
09 - 15 April 2025
(Issue 15)
Send submissions and comments to: winseditor@afio.com.
CONTENTS
(Recent Developments)
General Interests
- EU issues US-bound staff with burner phones over spying fears - Financial Times, 14 Apr 25 (Member Contribution)
- CIA preparing for AI agents while maintaining human in the loop - Washington Times, 14 Apr 25 (Member Contribution)
- US readies super spy drones with 8,500-mile-range to tackle China’s moves near Taiwan - Interesting Engineering, 09 Apr 25 (Member Contribution)
- Gabbard sets up DOGE-style team to cut costs, uncover intel ‘weaponization’ - Washington Post, 08 Apr 25 (Member Contribution)
- Russia Using Oligarchs' Yachts, Spy Devices for Naval Espionage: Report - Newsweek, 07 Apr 25
- Space Force's intelligence ‘marketplace’ gets funds to expand - Defense One, 10 Apr 25
- Exclusive: At the NSA, backlogs to clear resumes as employees consider their future - HUMINT, 11 Apr 25
Special Collections
- Counterespionage - Arrests, convictions, expulsions, and more...
- Cyberespionage - New actors, collection and sabotage ops, countermeasures, policy, other...
- Covert Action - Influence ops, assassinations, sabotage, paramilitary ops, countermeasures, etcetera...
Section II - DEEP DIVES
(Research Papers, OpEds, Analysis, Podcasts)
- U.S.-Iran Nuclear Talks a Magnet for Spies - SpyTalk, 11 Apr 25 (Member Contribution)
- Russia’s FSB and Law Enforcement Tactics Suppress Opposition - Jamestown Foundation, 11 Apr 25 (Member Contribution)
- Pentagon’s blind spot: How bureaucratic bungling is leading to the next intelligence catastrophe - Washington Times, 10 Apr 25 (Member Contribution)
- Sweden’s SÄPO Reports that Russia is Evolving Sabotage Tactics - Jamestown Foundation, 09 Apr 25 (Member Contribution)
- The Tangled History of the State Secrets Privilege - Lawfare, 08 Apr 25
- Taiwan: China's Testing Ground for Intelligence Operations (32 min) - SpyCast Podcast, 08 Apr 25
- Britain’s Spymasters — The Kremlin’s Most Feared Enemy - Center for European Policy Analysis, 08 Apr 25
Section III - FORMERS' FORUM
(Legacy Intel Practitioners' Informed Perspectives
and Recent Endeavors)
- I helped Biden defend against national security threats. NSA needs skilled leaders not politics. - by former Assistant Secretary of State for INR and former acting director of the National Counterterrorism Center Brett M. Holmgren - Fox News, 10 Apr 25 (Member Contribution)
- Qatar Told Hamas to Keep Israeli Hostages - with former U.S. Intelligence Officer Michael Pregent - Haaretz, 10 Apr 25 (Member Contribution)
- What the ‘Signalgate’ Snafu Overlooks - by Former CIA Senior Analyst Michael Ard - Discourse Magazine, 08 Apr 25(Member Contribution)
- American academia and Chinese espionage go hand-in-hand by former NSA Counterintelligence Officer John Schindler - Washington Examiner, 08 Apr 25
- Information War: The U.S. Surrenders by former CIA Senior Operations Officer John Atwell - Hawaii Tribune Herald, 08 Apr 25
Books: (Forthcoming, New Releases, Overlooked)
- The Illegals: Russia's Most Audacious Spies and Their Century-Long Mission to Infiltrate the West by Shaun Walker (15 Apr 25)
- Cracking the Nazi Code: The Untold Story of Agent A12 and the Solving of the Holocaust Code by Jason Bell (30 Apr 24)
- Covert Action in the Cold War: US Policy, Intelligence and CIA Operations by James Callanan (15 Dec 09)
Intelligence Matters on Film: The Tailor of Panama - John Boorman (2001)
Intelligence in History - A Collection of Recently Released Content
Walking Tours: "The Spies of Embassy Row" and "Spies of Georgetown" - Washington, DC. (Sundays, Dates/Times Vary)
Section V - Obituaries and Classifieds
(Research Requests, Academic Opportunities, Employment)
Research Requests and Academic Opportunities
- Call for Information: Nephew of OSS and CIA officer Robert Stock (1916-1983), last seen alive by family in 1957, seeks information on uncle's past.
- Call for Information: Child of CIA officer seeks former CIA SE division branch chiefs (1980-1994), CIA officers stationed in Rome (1986-90).
- Call for Study Participants: Current and former intel professionals experienced in collecting, analyzing, or disseminating intelligence that directly informs organizational goals/missions in federal agencies, military, law enforcement, or private sector.
- Call for Information: CIA in 1970 FIFA World Cup or 1968 Olympic Games.
- Academic Opportunity: The International Security & Intelligence Programmer at Emmanuel College in the University of Cambridge, Summer 2025. Residential Programmer: Cambridge, Sunday 6 July to Saturday 2 August 2025.
- Information Sought: 1969 "KGB Wanted List"
- Call for Collaboration: AFIO member seeks help establishing YouTube channel focused on Russian and Chinese influence operations.
- Internship Opportunity: International private intelligence company accepting applications for analyst internship program.
- Call for Information: Child of former CIA Como Officer Walter E. McLeod seeks information about father's life and work.
- Director, School of Criminology and Security Studies, Full Professor or Associate Professor - Indiana State University - Terre Haute, Indiana
- Open-Source Intelligence Laboratory and Professor of Intelligence and National Security Studies - University of Texas at El Paso - El Paso, Texas
- 2 Assistant Professors in Intelligence and Security - Institute of Security and Global Affairs, University of Leiden, Netherlands
- Assistant Professor of Intelligence Studies - Mercyhurst University - Erie, Pennsylvania
- Associate Professor and Chair of National Security - University of New Haven, Connecticut
- Wanted: Former intelligence officers to lead spy-themed walking tours in Washington, D.C. - Spyher Tours
- Assistant Professor - Intelligence Studies - Embry-Riddle Aeronautical University, Arizona
- Tue 22 Apr 2025, 12:00pm EDT - Tampa, FL and virtual - The Florida Suncoast AFIO Chapter luncheon features COL Mike McCalister (US Army, RET) speaking on "Current Global and National Challenges facing the United States"
- Wed May 7 2025, 11:30am PDT - AFIO LA Chapter - Adm James Stavridis, a CNN Military Analyst, discusses Trump Administration Policies' Impact on International Security - In-person
- Wednesday, 28 May, 2025, 11:30am no host cocktails, Noon meeting - In-Person, San Francisco CA - "The Language of War" by LTC Christopher Gin, DLI 229th Military Intelligence Battalion Commander and Visiting Scholar, Center for International Security and Cooperation, Stanford University
Events of Advertisers, Corporate Sponsors, Others
- Wednesday, April 16, 6:30pm – Washington, DC – Rogue Agent with James Crossland – Virtual and In-Person International Spy Museum Program
- Thursday, April 17, 12:00-1:00pm – Washington, DC – Spy Chat with Special Guest Jen Easterly – Virtual International Spy Museum Program
- Tuesday, April 22, 2:00-3:00pm – Washington, DC – SPY with Me: Program for Individuals with Dementia and their Care Partners – Virtual International Spy Museum Program
- Wednesday, 30 Apr 25, 1200-1300 (ET) – Virtual – Inside Intelligence presents "Domestic Intelligence is Broken" with Donell Harvin - Johns Hopkins University
- Thursday, 15 May 2025: 6p-8p- Washington, DC - The Art of Building Relationships at The Octagon Museum and oldest private residence in Washington D.C.
- 30 Aug - 8 Sep 2025 - Mediterranean Cruise - Spies, Lies & Nukes announce Espionage on the High Seas! Plan NOW to join the late-summer 2025 cruise.
See the AFIO Calendar of Events for scheduling further in the future.
Acknowledgments
The editor thanks the following
contributors of content for this issue:
LC, JK, LR, TM, GR, EB, MA
DISCLAIMER
The Weekly Intelligence Notes include a wide range of articles and commentary to
inform our readers. It also includes several paid advertisements. Views expressed in articles and advertising are those of the authors and advertisers; they do not reflect AFIO's support or endorsement. Notices about non-AFIO events do not reflect AFIO endorsement or recommendation.
AFIO does not vet or endorse research inquiries, career announcements, or job offers. Reasonable-sounding inquiries and career offerings are published as a service to readers, who should exercise caution and good judgment when responding and independently verify the source before supplying resumes, career data, or personal information.
CIA's In-house Gift Shop
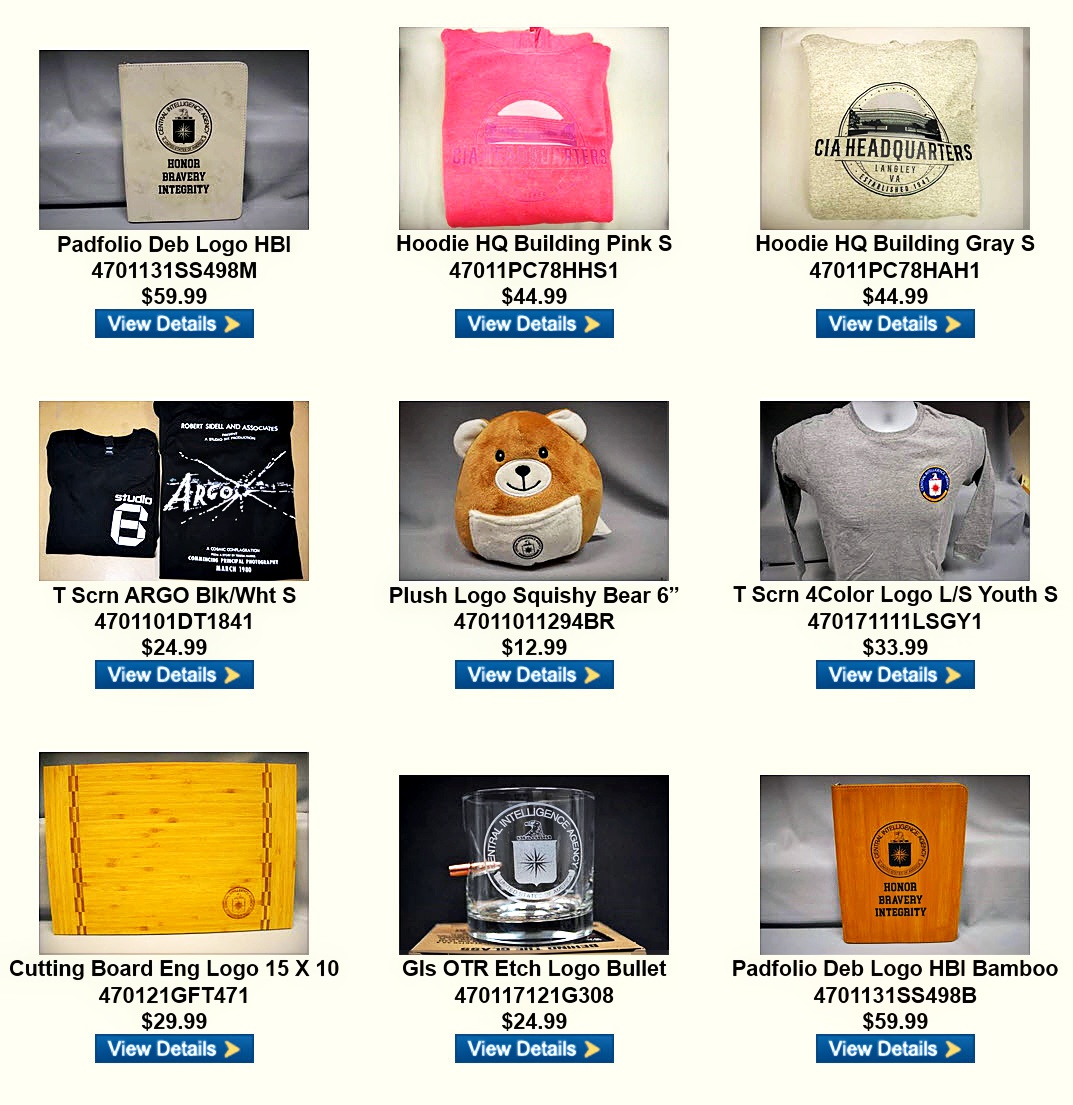
One special benefit of AFIO membership is access to CIA's EAA Store.
After completing the required, quick pre-approval process for all AFIO members described here, you can purchase directly from the EAA online store their unusual logo'd gift items for self or colleagues. EAA on 28 March 2025 released the photo above, which features some of their newest CIA items and other gift suggestions.
ANNOUNCEMENTS
AFIO IC National Luncheon Friday, 2 May 2025, 10:30 am - 2 pm - McLean, VA |
||
 |
|
 |
Schedule: 1030 - Check-in for preregistered attendees (no walk-ins) |
||
| BIO: Michael Ellis was sworn in as Deputy Director of the CIA on February 10, 2025. DD/CIA Ellis has held a variety of senior national security positions, including General Counsel of the National Security Agency and Senior Director for Intelligence Programs at the National Security Council. DD/CIA Ellis previously served in the White House Counsel's Office, providing legal advice on national security and foreign relations. Prior to the White House, he was General Counsel of the U.S. House of Representatives Permanent Select Committee on Intelligence and served as an intelligence officer in the U.S. Navy Reserve. Before returning to government, DD/CIA Ellis was the General Counsel of Rumble, a publicly traded video sharing platform and cloud services provider. DD/CIA Ellis is a graduate of Yale Law School and Dartmouth College. Following law school, he served as a clerk to two federal judges. | ||
| BIO: David M. Cattler is the Director of the Defense Counterintelligence and Security Agency (DCSA), the United States Government's premier provider of integrated security services, effective March 24, 2024. DCSA is a strategic asset to the Nation and its allies — ensuring a trusted federal and industrial workforce and enabling industry's delivery of uncompromised capabilities. DCSA uniquely blends industrial security, counterintelligence support, personnel vetting, and security training to advance and preserve America's strategic edge. He leads the agency's strategic transformation and maturation, and a workforce of approximately 12,000 federal and contract support personnel worldwide. Before joining DCSA, Mr. Cattler served as Assistant Secretary General for Intelligence and Security at the North Atlantic Treaty Organization (NATO), and informed and protected NATO |
||
| Registration and Cost: Registration and credit card payment required before event. Lunch is $60 (members) or $75 (guests, Subscribers). Students $30 - limited seats. Registration opens 2 April 2025 and is available while space remains. Registration closes 1700 hours, Friday, 25 Apr 2025 or earlier when all seats taken. |
||
Register HERE while space remains. |
||
| Venue: DoubleTree by Hilton Hotel, 1960 Chain Bridge Rd, McLean, VA 22102 Though we do not provide special overnight room rates, if you wish to make room reservations at the hotel, do so here. |
||
| Cancellations: No refund for cancellations after 21 Apr 2025. Payment for reservations canceled 22 to 30 Apr 2025 will be converted to donations to AFIO. Payments for reservations canceled after 30 Apr 2025 are forfeited; the meal will have been guaranteed at the hotel per the contract. Attendees must be AFIO members or accompanied by a member. For security reasons, no late or last-minute substitutions. |
||
| Please direct questions to events@afio.com | ||
AFIO Now Just Released
Released 15 April 2025...to members-only
The Oligarch's Daughter
Joseph Finder,
author, Russian Studies expert, on
The Oligarch's Daughter
Interview of Tuesday, 13 March 2025 with Joseph Finder, author, Russian Studies expert, on The Oligarch's Daughter
Interviewer and Host: AFIO President James Hughes, a former senior CIA Operations Officer.
The interview runs 12 minutes.
It is a breakneck thriller that marries the dynastic opulence of Succession with the tense and disorienting spycraft of The Americans.
"This is Finder at his finest—a perfect everyman-in-peril story, first building an ominous drumbeat of menace, then exploding in action and intrigue and triumph. As good as it gets."—Lee Child
Access the FINDER video interview here or click above image.
The AFIO Now video and podcast series is proudly sponsored by
Northwest Financial Advisors.
- Spy Cruise -
 Valerie Plame's Spies, Lies & Nukes Conference, in collaboration with the International Spy Museum, brings you Spies at Sea 2025—an unparalleled espionage experience on the high seas! 30 August - 08 September 2025. AFIO members receive $100 discount (use code "AFIO"). More information and booking details in "Events" section below and here.
Valerie Plame's Spies, Lies & Nukes Conference, in collaboration with the International Spy Museum, brings you Spies at Sea 2025—an unparalleled espionage experience on the high seas! 30 August - 08 September 2025. AFIO members receive $100 discount (use code "AFIO"). More information and booking details in "Events" section below and here.
- AFIO Scholarship -
Applications Being Accepted now until 1 June 2025
Five Undergrad, Five Graduate Scholarships
$5,000 EACH.
Do not let budget limitations stop you from reaching your potential. Let AFIO offset some of your education costs. Applications for 2025 have opened and can be sent to us online until 1 June 2025. No applications accepted after midnight 1 June 2025.
View scholarship requirements here.
- New From the International Spy Museum -
Guided Tour. The International Spy Museum announces new guided public tours for its visitors through its volunteer docent program, The Honorable William H. Webster Docent Corps. On Fridays and Sundays at 11 AM and 1 PM, volunteer docents will lead visitors through a special one-hour long highlights tour of the permanent exhibit and will answer questions about the material. More information: here.
Podcast Reboot. The longest-running podcast on intelligence, the International Spy Museum’s SpyCast, gets a full refresh, kicking off the new year with a brand-new host, length, and format. Partnering with creative audio agency Goat Rodeo and curated podcast network Airwaves, the Museum will pivot from its long form interview format to the production of shorter, narrative-driven 25-minute episodes that answer specific questions about intelligence tradecraft, headlines, or processes that fascinate and mystify audiences. More information here
National Intelligence Summer Academy (NISA) - High School Students Grades 10-12
14-18 July 2025 - Cummings, GA
University of North Georgia, Cummings Campus,
300 Aquatic Circle Cummings, GA 30040
 Are you thrilled or fascinated by the field of intelligence – spying and counter spying?
Are you thrilled or fascinated by the field of intelligence – spying and counter spying?
Are you considering a career in the U.S. Intelligence Community? Did you know that the U.S. Intelligence Community is made up of 18 separate agencies? Sign up for an intense and exciting five days of learning from intelligence practitioners, University of North Georgia instructors, and highly qualified MA and Ph.D. degree holders.
This Academy will: Lift the veil of secrecy on the hidden world of intelligence, exploring the history, challenges, and controversies;
Provide a context for understanding the important role intelligence has played in our nation's history and continues to play today;
Provide foundational knowledge of intelligence, setting the stage for possible careers in the field;
Provide opportunities to learn from the Academy's instructors include academia, practitioners, and guest speakers.
Hear from experts that have worked with the CIA, FBI, and the former Soviet Union KGB.
Explore, Apply, Learn more
Spyher Winter Savings
Regularly scheduled spy tours are available
through Georgetown, Embassy Row, Capitol Hill, and Arlington National Cemetery.
Book now on Eventbrite
Spyher Gift Cards
Give the Gift of an Exclusive Spy History Tour with a Former Intelligence Officer
Purchase an e-gift card here.
For a physical gift card contact rosanna@spyher.co
AFIO Exclusive Content
- WIN Short-form Book Review -
(April 2025)
 Randal Phillips
Randal Phillips
Former CIA East Asia Division Chief (acting), Chief of China Ops,
COS Beijing
reviews
Chinese Espionage, Operations, and Tactics, Second Edition
by Nicholas Eftimiades
(January 2025)
Access review here.
 - Latest AFIO Now Audio Podcast -
- Latest AFIO Now Audio Podcast -
AFIO Now Podcasts Presents:
Douglas Waller, Historian, Author, and Foreign Correspondent
discussing his new book
"The Determined Spy: The Turbulent Life and Times of CIA Pioneer Frank Wisner"
Frank Wisner was one of the most powerful men in 1950s Washington, though few knew it. Reporting directly to senior U.S. officials--his work largely hidden from Congress and the public--Wisner masterminded some of the CIA's most controversial operations in the early years of the Cold War, commanding thousands of clandestine agents around the world.
Recorded: 31 Mar 25
Interviewer: AFIO President James Hughes
Duration: 30 min (with Q&A)
Purchase The Determined Spy here.
The audio-only version of AFIO Now, great for listening to in your car or while accomplishing other tasks, can be downloaded or streamed on any of the following podcast platforms by searching for "AFIO":
Podbean; iTunes; Spotify; Amazon Music; TuneIn; iHeartRadio; Pandora
AFIO Now Archive
AFIO Now interviews, video and audio-only forms, are proudly sponsored by
Northwest Financial Advisors
Click here to watch interviews in the AFIO Now series released in 2025.
View interviews from 2020 to 2024 here.
Watch public-release interviews on our YouTube channel or listen to them in podcast form at the links in the section above.
Log into the member-only area for member-only features.
THE MARKETPLACE
THE AFIO STORE
Special Gifts for Colleagues, Self, or Others
 Gray long-sleeved polo shirts with embroidered AFIO logo. Men's sizes only.
Gray long-sleeved polo shirts with embroidered AFIO logo. Men's sizes only.
Show your support for AFIO with our new Gray Long-sleeve Polo Shirts. Shirts are shrink and wrinkle resistant of fine cotton with a soft, "well-worn, comfy" yet substantial feel. They feature a detailed embroidered AFIO seal. Get a shirt for yourself and consider as gifts for colleagues, family, and friends. Only $60 each including shipping.
Sizes for men, only: Small, Medium, Large, XL, XXL, and XXXL. $60 per shirt. Order this and other store items online here.
 20 oz ceramic Mug with color glazed logo. Made in America. Check out our tapered, sleek AFIO coffee mug. This handsome 20 oz. ceramic mug is made in the USA, has a white matte exterior, sports a beautiful navy-blue interior, and is dishwasher safe. Order yours today! $35 per mug includes shipping to a CONUS address. [includes shipping to U.S. based address, only. For foreign shipments, we will contact you with a quote.] SHIPPING: For shipment to a U.S.-based CONUS address, shipping is included in price. For purchases going to AK, HI, other US territories, Canada, or other foreign countries the shipping fees need to be calculated, so please call our office M-F 8 a.m. to 2 p.m. ET at 703-790-0320 or email afio@afio.com providing following information: 1) your name, 2) mailing address (or addresses where each gift item will be shipped), 3) name of the AFIO store items you wish to purchase, 4) quantity of each, 5) your credit card number and expiration date, 6) amount (except for additional of shipping fees) authorized to charge, and 7) your phone number and email should we have questions. Foreign shipments fees will be calculated and estimates emailed to you, awaiting your approval. Order this and other store items online here.
20 oz ceramic Mug with color glazed logo. Made in America. Check out our tapered, sleek AFIO coffee mug. This handsome 20 oz. ceramic mug is made in the USA, has a white matte exterior, sports a beautiful navy-blue interior, and is dishwasher safe. Order yours today! $35 per mug includes shipping to a CONUS address. [includes shipping to U.S. based address, only. For foreign shipments, we will contact you with a quote.] SHIPPING: For shipment to a U.S.-based CONUS address, shipping is included in price. For purchases going to AK, HI, other US territories, Canada, or other foreign countries the shipping fees need to be calculated, so please call our office M-F 8 a.m. to 2 p.m. ET at 703-790-0320 or email afio@afio.com providing following information: 1) your name, 2) mailing address (or addresses where each gift item will be shipped), 3) name of the AFIO store items you wish to purchase, 4) quantity of each, 5) your credit card number and expiration date, 6) amount (except for additional of shipping fees) authorized to charge, and 7) your phone number and email should we have questions. Foreign shipments fees will be calculated and estimates emailed to you, awaiting your approval. Order this and other store items online here.
Section I - CURRENTS
(Recent Developments)
(Recent Developments)
General Interests
EU issues US-bound staff with burner phones over spying fears - Financial Times, 14 Apr 25 (Member Contribution)
The European Commission is issuing burner phones and basic laptops to some US-bound staff to avoid the risk of espionage, a measure traditionally reserved for trips to China. Commissioners and senior officials travelling to the IMF and World Bank spring meetings next week have been given the new guidance, according to four people familiar with the situation. They said the measures replicate those used on trips to Ukraine and China, where standard IT kit cannot be brought into the countries for fear of Russian or Chinese surveillance. “They are worried about the US getting into the commission systems,” said one official. The treatment of the US as a potential security risk highlights how relations have deteriorated since the return of Donald Trump as US president in January. (Access here.)
CIA preparing for AI agents while maintaining human in the loop - Washington Times, 14 Apr 25 (Member Contribution)
The CIA is planning for a future in which artificial intelligence agents augment the spy business, but a human stays involved in the process. Lakshmi Raman, the CIA’s AI chief, said Friday that she anticipates AI agents will be heavily involved in the espionage business. “I can imagine a future where AI is in the hands of an intelligence, of all intelligence officers, helping them do their work faster and have lots of productivity gains,” Ms. Raman said at a Vanderbilt University summit. “I can imagine having AI assistants in place to help our analysts go through massive amounts of reporting from thousands of sources with all modalities.” (Access here.)
US readies super spy drones with 8,500-mile-range to tackle China’s moves near Taiwan - Interesting Engineering, 09 Apr 25 (Member Contribution)
The US has decided to deploy long-range surveillance drones in the region to spy on Chinese activities around the Taiwan Strait, the Sea of Japan, and the East China Sea. Japan’s Minister of Defense, Gen Nakatani, confirmed in a press conference on April 8 that the US military will deploy its MQ-4C Triton unmanned aerial vehicles (UAVs) at the US Kadena Air Base on Okinawa’s main island “within a few weeks.” With this deployment, the US and Japan aim to boost the intelligence, surveillance, and reconnaissance (ISR) capabilities around Japan and nearby regions, Nakatani said. “The security environment surrounding our country is becoming increasingly severe,” Nakatani reportedly added. (Access here.)
Gabbard sets up DOGE-style team to cut costs, uncover intel ‘weaponization’ - Washington Post, 08 Apr 25 (Member Contribution)
Director of National Intelligence Tulsi Gabbard has established a new group to work on cost-cutting and investigate “weaponization” across the 18 spy agencies that her office oversees. The Director’s Initiatives Group was established in line with President Donald Trump’s executive order to “bring about transparency and accountability” in the intelligence community, the Office of the Director of National Intelligence said in a news release Tuesday. “We are already identifying wasteful spending in real time, streamlining outdated processes, reviewing documents for declassification, and leading ongoing efforts to root out abuses of power and politicization,” the ODNI said in the release. The composition of the group and its level of access and clearance remain unclear. But one U.S. official familiar with the matter said the group is composed of up to 10 people from outside the agency, vetted by the White House. The official, like several others interviewed for this report, spoke on the condition of anonymity to discuss internal matters. (Access here.)
Russia Using Oligarchs' Yachts, Spy Devices for Naval Espionage: Report - Newsweek, 07 Apr 25
Superyachts owned by Russian oligarchs have carried out reconnaissance missions on behalf of the Kremlin, marking part of a broader surveillance effort by Russia to gather intelligence on the U.K.'s nuclear deterrent and critical undersea infrastructure, a new report claims. Why It Matters: The U.K. and the U.S. are members of a multinational task force designed to put "unprecedented pressure on sanctioned Russians" in the wake of Moscow's full-scale invasion of Ukraine. Western supporters of Ukraine have frozen roughly $300 billion in Russian Central Bank assets, as well as seizing and detaining yachts owned by Russian citizens under sanctions. Russian oligarchs are typically closely connected to the Kremlin. Russia has a highly sophisticated underwater fleet, kitted out with advanced submarines and autonomous vehicles gliding far beneath the waves. Moscow is particularly adept at what is known as hybrid warfare, a raft of tactics that can include targeting vital cables snaking along the seabed. (Access here.)
Space Force's intelligence ‘marketplace’ gets funds to expand - Defense One, 10 Apr 25
A Space Force program that buys commercial satellite imagery and analytics has seen success across combatant commands—and with a plus-up from Congress, the service hopes to give commands more information and new tools. Called Tactical Surveillance, Reconnaissance, and Tracking, or TacSRT, the program began as a pilot in 2023. It provides a “marketplace” where military customers seeking timely intelligence can ask a question and then industry competes to provide answers. The tool has been used to support a wide range of missions, from tracking illegal fishing and monitoring humanitarian assistance and disaster relief to supporting the construction of the Joint-Logistics-Over-the-Shore pier in Gaza and the withdrawal of forces from air bases in Niger. (Access here.)
Exclusive: At the NSA, backlogs to clear resumes as employees consider their future - HUMINT, 11 Apr 25
At the NSA, the Prepublication Review office is now experiencing a backlog. Staff there examine material to prevent inadvertent disclosures of classified information. And so many agency personnel have been submitting their resumes to “pre-pub,” as they call it, that the wait time has increased significantly, two former senior intelligence officials told me on the condition of anonymity. “It’s a sign of the times,” one said. “A few have left and a lot are actively looking or are getting ready to look. That doesn’t necessarily mean they are going to leave. People are just worried about what the future holds.” Last week, the dual-hatted and widely respected Director of the NSA and Commander of U.S. Cyber Command, Gen. Timothy Haugh, was fired while abroad. The dismissal caught him by complete surprise. Now NSA employees are making their own preparations. They are thinking, “If I get fired, I need to be ready to find another job,” the other former official told me. But the backlog isn’t just about Haugh’s sudden termination, which appeared to be purely political. There was also Elon Musk’s “fork in the road email,” which introduced federal workers to a “deferred resignation” program. Of course, NSA’s personnel have also seen mass firings at other agencies, which becomes its own incentive. (Access here.)
Special Collections
Counterespionage - Recent arrests, convictions, expulsions, and more...
- China reveals espionage case involving overseas returnee recruited by foreign intelligence - Global Times, 11 Apr 25 (Member Contribution)
- Netherlands proposes anti-spy checks at universities - Euractiv, 09 Apr 25
- Houthi Militia Accused Of Kidnapping Civilians In Yemen's Hodeidah On Espionage Charges - Yemen Online, 09 Apr 25
- Sweden arrests senior Uyghur representative on suspicion of spying for China - The Record, 10 Apr 25
- Inside the downfall of Linda Sun, accused Chinese spy who worked for NY governors - Gothamist, 12 Apr 25
Cyberespionage - New actors, collection and sabotage ops, countermeasures, policy, other...
- Gamaredon: The Turncoat Spies Relentlessly Hacking Ukraine - Wired, 14 Mar 25
- In Secret Meeting, China Acknowledged Role in U.S. Infrastructure Hacks - Wall Street Journal, 10 Mar 25 (Member Contribution)
- Senator puts hold on Trump’s nominee for CISA director, citing telco security ‘cover up’ - Tech Crunch, 09 Apr 25 (Member Contribution)
- Top NSA, Cyber Command officials pulled from premier cybersecurity conference - NextGov, 08 Apr 25
- Germany suspects Russian cyber attack on research group - Deutsche Welle, 08 Apr 25
Covert Action - Influence ops, assassinations, sabotage, paramilitary ops, countermeasures, etcetera...
- Security officials report a Beijing-linked online operation focused on Carney - Canadian Broadcast Corporation, 07 Apr 25 (Member Contribution)
- Romanian arrested on espionage offences over DHL fire - BBC, 09 Apr 25
- The Russian disinformation campaign secretly rewriting Wikipedia - Digital Research Forensic Lab, 10 Apr 25
- Recruited by gangs, exploited by Iran: Intel sources say Swedish teens are being used to target Israeli interests - CNN, 08 Apr 25
- Kinetic Operations Bring Authoritarian Violence to Democratic Streets - Homeland Security News Wire, 11 Apr 25
Section II - DEEP DIVES
(Research Papers, OpEds, Analysis, Podcasts)
(Research Papers, OpEds, Analysis, Podcasts)
U.S.-Iran Nuclear Talks a Magnet for Spies - SpyTalk, 11 Apr 25 (Member Contribution)
If history and tradition hold, U.S. and Iranian spies will be hard at work trying to crack the secrets of the other side’s diplomatic strategies during the nuclear talks set to open Saturday in Oman. Each side’s espionage operations will range from efforts to bug meeting places and hotel rooms, to eavesdropping on diplomats’ phones, to piercing coded messages between delegates and their ministries back home, to bribing restaurant waiters to report on loose talk over dinner out in cosmopolitan Muscat, the capital. Nobody should be surprised by that, said two knowledgeable former senior U.S. officials. “This is standard operating procedure,” said one, a longtime veteran of Middle East intelligence operations, speaking on terms of anonymity to discuss the sensitive subject. “And, you know, we do it with everybody,” he added. (Access here.)
Russia’s FSB and Law Enforcement Tactics Suppress Opposition - Jamestown Foundation, 11 Apr 25 (Member Contribution)
The Russian Federal Security Service (FSB) is not just a security agency, but a key instrument of political repression aimed at suppressing opposition and dissent. In recent years, the FSB has shifted from ensuring real security to exerting political control over society. Unlike Western national security agencies, which focus on counterterrorism, organized crime, and foreign intelligence threats, the FSB primarily engages in domestic control. To achieve this, it employs intimidation, fabrication of criminal cases, and surveillance of political opponents of Russian President Vladimir Putin and his government. As a result, terrorist threats have intensified in recent years. The terrorist attack at Crocus City Hall in March 2024, the recent murder of high-ranking Ministry of Defense General Igor Kirillov, and other incidents are examples of how the FSB’s focus on domestic control has led to deteriorating national security in Russia. (Access here.)
Pentagon’s blind spot: How bureaucratic bungling is leading to the next intelligence catastrophe - Washington Times, 10 Apr 25 (Member Contribution)
The U.S. intelligence community is on a path to its next catastrophic failure. Despite warning signs, the Defense Department, which owns a massive portion of the intelligence community’s capabilities, is doing nothing to stop the next preventable disaster. The Pentagon conducts many intelligence activities, such as gathering information on foreign adversaries, protecting the nation from terrorist attacks and safeguarding military secrets from foreign intelligence entities. In fiscal year 2025, the intelligence community budget exceeded $100 billion, with a huge amount invested in military intelligence. Of the 18 intelligence community organizations, nine fall under the Defense Department, including five armed services intelligence elements, four major intelligence community agencies, service-affiliated intelligence agencies, and dozens of defense intelligence components throughout the defense agencies, combatant commands and the Joint Staff. (Access here.)
Sweden’s SÄPO Reports that Russia is Evolving Sabotage Tactics - Jamestown Foundation, 09 Apr 25 (Member Contribution)
Sweden’s Security Service (Säkerhetspolisen, SÄPO) reported in March that Russia is implementing a new espionage tactic. Russian intelligence is seeking prospective recruits suffering with substance addiction to carry out sabotage attacks in Sweden, with the police consequently being urged to heighten surveillance. The drug addicts are reportedly being sought because of their low social status and subsequent effective invisibility, a valued quality in espionage operatives (TV4 Nyheterna, March 17). SÄPO issued a press statement, provided in part below, as Russia seeks to further its covert espionage activities: "Foreign powers are using security-threatening activities and hybrid activities to destabilize Sweden and Europe. This involves illegal intelligence activities, influence, cyberattacks, theft of technology and knowledge, mapping, and threats against opponents. The Security Service can also note an increased Russian risk appetite with threats of sabotage also in Sweden (Säkerhetspolisen, March 11)." SÄPO previously reported that Iran uses criminal networks in Sweden to carry out various types of violent acts (Säkerhetspolisen, May 30, 2024). Moscow’s use of individuals suffering from substance addiction as tools for espionage demonstrates its heightened focus on “hybrid warfare” tactics, the incorporation of a “range of different modes of warfare,” against Europe. (Access here.)
The Tangled History of the State Secrets Privilege - Lawfare, 08 Apr 25
Recently, the Trump administration invoked the state secrets privilege in a case questioning the government’s compliance with a federal court’s order. This is a common law evidentiary privilege derived from the president’s “constitutional authority over the conduct of this country’s diplomatic and military affairs.” Although the contemporary understanding of this privilege is most often traced to the 1953 Supreme Court decision in United States v. Reynolds, its history and jurisprudential development is more complicated and fraught than current Reynolds-based analysis lets on. The exact basis for the state secrets privilege is hazy. Courts have complained that the privilege is “weakly rooted in our jurisprudence” and therefore “cannot and should not be a device for the government to escape [liability].” The Reynolds Court suggests that the privilege arises out of the separation of powers, while other courts have looked to the president’s authority as commander in chief under Article II. Perhaps most troubling, however, is the expansion over time of both the use and parameters of the privilege along with courts’ conflation of the privilege with the bar to litigation, articulated by Totten v. United States. (Access here.)
Taiwan: China's Testing Ground for Intelligence Operations (32 min) - SpyCast Podcast, 08 Apr 25
It's no secret that China has recently stepped up political and military pressure on the democratically governed island of Taiwan. But then, there are the Chinese Communist Party's covert efforts: Recruiting from the inside, gathering intelligence, and exerting influence. Executive Director of the Global Taiwan Institute Russell Hsiao breaks down Beijing Shadow Games in Taiwan. (Access here.)
Britain’s Spymasters — The Kremlin’s Most Feared Enemy - Center for European Policy Analysis, 08 Apr 25
While the US administration keeps seeking a deal with Putin, Moscow’s spy masters are shifting their attention to the confrontation with their two main adversaries in Europe. These are the British and French intelligence agencies, though for different reasons. Russian intelligence mandarins have always been obsessed with the British, considering them much superior in spy craft than the Americans, and the Cold War didn’t really affect that judgment. After all, the British are the only intelligence agency ever accused of directly plotting to overthrow the regime in Moscow (apart from Vladimir Lenin’s relationship with the Germans during World War I, still an embarrassment for the official historic narrative). It hardly matters to a paranoid Kremlin that this attempt occurred more than a hundred years ago, soon after the Russian Revolution of 1917. The British had a significant intelligence operation in post-revolutionary Russia, originally to support and observe its wartime ally, and ultimately to subvert the Bolshevik regime and its calls for global revolution. (Access here.)
Section III - FORMERS' FORUM
(Legacy Intel Practitioners' Informed Perspectives
and Recent Endeavors)
(Legacy Intel Practitioners' Informed Perspectives
and Recent Endeavors)
I helped Biden defend against national security threats. NSA needs skilled leaders not politics. - by former Assistant Secretary of State for INR and former acting director of the National Counterterrorism Center Brett M. Holmgren - Fox News, 10 Apr 25 (Member Contribution)
The first thing I read each morning for the last four years was the top-secret President’s Daily Brief – a summary of the most sensitive intelligence and analysis on global issues. From the president on down to cabinet members and other senior officials, we relied on that summary to warn us about China’s aggressive cyber operations, terrorist plots, Iran’s malicious activities, and other geopolitical risks. Invariably, these insights were derived mostly from intelligence collected by one entity: the National Security Agency. Why? Because in a world defined by digital communications and technology, the NSA is America’s most effective intelligence service. (Access here.)
Qatar Told Hamas to Keep Israeli Hostages - with former U.S. Intelligence Officer Michael Pregent - Haaretz, 10 Apr 25 (Member Contribution)
In September 2024, Michael Pregent briefly shook hands with Prime Minister Benjamin Netanyahu, managing to ask him about Qatar, Israel and the hostages in Gaza. "That is a problem," Netanyahu replied. Then, according to Pregent, he rolled his eyes, signaling anger or boredom. Pregent - a former U.S. intelligence officer and until recently a senior fellow at the conservative Hudson Institute in Washington - visited Israel about six months ago on a trip with a group of fellow researchers, during which they met Netanyahu. He is regarded as one of Qatar's fiercest critics, viewing it as a corrupt country that supports terrorist organizations, buys influence with money and is willing to bribe politicians around the world. His sharpest criticism is directed not only at Qatar, but also at the United States - particularly certain institutions, universities, influencers, journalists, government officials and civil servants. Just four days after President Donald Trump entered the White House, in January, Pregent was ousted from the Hudson Institute, where he had served for a decade as a senior research fellow specializing in Iran and the Middle East. (Access here.)
What the ‘Signalgate’ Snafu Overlooks - by Former CIA Senior Analyst Michael Ard - Discourse Magazine, 08 Apr 25(Member Contribution)
Last month, National Security Adviser Mike Waltz blundered by adding journalist Jeffrey Goldberg to his Signal app group chat for a Principals Committee meeting, which includes the most senior national security policymakers, on plans to attack Yemen’s Houthi outlaws. He also erred in not making the participants identify themselves in the chat, which would have outed Goldberg and prevented him from reporting on the meeting. Classified information was discussed in the chat, particularly specifics about when our military would strike the Houthis and about the post-attack damage assessment. About the attack: Well done. It was about time. The Houthis have been firing at U.S. warships for over a year and still are. We needed to strike at their leadership. About the meeting: Not good. Don’t include adversarial journalists in your secret national security discussions. And even though Signal is an end-to-end encrypted app—which no one claimed was compromised—this high-level discussion on national security should not have occurred on an unauthorized civilian messaging system. And if some participants were using the app on their internet-connected smartphones, that would raise even more security concerns. Some experts have even suggested that administration officials could be prosecuted under the 1917 Espionage Act, even though before this dust-up, many commentators regarded that law as being in woeful need of reform. (Access here.)
American academia and Chinese espionage go hand-in-hand by former NSA Counterintelligence Officer John Schindler - Washington Examiner, 08 Apr 25
Is the missing Midwestern professor merely a rogue researcher — or a Chinese spy? The academic, whose current whereabouts are unknown, is Xiaofeng Wang, a native of the People’s Republic of China and a certified star in the rarified world of cryptography and cybersecurity. Wang and his wife, Nainli Ma, have been missing since the Federal Bureau of Investigation raided two of their Indiana homes on March 28, the same day that Wang was fired by Indiana University. Ma, an IU library systems analyst, was fired the same day as her husband. Wang had been on the IU faculty since 2004, fresh from receiving his doctorate in electrical and computer engineering from Carnegie Mellon University. He previously received undergraduate and master’s degrees in his native China. Wang’s rise at IU was accomplished with a promotion to full professor in 2015, followed two years later by his appointment to a prestigious named chairman in IU’s Luddy School of Informatics, Computing, and Engineering. Wang was a standout at the Luddy School, winning numerous research grants for his cutting-edge work in computers and codes. Wang collaborated in well-funded projects with universities across the United States and around the world. (Access here.)
Information War: The U.S. Surrenders by former CIA Senior Operations Officer John Atwell - Hawaii Tribune Herald, 08 Apr 25
Most of us islanders enjoy the bliss of ignorance about the underworld—espionage against our nation, organized crime in our cities, assassinations on U.S. soil by foreign adversaries. There is, however, one element of the Dark Side that touches us all, even in Paradise—the information war. It is subtle, long-standing, ongoing, has covert and overt elements, and pits Western ideals (freedom, democracy) against others, like Russia and China’s communism, Iran’s militant theocracy, or India’s religious nationalism. That said, Washington this month began disarming our nation’s front line fighters in this conflict. Tasked with carrying pro-democracy and pro-Western messaging into denied areas and hostile territory, they sit on the chopping block—Radio Free Asia, Radio Free Europe, the Office of Cuba Broadcasting, Middle East Broadcasting Network, the Voice of America, and the Open Technology Fund (which provides uncensored Internet access to people living under repressive regimes). Called “the hard edge” of U.S. soft power, and fighting fascism and communism throughout the 20th century, their effectiveness is proven by the amount of money that adversaries spend trying to block them. Consider that VOA alone broadcasts in 50 languages and reaches a target audience of 345 million listeners. The platforms penetrate the intangible, darkest corners of our globe’s ideological worlds—Central Asia, tribal regions of South Asia, North Korea—and are infinitely cheaper than physical weapons needed when ideological conflicts move onto physical battlefields. (Access here.)
Section IV - BOOKS, FILM, HISTORY, POP CULTURE
 The Illegals: Russia's Most Audacious Spies and Their Century-Long Mission to Infiltrate the West
The Illegals: Russia's Most Audacious Spies and Their Century-Long Mission to Infiltrate the West
by Shaun Walker
(Knopf, 15 Apr 25)
More than a century ago, the new Bolshevik government began sending Soviet citizens abroad as deep-cover spies, training them to pose as foreign aristocrats, merchants, and students. Over time, this grew into the most ambitious espionage program in history. Many intelligence agencies use undercover operatives, but the KGB was the only one to go to such lengths, spending years training its spies in language and etiquette, and sending them abroad on missions that could last for decades. These spies were known as “illegals.” During the Second World War, illegals were dispatched behind enemy lines to assassinate high-ranking Nazis. Later, in the Cold War, they were sent to assimilate and lie low as sleepers in the West. The greatest among them performed remarkable feats, while many others failed in their missions or cracked under the strain of living a double life. Drawing on hundreds of hours of interviews, as well as archival research in more than a dozen countries, Shaun Walker brings this history to life in a page-turning tour de force that takes us into the heart of the KGB’s most secretive program. A riveting spy drama peopled with richly drawn characters, The Illegals also uncovers a hidden thread in the story of Russia itself. As Putin extols Soviet achievements and the KGB’s espionage prowess, and Moscow continues to infiltrate illegals across the globe, this timely narrative shines new light on the long arc of the Soviet experiment, its messy aftermath, and its influence on our world at large.
Order book here.
 Cracking the Nazi Code: The Untold Story of Agent A12 and the Solving of the Holocaust Code
Cracking the Nazi Code: The Untold Story of Agent A12 and the Solving of the Holocaust Code
by Jason Bell
(Pegasus Books, 30 Apr 24)
In public life, Dr. Winthrop Bell was a Harvard philosophy professor and wealthy businessman. As an MI6 spy—known as secret agent A12—in Berlin in 1919, he evaded gunfire and shook off pursuers to break open the emerging Nazi conspiracy. His reports, the first warning of the Nazi plot for World War II, went directly to the man known as C, the mysterious founder of MI6, as well as to various prime ministers. But a powerful fascist politician quietly worked to suppress his alerts. Nevertheless, Dr. Bell's intelligence sabotaged the Nazis in ways only now revealed in Cracking the Nazi Code. As World War II approached, Bell became a spy once again. In 1939, he was the first to crack Hitler’s deadliest secret code: Germany’s plan for the Holocaust. At that time, the führer was a popular politician who said he wanted peace. Could anyone believe Bell’s shocking warning? Fighting an epic intelligence war from Eastern Europe and Russia to France, Canada, and finally Washington, DC, Agent A12 was a real-life 007, waging a single-handed struggle against fascists bent on destroying the Western world. Without Bell’s astounding courage, the Nazis just might have won the war.
Order book here.
 Covert Action in the Cold War: US Policy, Intelligence and CIA Operations
Covert Action in the Cold War: US Policy, Intelligence and CIA Operations
by James Callanan
(I.B. Taurus, 15 Dec 09)
Born out of the ashes of World War II, the covert action arm of the Central Intelligence Agency (CIA) was created to counter the challenge posed by the Soviet Union and its allies and bolster American interests worldwide. It evolved rapidly into an eclectic, well-resourced organization whose activities provided a substitute for overt military action and afforded essential backup when the Cold War turned hot in Korea and Vietnam. This comprehensive examination of a still controversial subject sheds valuable new light on the undercover operations mounted by the CIA during the Cold War. Using a wide range of unpublished government records and documents, James Callanan traces the growth of the agency chronologically as it forged a covert action mission that sought to advance US foreign and defense policy in all corners of the globe. Offering a powerful perspective on a pivotal period in American history, "Covert Action in the Cold War" makes a crucial contribution to our understanding of global politics during the Cold War.
Order book here.
Intelligence Matters on Film - The Tailor of Panama - John Boorman (2001)
 John le Carré's spy thriller is brought to the big screen. A British spy is banished to Panama after having an affair with an ambassador's mistress. Once there he makes connection with a local tailor with a criminal past and connections to all of the top political and gangster figures in Panama. The tailor also has a wife, who works for the canal administrator, and a huge debt. The spy's mission is to learn what the President intends to do with the Panama Canal, but he's really in business for himself, blackmailing the tailor into spinning a fantastic tale about the canal being sold to China and former mercenaries ready to topple the current government. Featuring Pierce Brosnan, Jamie Lee Curtis. Fictional account.
John le Carré's spy thriller is brought to the big screen. A British spy is banished to Panama after having an affair with an ambassador's mistress. Once there he makes connection with a local tailor with a criminal past and connections to all of the top political and gangster figures in Panama. The tailor also has a wife, who works for the canal administrator, and a huge debt. The spy's mission is to learn what the President intends to do with the Panama Canal, but he's really in business for himself, blackmailing the tailor into spinning a fantastic tale about the canal being sold to China and former mercenaries ready to topple the current government. Featuring Pierce Brosnan, Jamie Lee Curtis. Fictional account.
More about this production here.
Intelligence in History - A Collection of Recently Released Content
- How the famed secret agent Oleg Gordievsky escaped the Soviet Union and certain death - The Week, 13 Apr 25
- James Fulton: MI6 Far East Controller c.1955 - Tom Griffin on Intelligence History, 13 Apr 25
- 'I am not who you think I am': how a deep-cover KGB spy recruited his own son - The Guardian, 10 Apr 25
- Gordievsky’s role in the Able Archer 1983 ‘War Scare’: Some Synthetic Evidence - Intelligence Studies Review, 08 Apr 25
- Declassified JFK Files Provide “Enhanced Clarity on CIA Actions, Historian Says - Homeland Security News Wire, 09 Apr 25
Walking Tours - "Spies of Embassy Row" and "Spies of Georgetown" - Washington, DC - Sundays (Dates/Times Vary)
Former intelligence officers guide visitors on two morning and afternoon espionage-themed walking tours: "Spies of Embassy Row" and "Spies of Georgetown." For more information and booking, click here or contact rosanna@spyher.co
Section V - Obituaries and Classifieds
(Research Requests, Academic Opportunities, Employment)
Obituaries
![]() Mark Klein — NSA Whistle Blower (Member Contribution)
Mark Klein — NSA Whistle Blower (Member Contribution)
Mark Klein, a whistleblower who revealed domestic spying, dies at 79. The AT&T technician predated Edward Snowden by seven years, but his allegations were never able to achieve traction. See full obituary here.
![]() Clint Hill — Former USSS Officer Who Ran to JFK's Car (Member Contribution)
Clint Hill — Former USSS Officer Who Ran to JFK's Car (Member Contribution)
Clint Hill, 93, remembered as the devoted agent who ran to JFK’s car in Dallas and who shielded Jacqueline Kennedy passed on 21 February at his home in Belveder, CA, with a deep guilt that haunted him late into his life. See full obituary here.
Research Requests and Academic Opportunities
- Call for Information: Robert Stock was born on December 29, 1916 in Hamilton, Ohio and died on October 25, 1983 in Queens, New York. He entered the U.S. Army in 1941 as a private, eventually being promoted to captain. His Selective Service Number was 0-1640045. He served as an intelligence officer, possibly with the Office of Strategic Services. He was discharged from the Army shortly after the end of World War 2. He subsequently joined the CIA in May of 1950. He was assigned to the staff of the military attaché in Yugoslavia. Soon after starting his assignment in Yugoslavia, he was sent to Budapest, Hungary, ostensibly to deliver diplomatic messages to the U.S. embassy. However, his main purpose was to contact the main agent there to give that agent verbal instructions about passing information and forming an intelligence ring. He was arrested on the way by a Hungarian counter-intelligence man and sent to a Hungarian prison. During the Hungarian Revolution in 1956, he was released from prison by the revolutionaries and was allowed to go immediately to the U.S. Embassy for asylum. He then found out that his identity had been “erased” by U.S. intelligence authorities, which was done for the purpose of protecting the intelligence network that he had helped set up. He was flown to Vienna and then to an Air Force hospital in Germany while his statements about who he was were being verified. He was told not to communicate with anyone beyond his commanding officer and a psychiatrist at the hospital who was treating him. He subsequently left the CIA, probably sometime in 1956. For decades, numerous family members have attempted to find out the details of Robert’s life while he was in the CIA, with very limited success. The last contact anyone in his family had with him was a short visit he made to his brother in Albany, New York in 1957. If anyone has information on Robert, please contact his nephew, Mike Brunner at: mbrunner1@cinci.rr.com or 513-379-9734 or by mail at 351 Warren Avenue, Cincinnati, Ohio 45220.
- Call for Information: Researcher working on project about her mother, a former CIA SE division desk chief, seeking former branch chiefs in the division between 1980 and 1994 to help with general descriptions of interrelationships and information flow. Also seeking officers who were in Rome station anytime between 1986-90. Please contact viveca.novak@gmail.com.
- Call for Study Participants: Are you a current or former intelligence professional interested in contributing to research on how intelligence and decision-makers collaborate? We are seeking individuals with professional experience in intelligence operations, either in current or previous roles within law enforcement, military departments, federal agencies, or the private sector. We are particularly interested in those who have been involved in collecting, analyzing, and disseminating intelligence that directly informs organizational goals/missions. We also seek those who have been in roles who make decisions based on such intelligence. This study involves an interview lasting approximately 1 hour to explore your experiences and contribute to a deeper understanding of this critical area of collaboration. If you are interested in participating or have questions regarding whether you qualify, please email me at carlos.lopez@unt.edu.
- Call for Information: CIA in 1970 FIFA World Cup or 1968 Olympic Games. Did the CIA watch soccer? I’m a British journalist and documentary maker (20 years at the BBC, now independent) working on a historical podcast series focusing on the 1970 FIFA World Cup (soccer), as well as the 1968 Olympic Games. I am trying to understand what operational interest, if any, the CIA took in these two sporting events, particularly in the context of the Cold War in Latin America. Since both events took place in Mexico, I am keen to speak to anyone specifically about either the CIA Mexico station at that time (under Win Scott and later John Horton), or - for broader context - about the Agency’s historical interest in sporting matters more generally. Anyone with insight into the involvement of the Brazilian government or security agencies in soccer during the 1970 World Cup (under Gen Medici) would also be of interest. I can be contacted at gabriel.gatehouse@gmail.com. Discretion is, of course, assured.
- Academic Opportunity: The International Security & Intelligence Programmer at Emmanuel College in the University of Cambridge, Summer 2025. Residential Programmer: Cambridge, Sunday 6 July to Saturday 2 August 2025. See flier with full details here.
- Information Sought: Researcher is seeking information about the document known in the West as the “KGB Wanted List,” the 1969 version of which was brought to the West by a KGB defector in 1972. Vladislav Krasnov analysed a portion of the list in his 1986 book titled “Soviet Defectors.” Both CIA and the FBI responded to FOIA requests indicating that they cannot find the 1969 list (although both CIA and NACIC have cited it in various forums). If you have a copy of the 1969 list, suggestions where it might be found in its entirety, or knowledge of any earlier lists in the series, please contact Kevin Riehle at kevin.riehle@brunel.ac.uk.
- Call for Collaboration: AFIO member seeks a collaborator with YouTube technical expertise to launch a channel that will highlight specific examples of Russian and Chinese misinformation. Please contact Greg Rushford at gregrushford@gmail.com.
- Internship Opportunity: U.K.-based private intelligence company Grey Dynamics is accepting applications for its analyst internship program. Excellent resume building experience for aspiring intel analysts and, for intelligence studies students (and graduates) who are interested in analysis and writing, a great entry-level opportunity to exercise your skills in a real editorial and publication setting. See full details and application instructions here.
- Call for Information: Child of former CIA Como Officer Walter E. McLeod seeks information on her father's life and work to help build a better understanding of the family's history. McLeod EODed in 1951 and served in Saipan, Havana, WTC, Caracas, Jakarta, Saigon, Paris, Phnom Penh, Vientiane, and Bangkok. He retired in 1975. If you have information to share, contact Kathy McLeod katherinemacleod@gmail.com.
Jobs
- Director, School of Criminology and Security Studies, Full Professor or Associate Professor - Indiana State University - Terre Haute, Indiana
- Open-Source Intelligence Laboratory and Professor of Intelligence and National Security Studies - University of Texas at El Paso - El Paso, Texas
- 2 Assistant Professors in Intelligence and Security - Institute of Security and Global Affairs, University of Leiden - Netherlands
- Assistant Professor of Intelligence Studies - Mercyhurst University - Erie, Pennsylvania
- Associate Professor and Chair of National Security - University of New Haven, Connecticut
- Wanted: Former intelligence officers to lead spy-themed walking tours in Washington D.C. - Spyher Tours
- Assistant/Associate Professor of Intelligence Studies (Global Security and Intelligence Studies) - Embry-Riddle Aeronautical University - Prescott, Arizona
Provide academic and administrative leadership within a School of approximately 500+ undergraduate majors and master’s students as well as 29 full and part-time faculty. Oversee and facilitate the School's resources. Provide support for teaching, research, service, recruitment, retention, and fundraising. Be an advocate for experiential learning and represent the School of Criminology and Security Studies effectively in college, university, and community matters. Teach and publish in expertise area. Promote interdisciplinary collaboration and innovation. Participate in external and community engagement to cultivate partnerships, funding opportunities, and promote the School. Full details on qualifications, duties, and application here.
The Department of Criminal Justice & Security Studies at the University of Texas at El Paso (UTEP) is seeking to fill a faculty position for a new open-source intelligence (OSINT) laboratory, created to be the first of its kind to study the complex security issues within the U.S.-Mexico border region. The faculty member will lead efforts to establish the nation's premier institution analyzing U.S. Mexican border security, including how it is impacted by political, social, physical, and economic forces across (and beyond) the Western Hemisphere. The laboratory will use cutting edge OSINT techniques, build databases, help create scholarly research and analytical reports, and assist students in developing career relevant skills. This will be a full-time, tenured position beginning in Fall 2025. The faculty member will hold the rank of associate professor or professor. Responsibilities include developing and directing the laboratory, obtaining external funding, and publishing scholarly research. The faculty member will teach courses and mentor students in open-source intelligence analysis. They will work closely with community partners across the university and in the public and private sectors in support of the laboratory and the Department. Full details on qualifications, duties, and application here.
The successful candidates will have demonstrable research records in themes related to the vacancy and strong teaching background in intelligence and security, or a related field, as well as in topics related to the Institute's Bachelor's and Master's programme offerings. The candidate will be expected to teach across several programmes in the Institute, notably the master's programme Crisis and Security Management and the bachelor programme Security Studies, and our minor in Intelligence Studies. The positions are aimed at strengthening the Institute's teaching, research and grant-acquisition capacities in a phase of growth and exciting interdisciplinary research opportunities. Full details on qualifications, duties, and application here.
Mercyhurst University in Erie, PA, invites applications for the position of Assistant Professor of Intelligence Studies in the School of Intelligence, Computing and Global Politics. The position is at the Erie campus and begins Fall Semester 2024. Successful candidates will teach introductory and applied courses in Crime and Law Enforcement intelligence analysis at the undergraduate and graduate levels, in addition to the ability to teach undergraduate or graduate courses in: Leadership in Intelligence; Advanced Analytic Techniques; Intelligence Collection and Analysis. Additional information and application instructions here.
The Department of National Security invites nominations and applications for a tenured Full/Associate Professor and Chair of National Security. The department includes a dynamic undergraduate program encompassing four distinct bachelor's degrees (Security & Defense Policy, Intelligence Analysis, Homeland Security, and International Affairs), a robust master's degree program, and several practitioner-oriented certificates. Qualifications: A terminal degree in national security, public policy, political science, or related field is required; Ph.D. preferred. The successful applicant will have a record of teaching excellence at the university level, established catalog of academic publications, and an innovative research agenda. Applicants should also possess experience in university-level service and leadership. The department is particularly interested in candidates with policymaking experience in national security at either the federal, state, or local level. Tenurable Assistant Professors may also be considered in accordance with the aforementioned qualifications. Application Instructions: Please submit a brief cover letter explaining teaching experience and philosophy, publication record, practitioner-oriented experience (if applicable), CV, and the name and contact information for three references. Applicants may also include up to 3 artifacts of teaching ability (examples include syllabi, student evaluations, learning exercises, assignments, or other feedback) that illustrate teaching experience. More information and application here or contact Search Committee Chair, Dr. Jeffrey Treistman at jtreistman@newhaven.edu.
These are 90-120 minute historical tours with an interactive "operational" component. Most tours start at 10am on select Thursdays-Sundays. The immediate opportunity is for dates in March, but additional opportunities are available through June, and new opportunities are likely to become available throughout the year. This is a fun way to get back out on the streets, engage/educate the public on the world of espionage, and make some extra cash. The next opportunities to see a tour in action (and train before the Spring rush) are Sunday 2/18 and Sunday 3/3. Please contact Rosanna at 571-236-9052 or rosanna@spyher.co. Visit https://spyher.co.
Embry-Riddle Aeronautical University's Prescott, Arizona campus is accepting applications for a tenure-track assistant or associate-level professor of intelligence studies to teach intelligence courses to students in the Global Security and Intelligence program. The successful candidate will teach students about the intelligence community, strategic intelligence, the intelligence cycle and intelligence analysis, writing, and briefing. Prior experience working in the intelligence community is strongly preferred. We are interested in candidates with teaching acumen in intelligence analysis and writing using structured analytical techniques.
Additional information and application here.
AFIO Events
Tue, 22 Apr 2025, 12:00pm EDT - Tampa, FL and virtual - The Florida Suncoast AFIO Chapter luncheon features COL Mike McCalister (US Army, RET) speaking on "Current Global and National Challenges facing the United States." The Florida Suncoast AFIO Chapter is holding a luncheon at noon on Tuesday, 22 April 2025, in the Tournament Room at the MacDill AFB Bay Pines Golf Complex, 1803 Golf Course Ave, MacDill AFB, FL 33621. Our speaker is COL Mike McCalister (US Army, RET) speaking on "Current Global and National Challenges facing the U.S." This is an unclassified but sensitive meeting. Strict non-attribution rules apply (Chatham House Rule). The luncheon includes a box lunch and costs $25. Reservations and arrangements for Base access must be completed no later than noon on Sunday, 13 April 2025, including arrangements for base access and food selection.
If you wish to participate by ZOOM, please click on this registration link to complete the registration request before noon on Sunday, 13 April 2025. This is NOT the ZOOM meeting link. Subject to approval, you will receive the ZOOM meeting link by separate email. Please check your ZOOM program in advance to ensure it is working properly and that you have the confirmed ZOOM meeting link handy to join the meeting. It is next to impossible to trouble-shoot ZOOM connections on the day of the meeting.
Please contact Michael Shapiro, Chapter Secretary, for more information, mfshapiro@suncoastafio.org.
Wed, 7 May 2025, 11:30am PDT - in-person - AFIO LA Chapter hears Adm James Stavridis, a CNN Military Analyst, on "Trump Administration Policies' Impact on International Security". This AFIO L.A. meeting features CNN Military Analyst and Former Supreme Allied Commander of NATO, Admiral James Stavridis (Ret) discussing "the Trump Administration's Policies' Impact on International Security.". Cost: $75 Buffet Lunch & Book Included. RSVP: Email your reservation request to: afio_LA@yahoo.com. Deadline for reservation: April 14, 2025. Program Details: 11:30 am - 12:00 pm: Check-In & Buffet Lunch; 12:10-12:25 pm: Presentation by Adm. Stavridis; 12:25-12:55 pm: Fireside chat; 12:55-1:25 pm: Q&A; 1:30-2:00 pm: Book Signing.
Location: American Legion Post 43, 2035 N Highland Ave, Los Angeles, CA 90068.
BIOGRAPHY: James Stavridis, former Supreme Allied Commander of NATO and Commander of U.S. Southern Command. A distinguished four-star admiral with over 30 years of service in the U.S. Navy, he commanded military forces across Latin America, Europe, and beyond. A leading global affairs expert, best-selling author, and Senior Military Analyst for CNN, Admiral Stavridis will share his insights on the challenges and opportunities facing the new U.S. administration, the wars in Ukraine and Gaza, and the evolving geopolitical landscape with China.
Wed, 28 May, 2025, 11:30am no host cocktails, Noon meeting - In-Person, San Francisco CA - "The Language of War" by LTC Christopher Gin, DLI 229th Military Intelligence Battalion Commander and Visiting Scholar, Center for International Security and Cooperation, Stanford University
Topic: "The Language of War: Modern Language Training at the Defense Language Institute Foreign Language Center"
Speaker: LTC Chris Gin, Former DLI 229th Military Intelligence Battalion Commander and Visiting Scholar, Center for International Security and Cooperation, Stanford University
Time: 11:30am no-host cocktails, 12 noon talk begins
Location: In-Person at the Basque Cultural Center, 599 Railroad Ave, South San Francisco, CA 94080
RSVP required here.
Questions? Contact Mariko Kawaguchi, Board Secretary, AFIO SF Chapter at afiosf@aol.com.
LTC Christopher Gin commanded the 229th Military Intelligence Battalion at the Defense Language Institute from 2022-2024. He is currently an Army War College Fellow at the Freeman Spongli Institute for International Studies at Stanford. LTC Gin is a 2005 graduate of the U.S. Military Academy at West Point with a BA in English/Chinese Studies and an MA from the University of Hawai'i in Asian Studies, where he was a graduate degree fellow with the East–West Center. Throughout his career, he has held various operational intelligence leadership positions in FORSCOM, SOCOM, and TRADOC, and will continue his service this summer with the US Army Pacific in Hawai'i.
Wed, 16 Apr 2025, 6:30pm – Washington, DC – Rogue Agent with James Crossland – Virtual and In-Person International Spy Museum Program - Diplomat, conspirator, intelligence gatherer, propagandist, and charmer, Sir Robert Bruce Lockhart was London's key agent in Moscow during the first half of the twentieth century. Join Dr. James Crossland, author of Rogue Agent: From Secret Plots to Psychological Warfare: The Untold Story of Robert Bruce Lockhart. Lockhart was an impressive figure who played a vital role in both world wars. He was a man who charmed his way into the confidences of everyone from Leon Trotsky to Anthony Eden. A man whom the influential press baron Lord Beaverbrook claimed, "could well have been prime minister." And yet Lockhart died almost forgotten and near destitute, a Scottish footnote in the pages of history. Crossland has drawn from years of research into private papers, top secret documents, and the memoirs and diaries of those who knew Lockhart best, as well as the numerous works penned by Lockhart himself, to write the first biography of this unconventional character. The discussion will explore this flawed maverick from his time as Britain's agent in Moscow and his role in a plot to bring down the communist regime to his leadership in the Political Warfare Executive—a secret body responsible for disinformation and propaganda during World War II. Famed spy Sidney Reilly will also be touched on as the Spy Museum has on view the only physical evidence that links Lockhart and Reilly to their 1918 plot against Russia's Bolshevik regime! Rogue Agent will be available for sale and signing after the conversation. Visit www.spymuseum.org.
Thurs, 17 Apr 2025, 12:00-1:00pm – Washington, DC – Spy Chat with Special Guest Jen Easterly – Virtual International Spy Museum Program Join us for an online discussion of the latest intelligence, national security, and terrorism issues in the news. Spy Museum Executive Director Chris Costa, a former intelligence officer of 34 years, will be joined by Jen Easterly, former Director of the U.S. Cybersecurity and Infrastructure Security Agency (CISA). As the Director of CISA, America's premier cyber defense agency, Easterly led the nation's efforts to protect critical infrastructure from cyber and physical threats, transforming the agency into a $3 billion operation with over 10,000 employees and contract personnel. Before CISA, she served as Head of Firm Resilience at Morgan Stanley, where she built and led the company's Cybersecurity Fusion Center, charged with protecting the Firm from cyber threats. Easterly's public service spans more than three decades, including multiple combat deployments in the U.S. Army, where she played a pivotal role in the creation of U.S. Cyber Command and commanded the Army's first cyber battalion. She served twice at the White House, including as Special Assistant to President Obama and Senior Director for Counterterrorism and earlier as Senior Policy Advisor to National Security Advisor Condoleezza Rice. She also served as the Deputy for Counterterrorism at the National Security Agency (NSA) and as a senior leader in Tailored Access Operations, NSA's elite hacking team. A distinguished graduate of West Point and Rhodes Scholar, Easterly is a two-time recipient of the Bronze Star as well as numerous awards, including the 2018 James W. Foley American Hostage Freedom Award. Visit www.spymuseum.org.
Tues, 22 Apr 2025, 2:00-3:00pm – Washington, DC – SPY with Me: Program for Individuals with Dementia and their Care Partners – Virtual International Spy Museum Program SPY with Me is an interactive virtual program for individuals living with dementia and their care partners. Join SPY as we use music and artifacts to explore some of our favorite spy stories. Programs last one hour and are held virtually through Zoom. To register, please email Shana Oltmans at soltmans@spymuseum.org. Free but space is limited. Visit www.spymuseum.org.
Wed, 30 Apr 2025, 1200-1300 (ET) – Virtual – Inside Intelligence presents "Domestic Intelligence is Broken" with Donell Harvin - Johns Hopkins University. Join Michael Ard, MS in Intelligence Analysis program director, for an Inside Intelligence webinar discussion with Donell Harvin, a homeland security expert from Washington, DC. Harvin is a Visiting Scientist at Harvard School of Public Health where he oversees the Harvard Humanitarian Initiative’s CBRNE research and training program. He also serves in an adjunct faculty role in several schools at Georgetown University, teaching terrorism, homeland security, and intelligence. He routinely provides expertise to MSNBC/NBC News, CNN, Politico, INTERPOL, and the UN Office of Counter Terrorism. Harvin’s public safety career spans over 30 years and includes executive roles in fire/EMS, law enforcement, forensics, countering weapons of mass destruction, homeland security, and intelligence. A member of the FDNY on 9/11, he has also provided analysis on the Sandy Hook school shooting, the January 6th attack on the U.S. Capitol, and, most recently, WMD disaster-related capacity building activities within Ukraine. He holds graduate degrees in emergency management, terrorism studies, and environmental science, and a Doctor of Public Health degree, with a focus on environmental epidemiology and biohazards. More information and registration here.
Thurs, 15 May 2025, 6p-8p - Washington, DC - The Art of Building Relationships at The Octagon Museum and oldest private residence in Washington D.C. Dolley Madison was outgoing, energetic, fun-loving, kind and a great Washington socialite. In honor of her birthday we gather to address (and practice) the art of building relationships. Intelligence officers around the world live this practice and Spyher is pleased to address the key components of relationship building in this 1-hour program, followed by a 1-hour mix-and-mingle. Join SPYHER to hear more about Trust, Communication, Empathy, Respect and more. Book your attendance here.
30 Aug - 8 Sep 2025 - Mediterranean Cruise - Spies, Lies & Nukes announce Espionage on the High Seas! Plan NOW to join the late-summer 2025 cruise. Instead of their traditional Spies, Lies & Nukes conference in 2024, Valerie Plame and other intelligence colleagues are thrilled to introduce an exciting variation for 2025: Spies at Sea. A combined cruise and conference through the breathtaking Mediterranean, from
August 30 to September 8, 2025! See brochure here.
What to Expect:
• Intimate Conference Setting: Enjoy the same close-knit, engaging environment you've come to expect, with unparalleled access to our expert speakers.
• Exclusive Shore Excursions: Explore clandestine meeting spots, delve into espionage history, and more on excursions EXCLUSIVE TO OUR GROUP.
• Seminars at Sea: Participate in lectures and presentations led by Valerie Plame and other top intelligence professionals, all the while cruising through some of the Mediterranean's most iconic destinations.
• Special Events: Enjoy exclusive cocktail receptions, surprise activities, and one-on-one conversation time.
Exclusive Spies, Lies & Nukes Itinerary Highlights:
• Barcelona, Spain: Begin your adventure in this vibrant city.
• Valletta, Malta: Walk through history with guided tours led by espionage experts who will lift the veil on area spy stories and meeting sites.
• Mykonos, Greece: Discover the charm and beauty of this picturesque island.
• Ephesus, Turkey: Explore ancient ruins with a private guide and enjoy a unique group lunch, all while learning about intelligence activities that took place at each spot.
• Santorini, Greece: Experience the iconic beauty of Santorini with endless photographic opportunities.
• Naples, Italy: Enjoy a group lunch at a local restaurant and an exclusive walking tour with a private guide while learning a few spy secrets from Naples,
Capri, and the Amalfi Coast.
We've secured a discounted rate that includes your stateroom, meals, classic beverage package, wi-fi, exclusive excursions, and all conference activities. These
cabins will get booked quickly, so don't wait—
 Gray long-sleeved polo shirts with embroidered AFIO logo. Men's sizes only.
Gray long-sleeved polo shirts with embroidered AFIO logo. Men's sizes only.
Show your support for AFIO with our new Gray Long-sleeve Polo Shirts. Shirts are shrink and wrinkle resistant of fine cotton with a soft, "well-worn, comfy" yet substantial feel. They feature a detailed embroidered AFIO seal. Get a shirt for yourself and consider as gifts for colleagues, family, and friends. Only $60 each including shipping.
Sizes for men, only: Small, Medium, Large, XL, XXL, and XXXL. $60 per shirt. Order this and other store items online here.
 20 oz ceramic Mug with color glazed logo. Made in America. Check out our new tapered, sleek AFIO coffee mug!! This handsome 20 oz. ceramic mug is made in the USA, has a white matte exterior, sports a beautiful navy-blue interior, and is dishwasher safe. Order yours today! $35 per mug includes shipping to a CONUS address. [includes shipping to U.S. based address, only. For foreign shipments, we will contact you with a quote.] SHIPPING: For shipment to a U.S.-based CONUS address, shipping is included in price. For purchases going to AK, HI, other US territories, Canada, or other foreign countries the shipping fees need to be calculated, so please call our office M-F 8 a.m. to 2 p.m. ET at 703-790-0320 or email afio@afio.com providing following information: 1) your name, 2) mailing address (or addresses where each gift item will be shipped), 3) name of the AFIO store items you wish to purchase, 4) quantity of each, 5) your credit card number and expiration date, 6) amount (except for additional of shipping fees) authorized to charge, and 7) your phone number and email should we have questions. Foreign shipments fees will be calculated and estimates emailed to you, awaiting your approval. Order this and other store items online here.
20 oz ceramic Mug with color glazed logo. Made in America. Check out our new tapered, sleek AFIO coffee mug!! This handsome 20 oz. ceramic mug is made in the USA, has a white matte exterior, sports a beautiful navy-blue interior, and is dishwasher safe. Order yours today! $35 per mug includes shipping to a CONUS address. [includes shipping to U.S. based address, only. For foreign shipments, we will contact you with a quote.] SHIPPING: For shipment to a U.S.-based CONUS address, shipping is included in price. For purchases going to AK, HI, other US territories, Canada, or other foreign countries the shipping fees need to be calculated, so please call our office M-F 8 a.m. to 2 p.m. ET at 703-790-0320 or email afio@afio.com providing following information: 1) your name, 2) mailing address (or addresses where each gift item will be shipped), 3) name of the AFIO store items you wish to purchase, 4) quantity of each, 5) your credit card number and expiration date, 6) amount (except for additional of shipping fees) authorized to charge, and 7) your phone number and email should we have questions. Foreign shipments fees will be calculated and estimates emailed to you, awaiting your approval. Order this and other store items online here.
 Black short-sleeved polo shirts with Embroidered AFIO logo
Black short-sleeved polo shirts with Embroidered AFIO logo
Show your support for AFIO with our new Black Short-sleeve Polo Shirts. Shirts are shrink and wrinkle resistant of fine cotton with a soft, "well-worn, comfy" yet substantial feel. They feature a detailed embroidered AFIO seal. Get a shirt for yourself and consider as gifts for colleagues, family, and friends. Only $50 each including shipping.
Sizes for (M) men, only; Small, Medium, Large, XL, XXL, and XXXL. $50 per shirt.
You may pay by check or credit card. Complete your order online here or mail an order along with payment to: AFIO, 7600 Leesburg Pike, Ste 470 East, Falls Church, VA 22043-2004. Phone orders at 703-790-0320. Questions? Contact Annette at: annettej@afio.com.

PopSocket for cellphones or tablets
Show your support to AFIO while enjoying the convenience offered by our AFIO Logo PopSocket. The PopSocket is most commonly used as a stand and as a grip for your mobile phone or tablet; handy for taking selfies, watching videos, and for texting. The PopSocket looks like a small button or sticker which, when closed, sticks flat to your mobile device. However, its accordion-like design enables it to pop open for use. The benefits of using a PopSocket make it a must-have accessory for your mobile phone or tablet. It also aids in keeping your phone from slipping off your hand during use, falling, or breaking.
Price: $15. Order this and other store items online here.

Duffel Bags - Royal Blue and Black with Full Color AFIO Logo This duffel has it all when it comes to value, style and organization.
600 denier polyester canvas with polyester double contrast; D-shaped zippered entry for easy access. Front pocket with hook and loop closure. End mesh pocket Easy-access end pockets. Four durable, protective feet and built-in bottom board for added strength. Web handles with padded grip. Detachable, adjustable shoulder strap.
Dimensions: 11"h x 19.75"w x 9.75"d; Approx. 2,118 cubic inches
Price: $50. Order this and other store items online here.

Caps - Dark Navy with Navy AFIO Logo
An authentic silhouette with the comfort of an unstructured, adjustable fit. Fabric: 100% cotton. Unstructured. Fabric strap closure with adjustable D-clip. Price: $30. Order this and other store items online here.
 AFIO's Guide to the Study of Intelligence...and...When Intelligence Made a Difference
AFIO's Guide to the Study of Intelligence...and...When Intelligence Made a Difference
"AFIO's Guide to the AFIO's Guide to the Study of Intelligence has sold out in hard-copy.
It is available in digital form in its entirety on the
AFIO website here.
Also available on the website here are the individual articles of AFIO's
history project "When Intelligence Made a Difference" that have been
published to date in The Intelligencer journal.
PUBLISHED IN 2023—Be informed on career opportunities in the U.S. Intelligence Community
 Intelligence as a Career - with updated listings of colleges teaching intelligence courses, and Q&As on needed foreign languages, as well as the courses, grades, extracurricular activities, and behavioral characteristics and life experiences sought by modern U.S. intelligence agencies.
Intelligence as a Career - with updated listings of colleges teaching intelligence courses, and Q&As on needed foreign languages, as well as the courses, grades, extracurricular activities, and behavioral characteristics and life experiences sought by modern U.S. intelligence agencies.
AFIO's popular 47-page booklet reaches thousands of high school, college students, university guidance offices, and distributed in classes teaching intelligence, to help those considering careers
in the U.S. Intelligence Community.
This is the fifth edition.
The publication is also popular with University Career Guidance Centers, professors and academic departments specializing in national security, and parents assisting children or grandchildren in choosing meaningful, public service careers.
This booklet is provided online as a public service from the generosity of AFIO board, volunteer editors/writers, donors, and members.
We thank all for their support which makes this educational effort possible.
Careers Booklet (2023 Fifth Edition) can be read or downloaded here
To unsubscribe from the WIN email list, please click the "UNSUBSCRIBE" link at the bottom of the email. If you did not subscribe to the WIN and are not a member, you received this product from a third party in violation of AFIO policy. Please forward to afio@afio.com the entire message that you received and we will remove the sender from our membership and distribution lists.
(c) 1998 thru 2025
AFIO Members Support the AFIO Mission - sponsor new members! CHECK THE AFIO WEBSITE at www.afio.com for back issues of the WINs, information about AFIO, conference agenda and registrations materials, and membership applications and much more!
AFIO | 220 Spring St Suite 220, Herndon, Virginia 20170-6205 | (703) 790-0320 (phone) | (703) 991-1278 (fax) | afio@afio.com
