group to Track Threat Posed by AI Development - NextGov, 14 Mar 23
Improved defense intelligence collection and analysis of emerging technologies will rely on forming new partnerships between government and industry, according to leadership at the Defense Intelligence Agency. Doug Wade, the head of the DIA's China Mission Group, spoke during a Tuesday media discussion about his agency's effort to bring together the best of industry to identify specific threats China poses and coordinate responses. Among the group's areas of concern: China's cyber capabilities and development of artificial intelligence technology. "So China is investing heavily right in its AI and ML capabilities," Wade said. "China's ability to use things like AI to ensure that they have strong…surveillance coverage of citizens, whether they're China citizens or whether they export that technology to other regimes around the world, and then those regimes use it to exert totalitarian control." (Full article here.)
YoroTrooper Espionage Campaigns Target CIS, EU Countries - OODA Loop, 16 Mar 23
The Cisco Talos cybersecurity team has identified a previously unknown threat actor conducting espionage campaigns against Commonwealth of Independent States entities such as Azerbaijan, Tajikistan, and Kyrgyzstan. The threat actor has been dubbed YoroTrooper by security researchers and has also been observed compromising accounts from at least two international organizations, including a critical European Union health care agency and the World Intellectual Property Organization. Researchers at Cisco Talos released a blog post regarding the threat actor, stating that information stolen during the course of its attacks included credentials, browser histories and cookies, system information, and screenshots. Therefore, it appears as though the group's main motivations could be intellectual gain and information access. YoroTrooper uses a Python-based, custom built information stealer in addition to commodity malware tools to conduct its attacks. (Full article here.)
Canada investigating claims of secret Chinese police stations in Montreal - Intel News, 14 Mar 23
Authorities in Canada are reportedly probing claims that the Chinese government is operating at least two "clandestine police stations" in Montreal, which allegedly monitor the activities of Chinese citizens and Canadians of Chinese origin. The announcement comes less than four months after a similar investigation took place into the alleged existence of four illegal Chinese police stations operating in the Toronto area. The investigations were sparked by a report issued in 2022 by Safeguard Defenders, a Spanish-based non-government organization that focuses on the state of human rights in China. The report, titled "110 Overseas: Chinese Transnational Policing Gone Wild", claimed that China's Ministry of Public Security, in association with Chinese diplomatic facilities, operated dozens of clandestine police stations around the world. Their official mission, according to the report, was to service the needs of Chinese citizens living abroad, as well as visitors from China. At the same time, however, these clandestine police stations were "actively […] engaging in covert and illegal policing operations" against Chinese citizens and expatriates, according to Safeguard Defenders. (Full article here.)
What's Up There, Where Is It, and What's It Doing? The U.S. Space Surveillance Network - National Security Archive, 13 Mar 23
The 65-year U.S. effort to detect and track objects in space, from the days before Sputnik 1 to today's much more crowded orbital environment, is the subject of a fascinating new article and briefing book posted today by the National Security Archive. Obtained through Mandatory Declassification Review (MDR) requests and archival research, these 25 documents reveal how U.S. policymakers conceived and built the U.S. Space Surveillance Network to detect, track and collect information on an increasingly busy and complex array of satellites and debris. Compiled and annotated by James E. David, curator of national security space programs at the Smithsonian National Air and Space Museum, and Charles Byvik, the documents trace the origins and evolution of the program, including the development, beginning in 1956, of the first cameras specifically designed to photograph and track U.S. scientific satellites. Other documents detail how in subsequent years the development of the Space Detection and Tracking System (SPADATS) greatly expanded the array of radars and optical sensors to keep up with the ever-increasing number of space objects, especially Soviet military satellites, which represented a potential threat to national security (Full article here.)
Ethnic Uyghurs Forced to Confront Foreign Influence Concerns - Clearance Jobs, 19 Mar 23
Obtaining a security clearance with relatives, financial interests, or other personal connections in China has been a challenging endeavor in recent years under the best of circumstances. As China has moved to supplant the U.S. as the dominant world super-power, the Chinese Communist Party has become increasingly bellicose and the Chinese intelligence services increasingly brazen. U.S. government personnel security officials well know this, and they view any clearance-applicant ties with China as a serious risk. Until the Chinese government broke their commitment to the United Kingdom and effectively invaded Hong Kong, clearance applicant ties there were generally viewed with somewhat lessened skepticism. That distinction has since evaporated, just as we're now learning it also has for ethnic Uyghurs. (Full article here.)
GCHQ spy chiefs warn Microsoft's ChatGPT and other AI chatbots pose a security risk - Daily Mail, 15 Mar 23
Spy organisation GCHQ says Artificial Intelligence powered chatbots like ChatGPT are emerging security threats. In a blog post yesterday the National Cyber Security Centre says companies operating the technology - like Microsoft and Google - are able to read questions typed into the chatbots. The centre admits that with any emerging technology, there is always concern around how secure it is. And it advises users not to include sensitive information in queries or anything that could lead to issues if everyone saw them. The blog points out: 'The query be visible to the organisation providing the LLM (so in the case of ChatGPT, to OpenAI). (Full article here.)
Mexico probes army's use of spyware against human rights activists - NPR, 18 Mar 23
This week, lawmakers in Mexico said they would launch a federal commission to look into potential human rights abuses by the country's military. Specifically, they want to look into whether the government and military were using cellphone-based spyware to spy on human rights activists and journalists. This inquiry was set off by a report from two digital rights groups, R3D, based in Mexico, and Citizen Lab at the University of Toronto. These groups work to protect privacy and human rights in the digital space. Dina Temple-Raston is host of "Click Here." That's a podcast that focuses on cybersecurity and intelligence. She's also a former NPR correspondent who's covered these topics. And she was part of a group of journalists who got an early look at the report. And she's with us now. Welcome, Dina. (Full article here.)
'American spy' stabbed near GCHQ in alleged terrorist incident was known to her attacker - The Telegraph, 15 Mar 23
An "American spy" who was stabbed near the GCHQ base in an alleged terrorist incident, had just finished a gym session and was known to her attacker, it has emerged. The woman, who is thought to be in her 20s, was attacked shortly after leaving a leisure centre in Cheltenham last Thursday evening and sustained serious injuries. A man, who was arrested at the scene, was on Wednesday evening charged with attempted murder. Joshua Bowles, 29, is also charged with causing actual bodily harm and will appear at Westminster Magistrates' Court in central London on Thursday. Mr Bowles was initially held on suspicion of attempted murder, but was rearrested the following day under the Terrorism Act after it emerged that the victim was an American working with the National Security Agency (NSA). (Full article here.)
Defence Geospatial Intelligence (DGI) 2023 Conference - GeoConnexion, 13 Mar 23
With the threats and challenges posed by the conflict in Ukraine serving as a common theme, the main opening day of the conference saw speakers emphasising the need to keep pace with the technologies being leveraged by our adversaries. This imperative was reiterated by Shelby Pierson, Deputy Director of the Source Operations and Management Directorate of the U.S. National Geospatial-Intelligence Agency (NGA), who singled out automation, Machine Learning and computer vision as prime examples. "Our adversaries are also investing in GEOINT collection techniques at an alarming pace," she added. Addressing an 800-strong audience, Pierson stressed the importance of adapting in order to meet these threats head-on. "We find ourselves in an operational environment very different from the one to which we have been accustomed. As such, we must move away from an 'all the data all the time' mentality and towards an integration-ready mindset which ensures users of GEOINT can hit the ground running in any required direction. To put it bluntly, we are out of time and out of runway to give those users the capabilities they need at the speed, precision and accessibility necessary to maintain the advantage." (Full article here.)
Russian Cyberspies Abuse EU Information Exchange Systems in Government Attacks - OODA Loop, 17 Mar 23
An advanced persistent threat group with links to Russia known as APT29 has been observed leveraging legitimate information systems used by European countries to conduct cyber espionage abuse. The group is believed to be sponsored by the Russian Foreign Intelligence Service and has also been referred to as Cozy Bear, the Dukes, Nobelium, and Yttrium. BlackBerry reported that the recent campaign aimed to target EU government organizations via phishing emails containing malicious documents. The phishing emails contained information about the Polish Foreign Minister’s visit to the US to lure recipients into clicking malicious links. BlackBerry also stated that the attacks abused multiple legitimate systems such as LegisWrite and eTrustX, which are used for information and data sharing between European government organizations. The platforms allow users to conduct secure document creation, revision, and exchange. Due to the fact that these platforms were chosen for the attacks, security researchers believe that the threat actor was specifically targeting European organizations. APT29 is likely utilizing Poland as a lure in an attempt to harm or gain intelligence on countries providing assistance to Ukraine. (Full article here.)
Counterespionage Corner - Recent Arrests, Convictions, Expulsions, and more...
- Greek authorities uncover identity of Russian spy who posed as Greek citizen - Intel News, 20 Mar 23
- Taiwan charges ex-MP and former admiral with spying for China - BBC, 17 Mar 23
- Sweden Charges 71-Year Old With Mapping Out Military Facilities - Bloomberg, 17 Mar 23
- Russian detained in Albania on espionage charges seeks political asylum - Euractiv, 15 Mar 23
Section II - REGULARLY FEATURED PODCASTS, BROADCASTS, NEWSLETTERS
The Latest National Security Topic Interview by Former Acting D/CIA Mike Morell
 Intelligence Matters: A CBS News national security podcast hosted by former CIA Acting Director and CBS News national security contributor Michael Morell.
Intelligence Matters: A CBS News national security podcast hosted by former CIA Acting Director and CBS News national security contributor Michael Morell.
14 Mar | The U.S. Invasion of Iraq: A Look at Intelligence, 20 Years Later
In this special episode of Intelligence Matters, host Michael Morell speaks with five former senior CIA officers about the agency's work before, during and after the U.S. invasion of Iraq in 2003. With personal recollections and reflections, Morell offers a candid walkthrough of what the CIA and other intelligence agencies assessed about Saddam Hussein's intentions and weapons programs in the lead-up to the invasion, how intelligence was used within the U.S. government throughout this period, and how the consequences of the CIA's missteps - as well as its successes - continue to reverberate today.
Past episodes:
07 Mar | Kristin Wood on the Intelligence Value of Open Source Data
28 Feb| Assessing Top Global Security Threats with Expert Frederick Kagan
21 Feb | Marking One Year of War in Ukraine: State Department Counselor Derek Chollet
More about Intelligence Matters by Michael Morell here.
The Latest from International Spy Museum Historian Andrew Hammond, PhD.
 Spycast is the official podcast of the International Spy Museum and hosts interviews with intelligence experts on matters of HUMINT, SIGINT, IMINT, OSINT, and GEOINT. Spycast is hosted by historian Andrew Hammond, PhD.
Spycast is the official podcast of the International Spy Museum and hosts interviews with intelligence experts on matters of HUMINT, SIGINT, IMINT, OSINT, and GEOINT. Spycast is hosted by historian Andrew Hammond, PhD.
14 Mar | "Hitler's Trojan Horse" - Nazi Intelligence with Nigel West Nigel West joins Andrew to discuss Germany's military intelligence service during WWII, the Abwehr. Nigel is known as the expert's expert on spy history."
Past episodes:
07 Mar | "Espionage and the Metaverse" - with Kathy Hackl
28 Feb | "Ukraine and Intelligence: One Year On" with Shane Harris
21 Feb | "The Espionage News Cycle" - A Conversation with SPY's Aliza Bran
The Latest Insights from Former CIA Acting Deputy Director for Operations Jack Devine.
 In Other News The proprietary analytic newsletter crafted for The Arkin Group's private clients by former CIA Acting Deputy Director for Operations Jack Devine.
In Other News The proprietary analytic newsletter crafted for The Arkin Group's private clients by former CIA Acting Deputy Director for Operations Jack Devine.
09 Mar | Emboldened by an unprecedented third term, Chinese President Xi's ambitions are inciting many firsts. In a meeting with members of the Chinese private sector in early March, President Xi accused Washington of enacting a policy of "containment" towards China- a term fraught with negative historic connotation and economic implications. This inaccurate, binary description of the relationship supports Xi's recently announced vision of a new world order, "the global civilization initiative", which unsurprisingly seeks to put China at the helm and minimize Washington. But Xi's attempts to reinvent Chinese foreign policy and capitalize on the global uncertainty stemming from the Russian invasion of Ukraine are not going unchallenged. (Full version available to AFIO members in the coming days here.)
09 Mar | Recent events demonstrate that post-Soviet states are wary of fully aligning with Putin.
Daily Analysis of Security Issues and Geopolitical Trends
 Intel Brief The Soufan Center's flagship, daily analytical product focused on complex security issues and geopolitical trends that may shape regional or international affairs. The Soufan Center was founded by former FBI Special Agent and Soufan Group CEO Ali Soufan.
Intel Brief The Soufan Center's flagship, daily analytical product focused on complex security issues and geopolitical trends that may shape regional or international affairs. The Soufan Center was founded by former FBI Special Agent and Soufan Group CEO Ali Soufan.
21 Mar | South Africa Has Emerged as a Financial Hub for ISIS in Africa
In 2022, Islamic State claimed more than 1,500 attacks across the globe, with the Middle East (Syria and Iraq) and Africa serving as the epicenters for ISIS’s terrorist violence. In the summer of 2022, in its al-Naba newsletter, ISIS highlighted Africa as the territory where it would most likely succeed in reestablishing a territorial caliphate. ISIS affiliates and networks in Mozambique, Burkina Faso, the Democratic Republic of Congo (DRC), Nigeria, and Mali were particularly active, conducting acts of terrorism directed at civilians and security services. At the same time, but less apparent, is a network of ISIS financiers based in South Africa who are fueling the violence on the continent. Indeed, in March 2022, the United States Government highlighted the financial activity of ISIS cells in South Africa that were specifically funding ISIS groups in DRCand Mozambique. (Full brief here.)
20 Mar | Is The United States a Viable Partner for Central Asia in a Strategic Competition?
17 Mar | Iraq Twenty Years after the U.S. Invasion
16 Mar | What the Chinese Spy Balloon Revealed About The U.S.
15 Mar | Ukraine War Erodes Russian Arms Sales
Analysis of Global Security Events with WTOP National Security Correspondent JJ Green
 Inside the SCIF - 16 Mar - Vladimir Kara-Murza's trial delayed, Pentagon footage of Russian jet colliding with U.S. drone, FBI Washington Field Office Chief concerns, DNI Haines' comments at hearing, Russian spies in Poland, and more...
Inside the SCIF - 16 Mar - Vladimir Kara-Murza's trial delayed, Pentagon footage of Russian jet colliding with U.S. drone, FBI Washington Field Office Chief concerns, DNI Haines' comments at hearing, Russian spies in Poland, and more...
 Target USA Podcast - 15 Mar - Jailed Kremlin Kara-Murza suffering symptoms of poisoning
Target USA Podcast - 15 Mar - Jailed Kremlin Kara-Murza suffering symptoms of poisoning
The Hunt Broadcast - 01 Mar - Taliban hunting down US collaborators
The Latest Insights from Jeff Stein and Colleagues in SpyTalk (Substack)
18 Mar | Israeli-Saudi Intelligence Ties Stirred, Not Shaken by Iran Rapprochement - Jonathan Broder
Back in 1982, Pierre Gemayel, the courtly leader of the right-wing Phalange Party, Lebanon's strongest Christian political group, made what seemed at the time to be a shrewd move. Always on the lookout for a powerful, preferably Western ally to protect Lebanon's Christians from the neighboring Arabs states and affiliated groups that often meddled in the country's internal affairs, Gemayel and his son Bashir, the Phalangist military commander, welcomed an invading Israeli army hellbent on expelling Syrian occupation forces and Palestine Liberation Organization guerillas who had taken over the southern border region. By the end of the summer, the Israelis had driven the Syrians and the PLO out of the country, and Bashir, with his father's blessing, rode the Israeli victory to Lebanon's presidency. (Full article here.)
17 Mar | Battle for the Skies Over Ukraine - Jeff Stein
Some of the biggest news from the war in Ukraine this week came out of the blue, you might say. First, there was the collision between a Russian SU-27 war plane and a U.S. MQ-9 Reaper reconnaissance drone. Then came word that Poland was transferring four MiG-29 fighter jets to Ukraine (followed on Friday by news that Slovakia plans to give its entire fleet of Mig-29s to Kyiv). We'd also learned that one of our B-52 strategic bombers had flown a provocative mission along western Russian airspace. (Full article here.)
15 Mar | Picture This: A Compelling New Photo History of a "Secret War" - Colin R. Thompson
The first thing the reader notices about the cover of Air America, Inc. is the photo of a DHC-4 Caribou cargo plane, resembling a bird of prey, talons extended, coming straight at you and looking like it's about to snatch lunch from the ground below. The next prominent thing is the seal of the Central Intelligence Agency, under which it says, "A CIA Proprietary Airline" — which is interesting itself because for years the agency denied any connection to the firm (no matter that it was an open secret). (Full article here.)
14 Mar | Bridge over Troubled Gulf Waters - Douglas London
The restoration of diplomatic ties between Iran and Saudi Arabia has garnered curious allusions of doom and gloom, if not outright shock and awe, over Israel's back channel security dialogue with the Kingdom, not to mention damage to U.S. interests in the region. The New York Times captured it as "the topsiest and turviest of developments anyone could have imagined, a shift that left heads spinning in capitals around the globe." And in a separate piece, it quoted Mark Dubowitz, chief executive of the arguably hawkish Foundation for Defense of Democracies that "Renewed Iran-Saudi ties as a result of Chinese mediation is a lose, lose, lose for American interests." (Full article here.)
10 Mar | A New TV Spy Drama Worthy of LeCarré - Peter Eisner
To support SpyTalk, subscribe here.
Section III - MEMBER CONTRIBUTIONS
Article: This Is the New Leader of Russia's Infamous Sandworm Hacking Unit - Wired, 15 Mar 23
For years, the hacking unit within Russia's GRU military intelligence agency known as Sandworm has carried out some of the worst cyberattacks in history—blackouts, fake ransomware, data-destroying worms—from behind a carefully maintained veil of anonymity. But after half a decade of the spy agency's botched operations, blown cover stories, and international indictments, perhaps it's no surprise that pulling the mask off the man leading that highly destructive hacking group today reveals a familiar face. The commander of Sandworm, the notorious division of the agency's hacking forces responsible for many of the GRU's most aggressive campaigns of cyberwar and sabotage, is now an official named Evgenii Serebriakov, according to sources from a Western intelligence service who spoke to WIRED on the condition of anonymity. If that name rings a bell, it may be because Serebriakov was indicted, along with six other GRU agents, after being caught in the midst of a close-range cyberespionage operation in the Netherlands in 2018 that targeted the Organization for the Prohibition of Chemical Weapons in the Hague. (Read full report here.)
Article: Losing Iraq Worse Than We Had To - National Review, 16 Mar 23
Iraq is a corrupt, divisive, sectarian country of little consequence because al-Qaeda has been driven beyond its borders. The war was not worth its costs. Could it have been prosecuted at less cost? Yes. With a different outcome? Most likely, no. Let me cite four takeaways from the war that lead to this conclusion, based on my decade of embedding on the battlefields with dozens of our platoons. First, in 2003, American battalions were in charge of dozens of Iraqi cities, Shiite and Sunni. Our commanders began to hold local elections, but that ground movement was stopped by Ambassador Paul Bremer, the president's envoy. Had they continued, local elections would have strengthened local centers of power, mitigating the later emergence of national, divisive political parties. General Jim Mattis, then commanding the First Marine Division, was simultaneously moving to reorganize Iraqi army units and, under new leadership, spread them out as the local security elements. Instead, Bremer dissolved the Iraqi army, leaving U.S. forces as the de facto police. (Read full report here.)
Article: The story behind spies and The Fourth Man - Santa Barbara News Press, 18 Mar 23
One of the more curious episodes during my tenure as Prince Albert's spymaster in Monaco was a Russia-based spy-net we codenamed The Oracle System, brought to us by a former senior officer of the CIA's clandestine service who had retired after a 30-plus year career, capped as a division chief. It was the mid 1990s and Benedict (not his real name) did as many former CIA veterans do upon departing the Agency: Venture into private-sector intelligence and risk analysis firms to utilize their very particular set of skills for corporate clients. A whole coterie of career senior CIA officers flew the coop through the 1990s amid contentious relationships with Directors John Deutch, James Woolsey and George Tenet. Morale was almost as low at CIA during that decade as it was among the Russian special services. The Cold War had supposedly ended and 9/11 had not yet happened to reenergize the Agency for its new mission: to crush Islamic terrorism (to the exclusion of almost all else). (Full article here.)
Article: 'The Hunt for Red October' Is Based on This Real Soviet Mutiny - Military.com, 17 Mar 2023
In the 1990 film "The Hunt for Red October," a Soviet Navy captain who is disenchanted with the Soviet system defects to the United States with a new, secret submarine propulsion system. Freedom beats communism, once again. One Soviet Navy officer in the mid-1970s didn't think the Soviet Union practiced anything like what communism was supposed to be. He decided he would steal a ship, but defecting to the United States was the last thing on his mind. He wanted to start another communist revolution, right in the heart of the Soviet Union. Tom Clancy was an insurance salesman when he read about Soviet captain 3rd Rank Valery Sablin. Sablin's story inspired him to write a book that would propel Clancy to literary stardom while introducing his most beloved character, Jack Ryan. "The Hunt for Red October" hit the bookshelves in 1984, but Sablin was long dead by then. (Full article here.)
Article: Entire Russian spy network dismantled in Poland - BBC, 16 Mar 23
Poland has charged six foreign citizens with preparing acts of sabotage and spying for Russia, interior minister Mariusz Kaminski has said. Mr Kaminski said the six were "foreigners from across the eastern border" and they had sought to disrupt military and aid supplies to Ukraine. Prosecutors are currently preparing proceedings against three other people also detained in the operation. Mr Kaminski said the cell had been preparing "sabotage actions" in Poland. "Evidence indicates that this group monitored railway lines. Their tasks included recognising, monitoring and documenting weapons' transports to Ukraine," Mr Kaminski told a news briefing on Thursday morning. "The suspects were also preparing sabotage actions aimed at paralysing the supply of equipment, weapons and aid to Ukraine." Six of the suspects have been charged with conducting espionage for Russia and participation in an organised criminal group, after they were detained as part of an operation conducted by Poland's Internal Security Agency (ABW). (Full article here.)
Article: Alleged Russian spy and sabotage cell busted in Poland - Intel News, 16 Mar 23
Nine members of an alleged Russian saboteur cell have been arrested in Poland, according to media reports and official acknowledgments by Polish authorities. Early reports on Wednesday afternoon local time centered on the arrests of six nine individuals, who were detained on suspicion of conducting espionage and planning sabotage attacks against various elements of transportation infrastructure. Radio station RMF24 FM reported that the six nine individuals were detained following a number of early-morning raids conducted by the Polish Internal Security Agency (ABW), which is the country's primary counterintelligence and counterterrorism organization. At least some of the six nine individuals are reportedly Belarusian nationals who were active in Poland's southeastern Podkarpackie Voivodeship, a largely rural province that borders Ukraine's Lviv Oblast. Later on Wednesday, the RMF24 FM report was confirmed by Polish government officials, who spoke to the BBC. Notably, the Podkarpackie Voivodeship is home to the Rzeszów–Jasionka International Airport, located near the village of Jasionka, which is approximately 60 miles, or 100 kilometers, from the Ukrainian border. Since the February 2022 Russian invasion of Ukraine, this provincial airport has been transformed into a major logistical gateway for the transportation of Western military and humanitarian aid to Ukraine. Dozens of Western aircraft land there every day, carrying supplies that are then loaded onto trucks or trains en route to Ukraine. (Full article here.)
Article: How many Russians have been killed in Ukraine? - Economist, 08 Mar 23
Nearly 1,200 Russian soldiers were recently killed in a single day around Bakhmut, according to Mark Milley, America's top general, in an interview with Politico, a news website. "That's Iwo Jima," he reflected, referring to a brutal 36-day Pacific battle during the second world war. "That's Shiloh"—a battle in the American civil war. A recently published paper offers a new assessment of the extraordinary losses Russia is facing in Ukraine (see chart). (Full article here.) Note: Content may be behind a paywall or require a onetime free registration.
Article: A Spy Wants to Connect With You on LinkedIn - Wired, 15 Mar 23
There is nothing immediately suspicious about Camille Lons' LinkedIn page. The politics and security researcher's profile photo is of her giving a talk. Her professional network is made up of almost 400 people; she has a detailed career history and biography. Lons has also shared a link to a recent podcast appearance—"always enjoying these conversations"—and liked posts from diplomats across the Middle East. So when Lons got in touch with freelance journalist Anahita Saymidinova last fall, her offer of work appeared genuine. They swapped messages on LinkedIn before Lons asked to share more details of a project she was working on via email. "I just shoot an email to your inbox," she wrote. (Full article here.)
Article: US intel - Chinese influence operations are growing more aggressive, more similar to Russia's - Cyberscoop, 08 Mar 23
U.S. intelligence officials warned on Wednesday that China is stepping up its efforts to carry out influence operations against the United States and that its efforts to influence American public opinion increasingly resemble Russian operations. In testimony before the Senate Intelligence Committee and in the U.S. intelligence community's annual threat assessment published on Wednesday, U.S. intelligence leaders cautioned that China represents perhaps the leading threat to U.S. power and that the conflict between Washington and Beijing is increasingly playing out along technological lines. "The People's Republic of China, which is increasingly challenging the United States economically, technologically, politically and military around the world, remains our unparalleled priority," Director of National Intelligence Avril Haines said during her testimony on Wednesday before the Senate Intelligence Committee during its annual worldwide threats hearing. (Full article here.)
Article: In Espionage Thrillers, Emotional Intelligence Matters, Too - former CIA Targeter writes in Publishers Weekly, 17 Mar 23
When you work at the CIA, you're taught to keep everything you do secret. You must be invisible. As a woman who grew up in a patriarchal family, I was not unfamiliar with the imperative. So it felt dicey when I decided to make public that I worked at the CIA and was writing a book on the subject. Being exposed and vulnerable was unsettling, but with this exposure also came freedom. I started working at the CIA shortly after 9/11. In the years that followed, there was an immediacy and relevance to the counterterrorism mission that is difficult to quantify. In 2005, I was assigned to support the CIA's mission in Iraq. As a CIA targeting officer, my days were spent hunting elusive high-value targets, which typically meant high-ranking members of a Sunni extremist group. In 2010, I graduated to hunting targets in the CIA's Pakistan Afghanistan division—not just in support of the CIA's capture/kill operations but also targeting for the potential recruitment of sources. These were challenging tasks in my 20s and early 30s—navigating both the war zones in the Middle East and the male-dominated vaults at Langley. (Full article here.)
Section IV - DEEPER DIVES, FILM, HISTORY, POP CULTURE
Analysis: Russian Psyops in Northern Europe - Grey Dynamics, 15 Mar 23
Russian Strategic Psychological Operations (Psyops), specifically information operations, have an important place in the Kremlin's foreign policy and Russian military strategy. Russia is conducting psyops on a global scale. Still, the war in Ukraine, the increasing attention to the Arctic region, and the Swedish and Finnish applications to NATO are all factors which increase strategic value in psyops targeting Northern Europe. Psyops are mainly operations intending to influence an adversary's emotions and motives to shape the behaviour of governments, organisations, groups, and individuals. Strategic psyops mainly focus on shaping narratives through disinformation campaigns and other types of influence operations, encouraging popular discontent and degrading an adversary's ability to maintain unity at domestic and foreign policy levels. Strategic psyops constitute a desirable alternative to inflicting harm on an opponent below the threshold of war. Looking at the influence operations element of psyops, these are the coordinated covert activities initiated by a state actor to influence decision-making, perceptions, and policy-objectives of influential actors such as experts and media outlets in opponent states. Such operations aim to achieve foreign policy objectives through tailored disinformation campaigns. (Full report here.)
Audio: Havana syndrome looks very real on brain scans. Why is it still a mystery to the U.S. government? (28 min) - Apple News in Conversation, 16 Mar 23
In 2016, U.S. government officials began reporting a mysterious set of symptoms. They first appeared in Havana, but then showed up in other countries around the world. In a podcast for Vice World News, reporters Adam Entous and Jon Lee Anderson explain everything they've learned about what's now commonly called Havana syndrome, and why the U.S. still can't explain what causes it. On this week's episode of Apple News In Conversation, Entous and Anderson discuss their reporting with host Shumita Basu. (Listen here.)
Backgrounder: Chinese Military intelligence - How a mammoth war machine plays spy games across the globe - First Post, 16 Mar 23
One of the key elements of the Chinese espionage network is the military intelligence that it has been able to keep under wraps. What we are witnessing is a new avatar of Chinese Military intelligence under President Xi Jinping who as a head of the Central Military Commission directly controls the Chinese military. He started restructuring the Chinese military in 2015-16 and that also included revamping of the Chinese military intelligence network. Peter Mattis explained the importance and implications of this exercise of Chinese espionage network in China reorients strategic military intelligence (Janes, 2017), "On 26 November 2015, Chinese president Xi Jinping announced the first significant revision of the People's Liberation Army (PLA) since its reorganisation during the 1950s, when the PLA transformed from an army fighting a civil war to one capable of protecting a nation-state. The reforms removed the Soviet-inspired system of general departments, established a new division of labour, and realigned the PLA organisationally to better fulfill the Military Strategic Guidelines that state the goal of winning informationised local wars." (Full report here.)
Analysis: China's Spy Balloon Masks Espionage Iceberg in U.S. - Newsweek, 16 Mar 2023
In the middle of February, a week after an American fighter jet downed China's spy balloon off the Atlantic coast, a diplomat at its foreign ministry sought to turn the fiasco on its head by accusing the United States of launching airships over Chinese territory, too. After flat denials by seniors U.S. officials, the Chinese spokesperson, who when asked for Beijing's evidence referred reporters to Washington instead, then complained that the Americans had refused to share details of the balloon debris, which was being examined "behind closed doors." "What gives such an investigation credibility anyway?" he asked, in what was the extent of China's attempt to save face. Beijing's refusal to concede any wrongdoing was par for the course, subject-matter experts said. In the meantime, the White House must juggle a red-faced adversary with an expectant public when it decides how much to reveal about the recent findings. The information could solve curiosities including the extent to which China relies on its dirigible program for intelligence, surveillance and reconnaissance, as well as how exactly Chinese leader Xi Jinping was convinced of the utility of a balloon with seemingly limited maneuverability. (Full report here.)
Analysis: Open-Source Intelligence is Indispensable for Countering Threats - National Interest, 04 Mar 2023
When most people hear the word intelligence in a political context, they immediately think of clandestine sources, spies, and secret meetings. Intelligence services still rely on human source intelligence (HUMINT) and intercepted communications (SIGINT). However, in the twenty-first century, open-source intelligence (OSINT) has become indispensable for understanding your adversaries and is often the primary and most valuable source of actionable intelligence. According to a detailed article highlighting the power of OSINT in the Wall Street Journal, “80% of what a U.S. president or military commander needs to know comes from OSINT.” What then is OSINT, and why is it so important in 2023? (Full report here.)
Infographic and Report: Mapped - All the World's Military Personnel - Visual Capitalist, 11 Mar 22
While much of the world is living in one of the most peaceful periods in history, the spark of new conflicts like Russia's invasion of Ukraine reminds us of the importance of military personnel. Between ongoing armed conflicts to building of defenses preemptively, many countries have amassed significant militaries to date. This map, using data from World Population Review, displays all the world's military personnel. (Access visual tool and full report here.)
The Academy loves a good spy flick, and so do we! This week, Shane talks with Washington Post culture critic Alyssa Rosenberg about the enduring power of espionage on the big screen. Movies like Zero Dark Thirty, the Mission: Impossible franchise, and this year's Top Gun: Maverick and All Quiet on the Western Front, which both took home Oscars, help us understand global conflict as they wrestle with questions of personal morality. How do the stories of James Bond and George Smiley help us make sense of the fate of nations? And why is Hollywood finding it nearly impossible to tell stories about great power competition between the U.S. and China? Shane and Alyssa go way back, and this is a fun, lively conversation about spy stories that have resonated through the decades. Alyssa has written for years about popular culture, books, and more recently parenting. (Listen here.)
Intelligence in History - A Collection of Recent Content
- Article - When MI6 betrayed Ukraine’s resistance to Russia - Declassified UK, 16 Mar 23
- Article - Vicky Peláez - Journalist and Spy, 16 Mar 23
- Article - Tiny American Mugshots of the Anti-Espionage Age - Messy Nessy Chic, 15 Mar 23
- Audio - Hemingway and the NKVD with Dr. Frederick H. White (73 mins), Spycraft 101, 05 Mar 23
- Audio - Sax and the Spy (34 mins), DIA Connections Podcast, 13 Mar 23
- Article - The poison umbrella: film sheds new light on infamous cold war killing - The Guardian, 17 Mar 23
True Intelligence Matters in Film - Turn!: Washington's Spies - Craig Silverstein (2014-2017)
 This AMC original drama series follows Long Island farmer Abe Woodhull, who bands together a group of childhood friends to form The Culper Ring, an unlikely group of spies who turn the tide in America's fight for independence.
This AMC original drama series follows Long Island farmer Abe Woodhull, who bands together a group of childhood friends to form The Culper Ring, an unlikely group of spies who turn the tide in America's fight for independence.
More information about this based-on-true-events production here.
Walking Tours - Washington, DC - Sundays (Dates/Times Vary)
Former intelligence officers guide visitors on two morning and afternoon espionage-themed walking tours: "Spies of Embassy Row" and "Spies of Georgetown." For more information and booking, click here or contact rosanna@spyher.co
Section V - Books, Research Requests, Jobs, Obituaries
Books — Forthcoming, Newly Released, Overlooked
 Guilty of Journalism: The Political Case against Julian Assange
Guilty of Journalism: The Political Case against Julian Assange
by Kevin Gosztola
(Seven Stories Press, 07 Mar 23)
From an acclaimed independent journalist, this carefully-documented analysis of the government's case against Julian Assange and its implications for press freedom acts as a crucial, compelling guidebook to Assange's upcoming trial. The legal action against Julian Assange is poised to culminate in a trial in the United States in 2023, and this book will help the public understand the proceedings. The establishment media's coverage of WikiLeaks founder Julian Assange's extradition case has focused on his deteriorating health and what CBS News called his "secret family," but most of this coverage failed to detail the complex issues at stake against Assange. Guilty of Journalism outlines how WikiLeaks exposed the reality of American wars, the United States government's unprecedented indictment against Assange as a publisher, and the media's role in persuading the public to "shoot the messenger." This new book by Kevin Gosztola, who has spent the last decade covering Assange, WikiLeaks, and the wider war on whistleblowers, tells the full story based on testimony from dozens of witnesses. Itexamines abuses of power by the CIA and the FBI, including a spying operation that targeted Assange's family, lawyers, and doctors. Guilty of Journalism offers a balanced and comprehensive perspective on all the events leading up to what press freedom advocates have called the trial of the century.
Order book here.
 'Action Likely in Pacific': Secret Agent Kilsoo Haan, Pearl Harbor and the Creation of North Korea
'Action Likely in Pacific': Secret Agent Kilsoo Haan, Pearl Harbor and the Creation of North Korea
by John Koster
(Amberley Publishing, 15 Nov 19)
Pre-WW2, Kilsoo Haan repeatedly warned the United States about Japanese attacks and accurately supplied every conceivable detail: midget submarines as well as aircraft at Pearl Harbor, giant submarine aircraft carriers on the high seas that almost bombed San Diego with plague germs until Tojo canceled the air strike, and a joint Chinese-Japanese attack – Operation Ichi-Go – against the American and Chinese Nationalist forces, which drove through Chiang Kai-shek's much larger army. When US political bungling helped to create a Communist North Korea, Haan continued to supply information about Soviet nuclear tests in Siberia, the development of Soviet guided missiles, and the North Korean invasion of the Republic of Korea, which led to thousands of American and British casualties. He was ignored. The story of American influence in Korea and dealings with Japan provides a little-known background to the Pacific War and remains a factor today in international politics.
Order book here.
 Covert Radio Agents, 1939–1945: Signals From Behind Enemy Lines
Covert Radio Agents, 1939–1945: Signals From Behind Enemy Lines
by David Hebditch
(Pen and Sword Military, 23 Mar 23 in paperback (original hardback released 04 Mar 21))
Clandestine radio operators had one of the most dangerous jobs of World War 2. Those in Nazi-occupied Europe for the SOE, MI6 and the OSS had a life-expectancy of just six weeks. In the Gilbert Islands the Japanese decapitated 17 New Zealand 'Coastwatchers'. These 'behind the lines' highly skilled agents' main tasks were to maintain regular contact with their home base and pass vital intelligence back. As this meticulously researched book reveals, many operators did more than that. Norwegian Odd Starheim hijacked a ship and sailed it to the Shetlands. In the Solomon Islands Jack Read and Paul Mason warned the defenders of Guadalcanal about incoming enemy air raids giving American fighters a chance to inflict irreversible damage on the Japanese Air Force. In 1944 Arthur Brown was central to Operation Jedburgh's success delaying the arrival of the SS Das Reich armored division at the Normandy beach-heads. The author also explains in layman's terms the technology of 1940s radios and the ingenious codes used. Most importantly, Covert Radio Agents tells the dramatic human stories of these gallant behind-the-lines radio agents. Who were they? How were they trained? How did they survive against the odds? This is both a highly informative and uplifting work about unsung heroes.
Order book here.
Research Requests and Academic Opportunities
Academic Opportunity: National Intelligence Summer Academy (NISA) for High School Students - 17-21 July 2023 - University of North Georgia, Cumming Campus
Are you considering a career in the U.S. Intelligence Community? Did you know that the U.S. Intelligence Community is made up of 18 separate agencies? Sign up for an intense and exciting five days of learning from highly qualified Master's and Ph.D. University of North Georgia instructors and practitioners. Application deadline 15 Apr 23. (More information and registration here.)
Call for Sources: Intelligence Officers Who Lived in Spain in the 1970s
Spanish journalist Francisco Jiménez is preparing a documentary about the intelligence services in Spain in the 70s. He is looking for intelligence officers who worked in Spain in those years. If you are willing to assist Franciso, he can be reached at fjimenez@globomedia.es.
The Washington Post is developing a multipart audio documentary series (i.e. podcast) chronicling the Grenadian revolution and the US intervention in 1983. They've interviewed nearly 100 people so far, ranging from the heads of state, former Grenadian officials, current and former US officials, veterans, and intelligence officers. They're looking for people who served at the time and may be knowledgeable about intelligence activities in Grenada and the southern Caribbean between 1979 and Operation Urgent Fury. They would also be interested in speaking with anyone who knew Leonard Barrett during the same period. If anyone is interested in participating, please reach out to Washington Post reporter Ted Muldoon via email at ted.muldoon@washpost.com or on Signal at 651-497-5449.
Academic Opportunity: Critical Thinking for Intelligence Analysis Course - 21 Apr 23, 0800-1700 (ET) - Virtual
This course will help Intelligence Analysts improve their critical thinking skills. It begins by reviewing the basic characteristics of quality intelligence analysis (and the challenges to producing it) and the methodology for building an analytic argument. The course continues with a discussion of the mental traits and habits that inhibit critical thinking and objectivity. Finally, the course discusses several types of structured techniques designed to inject critical thinking and analytic rigor into intelligence production. $600 fee. (More information and registration here.)
Academic Opportunity: The International Security and Intelligence Programme - 9 July to 5 August 2023 - Magdalene College, Cambridge
Chaired by Sir Richard Dearlove the former Chief of the British Secret Intelligence Service, the Cambridge Security Initiative (CSi) launched the ISI Programme in 2016. The purpose of this unique programme is to provide an opportunity for participants to meet and work with leading academics and practitioners from the intelligence and security communities in the historic setting of one of the world's foremost universities. The Programme is run in partnership with the Department of War Studies at Kings College, London. (More information and registration here.)
Call for papers: Intelligence and Post-War Reconstruction - International Journal of Intelligence and Counterintelligence
History shows that without planning for post-war reconstruction, apparent victory in war can lead to long-term defeat. On the other hand, wise post-war planning can lead to friendly, peaceful, and profitable relations between victor and vanquished. For political, socio-economic and security-related planning, intelligence plays a crucial role in estimating capabilities, securing infrastructure, locating persons of interest, and rebuilding. In honor of the 75th anniversary of the European Recovery Program (Marshall Plan) after the Second World War, the editors are particularly interested in papers dealing with intelligence concerning post-war reconstruction initiatives and planning connected to historical and recent conflicts. Both case studies and theoretical and methodological approaches are welcome. The studies may include, but do not have to be focused on, the following questions and issues:
- The role of diplomatic and military intelligence during the conflict as preparation for post-war reconstruction, from the conceptual to the practical.
- What intelligence needs to be collected to secure and boost reconstruction?
- What contacts, networks, and infrastructure are necessary for intelligence to be effective?
- Who has been or should be approached and/or recruited for reconstruction efforts based on intelligence?
- When has intelligent post-war planning (or its opposite) been historically evident?
- How should intelligence interact with formerly warring parties and international organizations to empower practical reconstruction efforts?
- What intelligence collection challenges have services encountered in working for post-war peace?
- How did intelligence factor in the European Recovery Program?
- What was George C. Marshall's position on the role of intelligence in general or concrete examples related to "his" plan?
01 Nov 23 deadline. More information and submission instructions here.
Search for stories: Matt Brazil, an AFIO member in the San Francisco Chapter and co-author of Chinese Communist Espionage, An Intelligence Primer (Naval Inst. Press, 2019) is writing a second work on Beijing's worldwide espionage and influence offensive. As part of that effort, he seeks interesting stories of encounters with China's civilian and military intelligence apparatus. If you are interested in telling your story or you know someone who would be, Matt can be reached via matthew.brazil@gmail.com or his website www.mattbrazil.net.
Search for information: Author and AFIO member Toby Harnden is researching recipients of CIA gallantry awards (DCI's OPA is assisting). Harnden is eager to speak to anyone with memories of, information about, or pointers toward Bob A. Plan and Arthur J. Porn. Plan was born in Croatia in 1920 and served with the OSS in Yugoslavia 1944-45. He became a CIA contractor, working as a career agent and translator, and was based in Greece in the 1950s and Mexico in the 1960s. He was parented by EUR Division when he came out of retirement to enter Tehran in 1980. Porn, born in 1930, was a WH case officer from 1958 who was based in Argentina, Honduras and Bolivia in the 1960s and 1970s. He was honored for an act of bravery in Bolivia in 1970. Please contact tobyharnden@gmail.com or 202-213-3775.
Search for information: Searching for information on a CIA "intelligence operation" carried out during the Clinton administration in 1997 or 1999 aimed at Iran and/or its MOIS in response to Iran's involvement in the 1996 Khobar Towers bombings. Clinton's counterterrorism chief Richard Clarke made a brief reference to this operation on p. 129 of his book Against All Enemies; George Tenet made a possible reference to this operation on p. 124 of his book At the Center of the Storm; and Bruce Riedel posted a reference to it here in his article "The Iran Primer: The Clinton Administration." He called it "Operation Sapphire" - not to be confused with Operation Sapphire aimed at Kazakhstan. Also, searching for information on a bomb found on a bridge in Manila, Philippines around November 23, 1996 when President Clinton was in the city. Contact: dpluchinsky@rocketmail.com.
Search for information: Dr John Gentry of Georgetown University seeks information on what ways, to what extent, at what agencies, and with what implications/consequences are DEI (diversity, equity, inclusion) policies damaging the IC and DOD. Request examples and assessments that link senior-level policies, and middle managers' interpretations of them, to specific organizational and personal actions and then to actual consequences in sufficient volume and detail to be able to make a coherent argument. Anonymity assured. Contact: jag411@georgetown.edu.
Call For Papers: The Struggle in the Israeli Security Zone in South Lebanon, 1985-2000, Israel Affairs
In June 1985, the Israel Defense Forces (IDF) de jure completed its withdrawal from Lebanon to the Israeli borders. De facto, Israel left in its hands a strip of land, about 15 kilometers from its border, in which its ally, the South Lebanon Army (SLA), operated. This strip of land came to be known as the Israeli Security Zone. The idea was that the SLA would be almost independent, while the IDF would intervene only when necessary in the battle against Palestinian and Shiite groups and supervise the SLA. Soon, however, the IDF became more involved, building military posts within the Security Zone, reinforcing itself, and encountering new challenges. In May 2000, Israel pulled its forces back to its borders and the SLA collapsed, along with the Security Zone. The 15 years of fighting in the Security Zone were rarely mentioned within Israeli society, let alone in the academic sphere. Only in recent years has the Israeli public become aware of this period after many soldiers who served in the Security Zone began sharing their memories through books and social media. The campaign to raise awareness of the period successfully ended when in March 2021, Israel officially recognized this period as one of warfare. This special issue aims to interdisciplinarily bridge the gap in the academic discourse regarding the war in the Security Zone. The editors are interested in articles dealing with various topics concerning the 1985-2000 war in the Security Zone. 30 March 2023 deadline. For more information, including submission instructions and suggested topics, click here.
Call For Articles: AFIO Journal, The Intelligencer
For the past four years, AFIO has included in The Intelligencer a series of articles on "when intelligence made a difference." Written by scholars, intelligence practitioners, students, and others, they cover events from ancient times to the modern world and in many countries. AFIO is soliciting articles for future issues. Most articles run between 2,000 and 3,000 words, although some are longer or shorter. If you have an idea for an article that fits the theme, email senior editor Peter Oleson at peter.oleson@afio.com.
Jobs
Faculty Opening - Adjunct Faculty, Intelligence Analysis - Krieger School of Arts and Sciences, Advanced Academic Programs, Johns Hopkins University, Online
The Advanced Academic Programs (AAP) division seeks non-tenure track adjunct faculty to teach several courses within the MS in Intelligence Analysis program. The course(s) will be taught fully online beginning in Summer 2023 and beyond. Candidates with online course development and teaching experience and those with experience teaching and engaging students from diverse backgrounds are of particular interest. Full details and online application instructions can be found here.
Retired Federal Government Employees Wanted - National Security Agency - Fort Meade, Maryland
The National Security Agency (NSA) may occasionally need skilled civilian retirees to augment the existing work force on high priority projects or programs. In order to fill these temporary positions quickly, we need to know who may be interested and available to return to work with us on a short notice basis as well as their skills. Retirees provide expertise and corporate knowledge to temporarily support mission requirements, manpower shortfalls, and/or mentor the next generation of Agency employees. Salary Range: $86,335 - $170,800.
Additional information and application here.
Assistant/Associate Professor of Intelligence Studies (Global Security and Intelligence Studies) - Embry-Riddle Aeronautical University - Prescott, Arizona
Embry-Riddle Aeronautical University's Prescott, Arizona campus is accepting applications for a tenure-track assistant or associate-level professor of intelligence studies to teach intelligence courses to students in the Global Security and Intelligence program. The successful candidate will teach students about the intelligence community, strategic intelligence, the intelligence cycle and intelligence analysis, writing, and briefing. Prior experience working in the intelligence community is strongly preferred. We are interested in candidates with teaching acumen in intelligence analysis and writing using structured analytical techniques.
Additional information and application here.
Teaching Associate - Intelligence and National Security Studies - Coastal Carolina University, South Carolina
The Department of Intelligence and Security Studies ( ISS ) at Coastal Carolina University is accepting applications for a pool of Teaching Associates (part-time adjunct faculty) to teach introductory and undergraduate elective course offerings for the program beginning in August 2022. While the ad is open to any specialization within the field of study, courses in the areas of homeland security, law enforcement intelligence, counter-narcotics, and cybersecurity are of particular interest. Course offerings can be in a face-to-face or synchronous online modality. To be considered, candidates must have a masters or doctoral degree in a relevant subject area. Prior professional experience in the profession, as well as prior teaching experience are preferred.
Additional information and application here.
Obituaries
![]() Ted Speaker — Career Military Intelligence Officer
Ted Speaker — Career Military Intelligence Officer
Dr. Edwin "Ted" Ellis Speaker, 95, passed away on Friday February 24, 2023 in Mount Pleasant, SC. Born in Washington, DC., he attended the Staunton Military Academy in Virginia, serving his last year as the Cadet Regimental Commander. He won a competitive appointment to the US Naval Academy. Upon graduation from the Naval Academy in 1950, he was commissioned a Second Lieutenant in the US Air Force. During the Korean War, Ted was stationed in Japan and Korea. He held numerous assignments in missile and space R and D at Cape Canaveral, and later worked in scientific and technical intelligence at the Pentagon. He retired as a Lieutenant Colonel in 1970. After retiring from the Air Force, Ted joined the Rand Corporation in Washington, DC, where he supported HQ USAF with strategic war game analysis. He then returned to government service as an executive in the Defense Intelligence Agency, where he directed intelligence research programs in analysis of foreign weapons systems. These studies contributed to important National Intelligence Estimates used in the Strategic Arms Limitation Talks (SALT) and in the formation of national defense policies. Ted went on to work at the NASA Goddard Space Flight Center, where he was Project Manager for LandSat, an earth-observing satellite reconnaissance system. He was selected to be on the NASA Planning Team for the International Space Station (ISS) program which was approved by President Reagan in 1984. Moving to NASA's newly formed Headquarters Program Office, Ted was Chief of Plans Integration for the ISS. After retiring a second time from government service Ted moved to Satellite Beach, Florida, where he taught graduate space science courses for Florida Institute of Technology. Ted earned a master's degree from the Massachusetts Institute of Technology and a Doctorate in Aerospace Engineering from the University of Michigan. He was a Fellow and past president of the American Astronautical Society, an Associate Fellow of the American Institute of Aeronautics and Astronautics, was a member of the Association for Intelligence Officers, Military Officers Association of America, Phi Kappa Phi, Sigma Xi, and the NRA. Internment is expected to be at Arlington National Cemetery in Arlington, Virginia.
![]() Benedict Dichoso — Decorated DIA and ODNI Engineer and Leader
Benedict Dichoso — Decorated DIA and ODNI Engineer and Leader
Benedict Oliver Dichoso Jr. - Age 53 of Dumfries, Virginia, passed away after a long-term illness on March 4, 2023. Ben was born in Washington, D.C. and graduated from St. John's College High School and Virginia Polytechnic University as a member of the Corps of Cadets with a Bachelor's and Master's degree in civil engineering. He was commissioned an officer in the U.S. Air Force in 2002 and served on active duty for 6 years. He then accepted a position as a civilian civil engineer with the Air Force that led to a career in the U.S. government in facilities engineering with the Defense Intelligence Agency and the Office of the Director of National Intelligence, culminating as the Intelligence Community Deputy Director for Facilities and Logistics. In his distinguished career, Ben was awarded the Intelligence Community Exemplary Civilian Service to the Department of the Air Force medal, the Air Force Commendation medal, the Air Force Meritorious Service medal with oak leaf clusters in lieu of second and third award, and the Humanitarian Service medal with bronze stars in lieu of second and third award.
Section VI - Events
13 Apr 23 (Thursday), 1130 (PST) - In Person - San Francisco - The AFIO Andre LeGallo Chapter hosts Richard E. Hanson on CIA Operations in Viet Nam. No-host cocktail. Location: Basque Cultural Center, 599 Railroad Avenue, South San Francisco, CA. Please contact Mariko Kawaguchi, Board Secretary at afiosf@aol.com for questions. Students: please e-mail your school ID to get sponsored. Register here.
21 Apr 23 (Friday), 1030 (ET) - In-Person Tysons, VA - Registration has opened for AFIO National Spring Luncheon. Presentations by LTG Michael Groen (USMC, Ret), former Commander of the Joint Artificial Intelligence Center, discussing AI. His presentation begins at 11:00 a.m. And journalist Jim Popkin discussing Cuban Spy Ana Montes featured in his book, "Code Name Blue Wren: The True Story of America's Most Dangerous Female Spy―and the Sister She Betrayed." His talk starts at 1:00 p.m. Lunch served noon-1:00 p.m. Event ends 2:00 p.m.
Registration closes 5:00 p.m. Friday, 14 April.
Register here
NO registrations or walk-ins at hotel. Check-in and badge pickup for Registered Attendees starts at 10:30 a.m. Luncheon prices are $55 for Members; $70 for nonmember guests and all Subscribers.
Though we do not provide special overnight room rates, if you wish to make room reservations at the hotel, do so here. Cancellation Schedule: AFIO must guarantee XX meals to the hotel; therefore, regrets it must charge a cancellation fee. 100% refund until close of registration. No refunds or cancellations after close of registration. You will receive a donation receipt for fees forfeited. A donor statement will be sent showing that you made a "gift to AFIO" in such instances. Gifts to AFIO are tax-deductible. All attendees must be members of AFIO or accompanied by a member of AFIO. To learn more about becoming a member, visit: www.afio.com. If you have any questions regarding membership, contact our office at 703-790-0320 or email us at afio@afio.com. Questions regarding event? Email events@afio.com
Some reactions to Popkin's "Code Name Blue Wren"
"Code Name Blue Wren might be the most mesmerizing spy story I've ever read. It shows how a brilliant manipulator secretly working for the Cubans finagled her way deep into the US military—and the anguish of the friends and family she so easily conned. Jim Popkin captures the brutal realities of modern espionage. I couldn't stop reading this." —Mark Leibovich, author of This Town and Thank You for Your Servitude
"For espionage devotees, Jim Popkin's Code Name Blue Wren is a critical read. In great detail, Popkin explores the case of Ana Montes, who became a mole in the Defense Intelligence Agency for Cuban intelligence. A mole who was almost never caught thanks to years of incompetence by the FBI's counterspies. But thanks to the dogged persistence of a dedicated NSA analyst, who bypassed the FBI at great risk to her career, Montes was arrested shortly after the 9/11 attacks. Left in her wake was the likely death of an American Green Beret killed in action in El Salvador and the pro-American troops fighting alongside him." —James Bamford, bestselling author of The Puzzle Palace and Spyfail: Foreign Spies, Moles, Saboteurs, and the Collapse of America's Counterintelligence
"Jim Popkin uncovers riveting details about one of the most damaging spy cases in US history, revealing new insights into the highly sensitive secrets that Ana Montes gave to her Cuban handlers. Through remarkably extensive interviews with her relatives and coworkers, he exposes not only what she did but why. This is the definitive history of how one of America's most highly regarded intelligence analysts betrayed her country, and how she almost got away with it." —Pete Williams, former NBC News justice correspondent
"This spy tale reads like a new season of Homeland – except this Ice Queen's traitorous double-life was entirely real. Jim Popkin takes us deep into a long-ignored story of an intel officer who went rogue, spilling US secrets to Cuba, endangering US operatives, and tricking presidents and her own sister at the FBI in the process." —Carol Leonnig, Pulitzer Prize-winning reporter at the Washington Post and author of Zero Fail: The Rise and Fall of the Secret Service
"An entertaining story of cunning espionage."—Kirkus Reviews
See the AFIO Calendar of Events for scheduling further in the future.
Events from Advertisers, Corporate Sponsors, Others
Join International Spy Museum Historian and Curator Dr. Andrew Hammond in conversation with historian Benny Morris, author of Sidney Reilly: Master Spy, about one of the most colorful and best-known spies of the twentieth century. Emerging from humble beginnings in southern Russia, Reilly was an inventive, multilingual businessman and conman who became a virtuoso of espionage. He spent World War I in the United States, brokering major arms deals for tsarist Russia, and then joined the ranks of MI6, Britain's foreign intelligence service. He tried to overthrow the Bolshevik regime in Moscow before eventually being lured back to Russia and executed. The Spy Museum is proud to exhibit the only object in existence that illustrates the connection between Reilly and R.H. Bruce Lockhart, co-conspirator of the plot. Join the historians as they sift through the reality and the myth of Reilly's life to paint a fascinating portrait of one of the most intriguing figures from the golden age of spies. Program is free of charge but requires advanced registration. Explore or Register here: www.spymuseum.org.
Prof. John J. Quattrocki, Former Vice President, CACI's National Intelligence Solutions Group; Former Senior Executive on the National Security Staff, will be discussing "The Fourth Man" controversy raised by retired CIA Case Officer, Bob Baer, who published a book of the same title which has reignited an Intelligence Community bar fight as the IC approaches its 40-year anniversary. Join the discussion at IWP, as they discuss the case that has been at the core of IWP's curriculum on the Statecraft of Counterintelligence for more than 18 years. Location: The Institute of World Politics, 1521 16th St. NW, Washington D.C. 20036, in the Marlatt Mansion, Commodore Barry Room. Register here. No cost to attend but registration required.
Alma Katsu is the award-winning author of seven novels; Red London, her latest is a follow-up to the successful Red Widow where she unveiled Lyndsey Duncan, a CIA intelligence officer nicknamed "the human lie detector." Katsu knows what she is writing about. She had a thirty-five-year career as a senior intelligence analyst for several US agencies, including the CIA and NSA, where she advised policymakers and military commanders on issues of national security. Her newest book is a nuanced, race-against-the-clock story that invokes today's headlines. International Spy Museum Director of Adult Education Amanda Ohlke and Katsu will discuss how Lyndsey reflects the reality of women working in intelligence and how the thriller's plot reflects both current affairs and famous notes from the past—like well-placed moles at the CIA. Explore or Register here: www.spymuseum.org.
SPY with Me is an interactive virtual program for individuals living with dementia and their care partners. Join SPY as we use music and artifacts to explore some of our favorite spy stories. Programs last one hour and are held virtually through Zoom. Every month the same program is offered on two different dates. To register, please email Shana Oltmans at soltmans@spymuseum.org. Free but space is limited. Register below. Explore or Register here: www.spymuseum.org.
Wednesday, 29 Mar 23, 0900-1700 (ET) – Boston, MA – How Wars End: A Conference Presented by the Pardee Center for the Study of the Longer-Range Future – Boston University - In Person
The event will feature five expert panels:How wars end from a historical perspective (Moderator: Prof. Erik Goldstein), How intelligence supports diplomats in ending wars (Moderator: Prof. Joseph Wippl), How the Afghanistan War ended (Moderator: Prof. John Woodward), How the Iraq War ended (Moderator: Prof. Shamiran Mako), How current crises will end (Moderator: Ambassador Mark Storella). The full list of panelists will be announced in the coming weeks. This conference is convened by Prof. John Woodward, Prof. Cathal J. Nolan, and Prof. Erik Goldstein in their capacity as Pardee Center Faculty Research Fellows. This event is free and open to the public. Register here.
SPY with Me is an interactive virtual program for individuals living with dementia and their care partners. Join SPY as we use music and artifacts to explore some of our favorite spy stories. Programs last one hour and are held virtually through Zoom. Every month the same program is offered on two different dates. To register, please email Shana Oltmans at soltmans@spymuseum.org. Free but space is limited. Register below. Explore or Register here: www.spymuseum.org
"The Nation's Premier Intel and National Security Event" - Save the date for the 10th Annual AFCEA/INSA Intelligence and National Security Summit! The powerful, two-day program, at the Gaylord National Resort, will feature five blockbuster plenaries, six engaging breakout sessions, and a jam-packed exhibit hall full of the latest IC technology innovations. Top leaders will discuss State of the Community, Military Intelligence Priorities, Strategic Intelligence, and Cybersecurity Challenges. Breakout sessions with senior leaders, technology experts, and thought leaders will examine some of the most pressing issues facing the community. Plus, powerful networking opportunities designed to foster partnerships and relationship building. Stay tuned! Registration to open in early March. Check for updates here.
Gifts for Friends, Colleagues, Self
 Now available: Black short-sleeved polo shirts with Embroidered AFIO logo
Now available: Black short-sleeved polo shirts with Embroidered AFIO logo
Show your support for AFIO with our new Black Short-sleeve Polo Shirts. Shirts are shrink and wrinkle resistant of fine cotton with a soft, "well-worn, comfy" yet substantial feel. They feature a detailed embroidered AFIO seal. Get a shirt for yourself and consider as gifts for colleagues, family, and friends. Only $50 each including shipping.
Sizes for (M) men, only; Small, Medium, Large, XL, XXL, and XXXL. $50 per shirt.
You may pay by check or credit card. Complete your order online here or mail an order along with payment to: AFIO, 7600 Leesburg Pike, Ste 470 East, Falls Church, VA 22043-2004. Phone orders at 703-790-0320. Questions? Contact Annette at: annettej@afio.com.

PopSocket for cellphones or tablets
Show your support to AFIO while enjoying the convenience offered by our AFIO Logo PopSocket. The PopSocket is most commonly used as a stand and as a grip for your mobile phone or tablet; handy for taking selfies, watching videos, and for texting. The PopSocket looks like a small button or sticker which, when closed, sticks flat to your mobile device. However, its accordion-like design enables it to pop open for use. The benefits of using a PopSocket make it a must-have accessory for your mobile phone or tablet. It also aids in keeping your phone from slipping off your hand during use, falling, or breaking.
Price: $15. Order this and other store items online here.

Duffel Bags - Royal Blue and Black with Full Color AFIO Logo This duffel has it all when it comes to value, style and organization.
600 denier polyester canvas with polyester double contrast; D-shaped zippered entry for easy access. Front pocket with hook and loop closure. End mesh pocket Easy-access end pockets. Four durable, protective feet and built-in bottom board for added strength. Web handles with padded grip. Detachable, adjustable shoulder strap.
Dimensions: 11"h x 19.75"w x 9.75"d; Approx. 2,118 cubic inches
Price: $50. Order this and other store items online here.
AFIO Mug with color glazed seal.
Made in the U.S.A., dishwasher-safe.
$35 includes shipping.
Sip your morning joe in style or use it to stash pens, cards, paperclips, or candy.
Order this and other store items online here.

Caps - Dark Navy with Navy AFIO Logo
An authentic silhouette with the comfort of an unstructured, adjustable fit. Fabric: 100% cotton. Unstructured. Fabric strap closure with adjustable D-clip. Price: $30. Order this and other store items online here.
JUST PUBLISHED FOR 2023
| Be informed on career opportunities in the U.S. Intelligence Community | ||
 |
Intelligence as a Career - with updated listings of colleges teaching intelligence courses, and Q&As on needed foreign languages, as well as the courses, grades, extracurricular activities, and behavioral characteristics and life experiences sought by modern U.S. intelligence agencies. AFIO's popular 47-page booklet reaches thousands of high school, college students, university guidance offices, and distributed in classes teaching intelligence, to help those considering careers in the U.S. Intelligence Community. |
 |
| This is the all new fifth edition. The publication is also popular with University Career Guidance Centers, professors and academic departments specializing in national security, and parents assisting children or grandchildren in choosing meaningful, public service careers. This booklet is provided online as a public service from the generosity of AFIO board, volunteer editors/writers, donors, and members. We thank all for their support which makes this educational effort possible. |
||
| Careers Booklet (new 2023 Fifth Edition) can be read or downloaded here |
||
 Guide to the Study of Intelligence...and...When Intelligence Made a Difference
Guide to the Study of Intelligence...and...When Intelligence Made a Difference
"AFIO's Guide to the Study of Intelligence" has sold out in hard-copy.
It is available in digital form in its entirety on the
AFIO website here.
Also available on the website here are the individual articles of AFIO's
history project "When Intelligence Made a Difference" that have been
published to date in The Intelligencer journal.
More articles will be appear in future editions.
Some features of the email version of the WIN do not work for readers who have chosen the Plaintext Edition, some users of AOL, and readers who access their email using web mail. You may request to change from Plaintext to HTML format here afio@afio.com. For the best reading experience, the latest web edition can be found here: https://www.afio.com/pages/currentwin.htm
To unsubscribe from the WIN email list, please click the "UNSUBSCRIBE" link at the bottom of the email. If you did not subscribe to the WIN and are not a member, you received this product from a third party in violation of AFIO policy. Please forward to afio@afio.com the entire message that you received and we will remove the sender from our membership and distribution lists.
(c) 1998 thru 2023
AFIO Members Support the AFIO Mission - sponsor new members! CHECK THE AFIO WEBSITE at www.afio.com for back issues of the WINs, information about AFIO, conference agenda and registrations materials, and membership applications and much more! .
AFIO | 7600 Leesburg Pike, Suite 470 East, Falls Church, VA 22043-2004 | (703) 790-0320 (phone) | (703) 991-1278 (fax) | afio@afio.com